-
Posts
5,501 -
Joined
-
Last visited
Content Type
Events
Profiles
Forums
Posts posted by ShyWriter
-
-
.
Non-US Cards Used At Target Fetch Premium
An underground service that is selling millions of credit and debit card accounts stolen in a recent data breach at retail giant Target has stocked its virtual shelves with a new product: Hundreds of thousands of cards issued by non-U.S. banks that were used at Target across the United States during the retailer’s 19-day data breach. It’s not clear how quickly the non-U.S. cards are selling, but they seem to be fetching a much higher price than those issued by U.S. banks.
On Dec. 20, this blog published a story about the “card shop” rescator[dot]la. That piece explained how two different banks — a small, community bank and a large, top-10 bank — had bought back their customers’ stolen cards from the fraud service and discovered that all of the purchased cards had been used at Target during the breach timeframe. The shop was selling data stolen from the magnetic stripe of each card, which thieves can re-encode onto new, counterfeit cards and use to go shopping in bricks-and-mortar stores for items than can easily be fenced or resold.
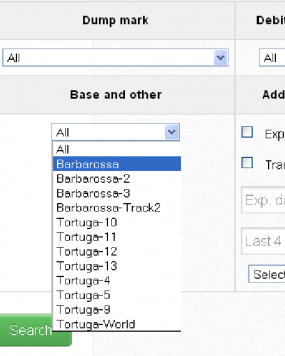
As I wrote in that story, a key feature of this particular shop is that each card is assigned to a particular “base.” This term is underground slang that refers to an arbitrary code word chosen to describe all of the cards stolen from a specific merchant. In this case, my source at the big bank had said all of the cards his team purchased from this card shop that matched Target’s N0v. 27 – Dec. 15 breach window bore the base name Tortuga, which is Spanish for “tortoise” or “turtle” (also an island in the Caribbean long associated with pirates). The small bank similarly found that all of the cards it purchased from the card shop also bore the Tortuga base name, and all had been used at Target.
Cards stolen from non-US customers who shopped at Target are sold under the “Barbarossa” base.
On Friday, the proprietor of this card shop announced the availability of a new base — “Barbarossa” — which consists of more than 330,000 debit and credit cards issued by banks in Europe, Asia, Latin America and Canada [side note: one Russian expert I spoke with said Barbarossa was probably a reference to Operation Barbarossa, the code name for Germany's invasion of the Soviet Union during World War II].
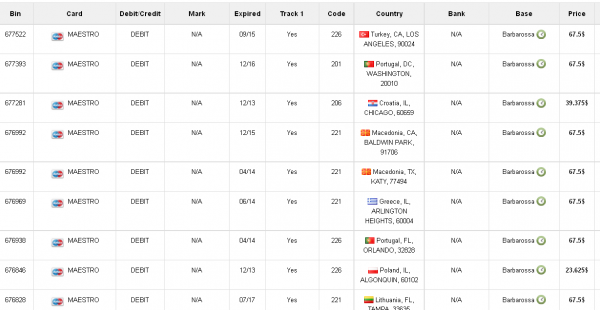
According to one large bank in the U.S. that purchased a sampling of cards across several countries — all of the cards in the Barbarossa base also were used at Target during the breach timeframe.
As with cards sold under the Tortuga base, debit and credit cards for sale as part of the Barbarossa base list the country of origin for the issuing bank, and then directly underneath include the state, city and ZIP code of the Target store from which the card numbers were stolen.
When I first became aware that this card shop was selling only cards stolen from Target stores, I noticed a discussion on a related crime forum wherein customers of this shop seemed very enthusiastic about this ZIP code feature. I couldn’t figure out what the big deal was: I’d assumed the state, city and ZIP described the bank that issued the card.
Later, I learned from a fraud expert that this feature is included because it allows customers of the shop to buy cards issued to cardholders that live nearby. This lets crooks who want to use the cards for in-store fraud avoid any knee-jerk fraud defenses in which a financial institution might block transactions that occur outside the legitimate cardholder’s immediate geographic region.
Non-U.S. cards used at Target generally fetch higher prices than U.S. cards, between $67 and $100 apiece.
The cards for sale in the Barbarossa base vary widely in price from $23.62 per card to as high as $135 per card. The prices seem to be influenced by a number of factors, including the issuing bank, the type of card (debit or credit), how soon the card expires, and whether the card bears a special notation that often indicates a higher credit limit, such as a Platinum card.
Continue reading →
SOURCE: https://krebsonsecurity.com/2013/12/non-us-cards-used-at-target-fetch-premium//Steve
-
Wishing you and yours a happy, healthy and fun festive season,
Hope you are feeling/doing better John.
Happy Holidays and the very best to you, and yours,
your instigating sidekick,
Steve

-
.
Target data stolen in hack showing up on black market
After 40 million accounts were compromised in a nationwide hack of the retail giant, fraud experts are seeing a "ten- to twentyfold increase" in high-value stolen cards on underground card-selling markets.
 (Credit: Target)
(Credit: Target)As if the Target hack ordeal couldn't get any worse -- data from the retail chain's massive security breach stolen between November 27 and December 15 is popping up in huge quantities on the black market, The New York Times reported Friday.
After Target conceded Thursday that its in-store point-of-sale systems were indeed hacked, compromising as many as 40 million debit and credit card accounts, fraud industry experts are seeing the information flood online card-selling markets to the tune of a "ten- to twentyfold increase" in high-value cards.
The hack, which affected only shoppers who made purchases physically at Target stores and not online customers, was a sophisticated operation. It allowed the hackers to glean customer names, credit and debit card numbers, expiration dates, and three-digit security codes from customers, data that can then be burned onto counterfeit cards and sold on the black market typically for $20 to $45 apiece.
However, Brian Krebs, the security blogger who broke the story of the breach, reported Friday that batches of up to 1 million cards were selling for anywhere from $20 to as high as $100 per card.
Related posts- Target hack hits 40M accounts
- Target: Hack may have hit 40 million accounts
- Target investigating massive Black Friday data breach: report
Target CEO Gregg Steinhafel released a statement assuring customers that no one will be held responsible for fraudulent charges and that only a few instances of fraud had since been reported. That echoes a sentiment by Visa yesterday in a statement to CNET in which a company spokesperson said, "Because of advanced fraud-monitoring capabilities, the incidence of fraud involving compromised accounts is actually rare, and Visa fraud rates remain near historic lows."
Steinhafel also said that no PINs had been compromised, a grave concern for those potentially affected as compromised PINs would allow one in possession of a counterfeit card to withdraw cash from an ATM. He added that Target had no reason to believe that customers' Social Security numbers or dates of birth were scooped up in the hack.
Target expects to have notified all 40 million of those affected via e-mail by the end of the weekend. In an attempt to save itself for what will inevitably be a disastrous hit to its holiday sales, Steinhafel also announced a promotion:
We're in this together, and in that spirit, we are extending a 10% discount -- the same amount our team members receive -- to guests who shop in US stores on Dec. 21 and 22. Again, we recognize this issue has been confusing and disruptive during an already busy holiday season. We want to emphasize that the issue has been addressed and let guests know they can shop with confidence at their local Target storesUpdate at 8:45 a.m. PT on December 21: Target is also claiming that only data from a card's magnetic strip has been breached, meaning no three- or four-digit security codes that enable one to make online purchases were compromised in the hack..
/Steve
-
.
Rumor: Winamp might not shut down after all on Friday

A month ago, it was announced that Winamp, one of the first PC software media players, would no longer be supported or made available for download by its owner AOL. Its last day is supposed to be on Friday, December 20th but now a new rumor claims that Winamp may be sticking around for at least a little while longer.
TechCrunch reports, via an unnamed source, that AOL is in talks with a potential buyer of Winamp and its Shoutcast streaming audio service. The article's source claims that it is "confident” that a deal can be made and that because the talks are so close to being completed, they don't believe that Winamp or Shoutcast will shut down on Friday as originally announced. For its part, AOL has not offered an official comment on any such talks.
TechCrunch previously reported that Microsoft might be in talks to acquire Winamp but so far the company has yet to confirm any interest in purchasing the rights from AOL. There's also a grass roots movement to ask AOL to turn Winamp over to the open source software community. An online petition for such a plan has now generated over 46,000 signatures as of this writing.
Source: TechCrunch | Image via AOL
http://www.neowin.net/news/rumor-winamp-might-not-shut-down-after-all-on-friday
/Steve
-
[...]
I no longer use my debit card for anything except ATM cash withdraws at their bank if needed. All transactions are now by credit card and I simply pay that off if I would have been using a debit card originally for the purchase.
[...]
Ron (and others);
Band of America, without notice or customer input) changed their ATM cards to a multiple-use ATM/Debit card years ago.. Needless to say, this irritated me to no end for the reason Ron mentioned; a debit card can drain your account with questionable recovery of funds lost.
I simply went to BofA and said this wasn't acceptable and I wanted an ATM-only card once again. With no argument or hassle, BofA provided me with one. Anybody else with a dual-use card should be able to make a similar request from their banking institution.
Just an FYI,
Steve
-
.
An early Christmas/Ect present from AVG..
AVG Technologies has launched a new app to block retailers from accessing smartphones and ensure consumers have an enjoyable experience in stores and shopping centres.
The WiFi Do Not Track feature within the AVG PrivacyFix for Android suspends WiFi on a user’s phone when they’re out and about, only reconnecting when they’re close to trusted WiFi locations like their home, office or favourite coffee shop.Steve
-
.
@FFGot'cha.. and you're right. I had already done a download and installed OVER my older copy of VLC so when I went to try UPDATE, I didn't have the same set of conditions; i.e., actually doing an version update.. I gots to get my glasses fixed or start using a 24 point font whilst reading the posts. (I don't know which is blinder; @DD or @Me
 )
)Steve
-
ShyWriter it does not cause a block or error when you download and install a fresh copy, or download and install over an existing version. You can even check for updates without a problem.
The issue occurs if there is an update available and you download the update through VLC and then attempt to install the update as mentioned in my post HERE
Apologies @FF; MY response was to the original Topic starter "Tom982" and I was advising him that he was using an outdated version of MBAE (0.09.3.1000) - I should have been clearer in MY post that I was asking him if the problem still occurred with the newest version of MBAE (0.09.4.2000) which has been released for some time now...
Sorry for the misunderstanding.

Steve
-
I have quite a few legacy apps in my XP system. They are there because they are very useful. Rather Office (18)97 than Office 2007 or later. I only wish that there were an Office (17)97.

They do; it's called Microsoft Works.



*sigh* Remember when OEM installed OSes actually came with included, ACTIVATED, versions of Office and such?? I use LibreOffice now..
Cheers,
Steve
EDIT: Hmmm.. I found my WordPerfect 3.5 diskettes and my DOS 6.0 3.5 diskettes.. It's like a trip through time altho' the wife made me dump all my Apple/IBM 1980s software (and hardware) when I retired.. *sigh* I had THREE Apples; a ][, a ][+ and a //e and associated peripherals including a ZipChip 8.. Have you seen auction prices lately??



-
As an aside, I have found that Office 97, that's 1897 I think :-) , is not recognised by MBAE.
Just between you and me I think Windows98/ME barely recognized M$OFFICE 97..

Sorry; couldn't resist as I still have my M$OFFICE 97 software in my collection right next to ENCARTA 98 .


Steve
-
If you select the option to show "updates" in your Add/Remove it should show IE 11 as an option to uninstall. It should then go back to IE 10 for you.
On Windows 8.1 though they say that it cannot be uninstalled and is part of the Windows 8.1 update.
More people should be screaming about this forced MSIE 11 "update" that doesn't work (and can't be removed/downgraded) on half the sites and less about the darned START button being missing.
IMHO, YMMV,
Steve
-
.
Microsoft bets on Windows XP disaster
Makes obvious prediction -- since it's calling the shots -- that ending support for XP will mean 'more systems will get compromised'By Gregg Keizer
December 12, 2013 04:17 PM ET
Computerworld - Microsoft today used the hoary practice of predicting next year to drive another nail into Windows XP's coffin.In an eight-item prognostication from several security professionals on its anti-malware and Trustworthy Computing teams, Microsoft forecast an increase in cybercrime that exploits unsupported software.
Microsoft's No. 6 prediction put the spotlight, and the onus, on Windows XP.
"This venerable platform, built last century, will not be able to keep pace with attackers, and more Windows XP-based systems will get compromised," prophesied Tim Rains, director of Trustworthy Computing, in a long post to Microsoft's security blog on Thursday.
Windows XP isn't quite "last century," at least to users; it may be old, very old in OS terms, but it wasn't released until September 2001.
Still, it is creaky, as any 12-year-old operating system would be. (By comparison, the same-aged Mac operating system would be OS X 10.1, aka Puma, a long-dead OS that required just 128MB of system memory; ran on the long-deserted PowerPC processors co-designed by Apple, IBM and Motorola; and was handed out as a free upgrade from OS X 10.0, or Cheetah.)
Microsoft has set Windows XP's end-of-support party for April 8, 2014, less than four months from now, and has given absolutely no hint that it will backtrack from that schedule.
Even if the end of support kills -- or allows infections for -- millions of still-used PCs.
According to analytics vendor Net Applications, Windows XP powered 34% of all Windows PCs last month. And with a two-month stall in decline, it now appears inevitable that the antique OS will be running more than one in every four PCs come April.
"The most effective way to protect systems in the current environment, where drive-by download attacks are so popular with attackers, is to keep all software installed on them up-to-date with security updates," said Rains.
True. But easier said than done.Nor was Microsoft's 2014 prediction a trip to the ledge's edge: Rains has rained on Windows XP's parade before. In October, he extrapolated data on PC infection rates to conclude that XP users will face a dramatic uptick, perhaps a hike by two-thirds, in attacks after April 8 because patches won't be provided to the public.
And like some predictions, Rains' was self-fulfilling. Microsoft is, after all, the one pulling the plug on users. Users aren't abandoning XP, at least not in numbers large enough to suit Microsoft.
But most outsiders don't see Microsoft letting this prediction fall flat: Even analysts who once believed the company might be forced by events to continue patching have retracted those statements as Microsoft has failed to breathe a word of any last-minute lifeline.
If a bookie will take Rains' bet, put down some money. It's as certain as the sun coming up tomorrow..
SOURCE: https://www.computerworld.com/s/article/9244757/Microsoft_bets_on_Windows_XP_disaster
Steve
-
You are using an outdated version (0.09.3.1000) of MBAE as well.
The updated version of MBAE is 0.09.4.2000 which has been released since 10/30/2013.
https://forums.malwarebytes.org/index.php?showtopic=119273&p=764040
You are also using an outdated version of VLC. VLC has been updated to 2.1.2 for both 32- and 64-bit systems for WinXP-SP2 up through Win8.1 since 12/10/2013
https://forums.malwarebytes.org/index.php?showtopic=106409&p=764080
I just download and installed (with no errors) VLC 64-bit on my MBAE 0.09.4.2000, Win8.1 machine without error. (Also, downloaded and installed the 32-bit version - no errors.) Also no problem checking for update(s)
Cheers,
Steve
-
.
Meet NASA's Valkyrie: A SILKY BUSTY ROBO-MINX that'll save your life
Space agency thinks with its Johnson, builds Iron (wo)Man for Mars colonyBy Iain Thomson, 11th December 2013Video NASA's Johnson Space Center (JSC) has revealed its entry into the $2m DARPA Robotics Challenge, which will start later this month. The result is a robot dubbed Valkyrie that's designed to look like a sexy superhero.

'My eyes are up here, thank you'
The 1.9-metre tall, 125kg droid has interchangeable arms that can be swapped out by removing a single bolt and connector, and three fingers and a thumb on each hand that exceed a human's in strength. It also has an impressive cleavage, thanks to the linear actuators that allow it to swivel, and a glowing NASA icon that looks straight out of Iron Man.
The bipedal robot is built to operate under human control and uses head-mounted stereoscopic cameras and laser range-finding equipment to help its operators find where it's going. A sonar system is also built into the torso, and the robot carries its own hot-swappable two kilowatt-hour battery backpack that's good for 60 minutes of operation.

'Sarah Connor?'
Val, as the robot is known to its builders, will compete for a $2m cash prize from the US military's research and development laboratory in its Robotics Challenge: the goal is to create a robot that can operate in environments built for humans, and conduct search and rescue missions where we fleshy mortals can't safely go. (More...)
Read much more on this at: http://www.theregister.co.uk/2013/12/11/nasa_unveils_valkyrie_the_shapely_robot_that_could_save_your_life/
Steve
-
.
ADOBE FLASH AND SHOCKWAVE UPDATES
Adobe has issued a patch for its Flash Player software that addresses at least two security holes, including a vulnerability that is already under active attack. Adobe said it is aware of reports of an exploit designed to trick the user into opening a Microsoft Word document with malicious Flash (.swf) content. The company credits researcher Attila Suszter for reporting the flaw; more information about this bug is available at Suszter’s blog.
To find out whether your system has Flash installed and at what version, check this page. Updates are available for Windows, Mac and Linux versions of Flash. The latest version for Windows and Mac users is 11.9.900.170, and 11.2.202.332 for Linux.
Google Chrome auto-updates its own versions of Flash (although not always right away); the newest Flash for Chrome is 11.9.900.170. Internet Explorer 10 and 11 on Windows 8 include an embedded version of Flash that gets updates from Windows Update, rather than through Adobe’s installer. On Windows 7 and earlier, Flash is not embedded, and needs ot be updated via Adobe’s updater or manually by downloading the appropriate version from this page.
In addition, Adode AIR (required by some applications like Pandora Desktop, for example) was updated to v. 3.9.1380 for Windows, Mac and Android devices. Adobe AIR checks for and prompts you to install any available updates anytime you launch an application that uses AIR; in any case, the download link is here.
Adobe also issued an update for its Shockwave Player software that fixes at least two vulnerabilities, bringing Shockwave to v. 12.0.7.148 on Windows and Mac systems. Shockwave is one of those programs that I’ve urged readers to remove or avoid installing. Like Java, it is very often buggy software that many people have installed but do not really need for everyday Web browsing. Securing your system means not only making sure things are locked down, but removing unneeded programs, and Shockwave is near the top of my list on that front.
If you visit this link and see a short animation, it should tell you which version of Shockwave you have installed. If it prompts you to download Shockwave, then you don’t have Shockwave installed and in all likelihood don’t need it. Firefox users should note that the presence of the Shockwave Flash plugin listed in the Firefox Add-ons section denotes an installation of Adobe Flash Player plugin — not Adobe Shockwave.
SOURCE: https://krebsonsecurity.com/2013/12/zero-day-fixes-from-adobe-microsoft/
/Steve
-
.
Microsoft's Patch Tuesday reinforces the value of software upgrades
Microsoft has issued five critical security bulletins in December's round of Patch TuesdayBy Joab Jackson
December 10, 2013 04:49 PM ET
IDG News Service - The latest round of monthly patches from Microsoft illustrates the need for organizations to move from older versions of Microsoft software if they haven't done so already."The load of the risk is on older software versions," said Wolfgang Kandek, chief technology officer for security firm Qualys, about this round of Microsoft software patches.
Overall, Microsoft's Patch Tuesday for December addressed a total of 24 vulnerabilities with 11 security bulletins. The bulletins cover Microsoft Windows, Office, Internet Explorer, Exchange, Office365, Visual Studio, and SharePoint.
Microsoft rated five of these bulletins as critical, meaning that the patches they contain should be applied as soon as possible.
Perhaps the set of critical patches that should be applied first is MS13-096, which addresses a vulnerability in Microsoft's GDI+ library for parsing TIFF image files. It is already being exploited by attackers.
The vulnerability affects mainly older Microsoft software, including Windows Vista, Office 2003, Office 2007 and Office 2010. It is already being used in targeted attacks in the Middle East and Asia.
Kandek noted that newer software tends to have fewer vulnerabilities than older software. "The newer software versions just have more security features. Windows 8.1 has more security features that Windows 8 which has more than Windows 7, which has many more than Windows XP," he said.
"Even if you are fully patched with Windows XP, you are running more of a risk than with a fully patched Windows 7 installation," Kandek said.
As an example, Kandek noted there has another zero-day vulnerability in the Windows XP kernel that this month's patch cycle has not addressed. A zero day vulnerability means that exploits have already been crafted that take advantage of a software flaw. In this case, an attacker can send the user a maliciously crafted PDF file that, when opened, can deposit code in the computer's memory that grants another user administrative access.
Microsoft offers a work-around for this problem.
Qualys estimated that 15 percent of enterprise users are still running Windows XP. Though the percentage of XP users is rapidly declining, Kandek doubted that everyone will be off the OS by April 2014, when Microsoft will cease issuing security patches for Windows XP. "After April, these machines will be very quickly be easy targets," Kandek said.
Another critical set of patches come under the security bulletin MS13-097, which affects Internet Explorer. The bulletin indicated that these vulnerabilities are easy to exploit, such as by using a maliciously crafted webpage.
The third critical bulletin, MS13-105 addresses a number of flaws in Outlook Web Access that an attacker could use to gain access to Microsoft Exchange server by tricking the user into opening a documents with embedded malicious code.
1 of a 2-page article
2
Next pageSOURCE: https://www.computerworld.com/s/article/9244691
/Steve
-
.

It wasn't that "huge" - really.
THAT'S what SHE said!



Really...
Yep, it wasn't nearly as "huge" as billed.
Some people have naughty minds on here.. I *know* what some of you were thinking about MY, "That's what she said." statement *wry grin*
Sorry DD; just teasing and the two posts in a row was too good for me to pass up.
I sorry
 :(
:(And thanks to @Amethyst and @DD for the kinds words about my easy update after all last week's misery.. Speaking of my misery, I'll pass along some advice @Maurice gave me.. and which he was kind enough to mail me a loaner. Everyone should make a 512MB flash stick with the "RECOVERY" tools on it. Do a SEARCH in Win8.1 on RECOVERY, read, and when you get to the part that says "You need at least a 32GB flash stick." say "No" and then it gives the option of the 512MB stick tool.
And... believe it or not.. I have my Win8.1 boot directly into "Desktop" mode and also bypassing the "password/logon" screen and after my time with 8.1 I can honestly say, "It's a piece of cake.. Different maybe but really just as easy to learn and use as Vista and Win7.. " And THAT statement *wasn't* a tease or a joke..

Good luck with your updates Amethyst... and DD I feel your pain as I just learned yesterday of all the Adobe updates and not only had to install them but I had to post the updates in the SOFTWARE Forums including the Adobe Beta ones from the 3rd I missed..
 ..
..Cheers
Steve
-
Can't speak for other people's problems but my updates were installed all in one bunch and required one restart and total time from update start to useable machine was about 23 minutes.:

Hope everyone else gets theirs working...
Steve
-
Amen..
[...]
i'll say this much for FF ... at least one does not have to wait for hell to freeze over before *something* is fixed ...
kind of like old man ford holding out on doing away with his directly actuated mechanical brakes .
[...]
I don't care how many problems a product has as long as they are being fixed almost instantly.

Steve
-
You guys (and gal).. You're too literal. FF26 was released 12 hours earlier than scheduled and had gone through many, MANY betas (which I don't post..) which is why I said it was released early - it wasn't supposed to be released until the 10th but with all the M$ updates coming I guess they decided to give everyone a chance to get FF26 installed and working before having to deal with the M$ 2nd Tuesday Update cycle.
Now; the real mystery is why the AEON theme author NEVER releases a compatible theme with the newest FF until a day or two afterwards.?
Steve
-
-
I had a train like that once.. *sigh* Pullman sleeping cars; REAL dining cars with linens and real china plateware AND real silverware.. AND real chefs..
HEY! Where did you find my Hopalong Cassidy lunchbox.. Those contents, a moon pie and an RC cola.. That's the life!

And MY Apple ][ had TWO floppy drives..

Steve
-
.

Microsoft's last Patch Tuesday of 2013 will be huge
Tim Greene- Dec 7, 2013 11:04 AM
Microsoft is wrapping up the year’s Patch Tuesday bulletins next week with 11 more fixes, pushing the total for 2013 to 106, up from last year’s total of 83.
Five bulletins ranked critical all hold the potential for enabling remote code execution on victimized machines and affect a wide range of platforms including most versions of Windows, Windows Server, Internet Explorer, SharePoint and Exchange.
The patches will include a remedy for the .TIFF zero day vulnerability, a flaw in Microsoft Graphics that leaves Microsoft Office and Lync apps and Windows open to attack. Common exploits of the vulnerability include a Word file containing a malicious .TIFF image that leads to the attacker gaining control of the machine with current user rights.
“In this vulnerability, an attacker needs to convince a user to preview or open a bad TIFF image for exploitation,” says Paul Henry, a forensics and security analyst for Lumension. “Because we know persuading users to click isn’t always that hard to do, a patch for this one is definitely welcome.”The problem and exploits in the wild were discovered last month, but Microsoft didn’t deem it worth an out-of-band fix.
Restarts requiredAll the critical bulletins save one require restarts, so scheduling the patches will be a chore. “Be careful and have a rollback plan in case the patches break your custom environment,” says Tommy Chin, a technical support engineer for CORE Security.
Another critical bulletin this month addresses a vulnerability in all versions of Internet Explorer from 6 through 11.“It is best to patch the ones that require restart quickly, since the vulnerable code is already loaded in those scenarios,” says Chin. “Definitely patch Windows and Internet Explorer first.”
A bulletin affecting Microsoft Exchange does not require a restart but warrants attention, says Qualys CTO Wolfgang Kandek. “Bulletin #5 is a server-side bulletin for Microsoft Exchange and will probably include the new Outside In library from Oracle that was released during October’s Critical Patch Update,” he says, referencing an Oracle update that included fixes for middleware in Outside In Technology, versions 8.4.0, 8.4.1. Outside In provides tools to access and control content in unstructured file formats.
One of the less severe bulletins, ranked important, should still be a high priority, says Kandek. “Bulletin #6 is for Microsoft Office and is only rated important, but it will still deserve your full attention due to the Remote Code Execution possibilities, most likely through file format vulnerabilities,” he says.
A vulnerability in Windows XP discovered last week is not being addressed in this wave of patches. “This is perhaps another reminder that end of life is now just four months out for Windows XP and users still running it should move to a current generation operating system sooner rather than later,” Henry says.
SOURCE: http://www.pcworld.com/article/2070661/microsofts-last-patch-tuesday-of-2013-will-be-huge.html
/Steve
-
.
Internet Explorer 11 at it again, breaks Microsoft's own CRM software
Customers advised to use old version ... or another browserBy Neil McAllister, 6th December 2013
Compatibility problems continue to plague Internet Explorer 11, with some Microsoft customers once again complaining that the company's latest browser doesn't work with one of its own products.
Users first raised red flags about IE11 in October, when reports surfaced that the browser was rendering a number of sites strangely, including several Google properties and Microsoft's own Outlook.com.
Microsoft apparently released a fix for those problems – although exactly why the issues cropped up to begin with is not entirely clear – but now Redmond's latest and greatest browser seems to be at it again. And as before, it's a Microsoft product that's taking the hit.
On Thursday, Microsoft service engineer Daria Barteneva blogged that customers of Microsoft Dynamics CRM Online are having problems running the initial configuration of new CRM Online instances, including free trials.
Barteneva posted a workaround for the problem, but it won't be much of a comfort for affected customers:
Log in to MOP from a machine with an older IE version (IE10 for example) and rerun the configuration from there OR use compatibility view.Compatibility View is Microsoft's name for the mode that makes the latest version of Internet Explorer behave as if it's an earlier version, complete with that version's rendering quirks and web standards incompatibilities.
Accompanying Barteneva's terse blog post, Microsoft's support organization has also published an updated document listing the browser compatibility for Dynamics CRM. In it, the latest supported version of Internet Explorer is listed as IE10. What's more, only the desktop version of IE10 is supported – the touch-enabled version for the Windows 8 Start Screen won't work.
All of this will be a bummer for anyone who upgraded to Windows 8.1, because IE11 was included as part of the upgrade and there's no way to roll back to the previous version once you're running Redmond's latest OS. Switching to Compatibility View or finding another machine to run the setup will be these customers' only options (that is, assuming they're still not ready to switch to a different browser).
More importantly, however, it's a bummer for Microsoft's Internet Explorer team, which has been touting IE11 as its best-performing and most standards-compliant browser to date. By comparison, the Dynamics CRM browser compatibility document lists the supported versions of Firefox, Chrome, and Safari simply as "Latest Version", without restrictions.
Microsoft has yet to say when and if it plans to release a patch for either IE11 or Dynamics CRM that will improve compatibility between the two products. ®
SOURCE: http://www.theregister.co.uk/2013/12/06/ie11_breaks_dynamics_crm_online/
/Steve




Target shoppers' credit card info stolen over Black Friday
in General Chat
Posted
Amen.. FDIC is to protect the customer against bank FAILURE (at the limits per account Ron mentioned,) nothing more; nothing less..
Steve