-
Posts
5,501 -
Joined
-
Last visited
Content Type
Events
Profiles
Forums
Posts posted by ShyWriter
-
-
.
Krebs on Security has posted a new item.
Until today, Microsoft Windows users who've been unfortunate enough to have the personal files on their computer encrypted and held for ransom by a nasty strain of malware called CryptoLocker have been faced with a tough choice: Pay cybercrooks a ransom of a few hundred to several thousand dollars to unlock the files, or kiss those files goodbye forever.That changed this morning, when two security firms teamed up to launch a free new online service that can help victims unlock and recover files scrambled by the malware.
Read the complete article at:
http://krebsonsecurity.com/2014/08/new-site-recovers-files-locked-by-cryptolocker-ransomware/
Steve (w/thanks to Samuel..)
-
Maverick was always my favorite..
-
.
Microsoft releases test patch to address Windows 8.1 update woes
But some will say it's still not a patch on Windows 7
By Chris Merriman
Wed Jul 02 2014, 16:55
MICROSOFT HAS RELEASED a patch to address issues for users who have had problems updating their machines to Windows 8.1.The patch, which is still in testing, fixes an issue that caused a Blue Screen of Death (BSOD) error for some users of Windows 8 and Windows RT when attempting to upgrade to Windows 8.1.
The problem has resulted in a slow migration process for Windows 8 users, with the latest figures from Net Applications showing that a significant number have not taken up the free upgrade that attempts to address many of the issues that users have had with the new Windows 8 user interface.
This is compounded by the fact that the original Windows 8 to Windows 8.1 upgrade was released via the Windows Store, rather than the traditional Windows Update service, alienating users who had never used the Windows Store.
Since Windows 8.1 was released a further update has been added, with another expected to follow in August, the last before Microsoft turns its attention to "Threshold", the codename for the next major Windows release. The company has also recently announced a "with Bing" edition of the operating system for low-end computers and tablets.
Anyone affected can download the patch from the Microsoft website, however it is a test patch and might not work for everyone. Also available is a hotfix that installs a notification to guide users through the update process. Windows RT users do not have access to Windows Update and can download from the Windows Store, but require a second hotfix.
/Steve
-
.
Cisco uncovers Microsoft Word spearphishing attack
Targeted rich industries like banking, oil, television and jewelry..By Lee BellTue Jul 01 2014, 13:44
CISCO HAS DISCOVERED spearphishing malware in Microsoft Word that uses an exploit targeting the software's Visual Basic Scripting for Applications feature.
Cisco's investigation into the malware identified a group of attacks by the same threat actor, with Cisco exposing the threat actor's network after it had discovered a Microsoft Word document that downloaded and executed a secondary sample, which began beaconing to a command and control server.
"While basic, the Office Macro attack vector is obviously still working quite effectively," Cisco technical lead Craig Williams said in a blog post. "When the victim opens the Word document, an On-Open macro fires, which results in downloading an executable and launching it on the victim's machine."Williams said that this threat actor seemed to target high-profile, rich industries such as banking, oil, television and jewellery companies and victims of the attacks were duped into opening an email attachment in the form of an invoice, written specifically for the recipient.
"The message [was] a fairly simple phish email which includes a fake name and an attached Microsoft Word document. However, this was simply the outer layer of the onion so it's best, we think, to start from the beginning," Williams said.
"This particular phishing attempt was noticed in Cisco's email corpus due to the email attachment's poor block rates at most antivirus engines."
"For the duration of this campaign there is one thing that remained consistent: at best, a few antivirus engines may have generically detected the attached malware but more often than not coverage was provided by a single vendor, or no coverage was provided at all."SOURCE: http://www.theinquirer.net/inquirer/news/2353015/cisco-uncovers-microsoft-word-spearphishing-attack
/Steve
-
.
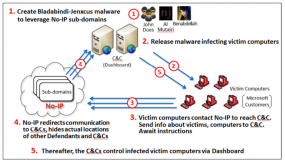
Microsoft Darkens 4MM Sites in Malware Fight
by Brian Krebs | July 1st, 2014
Millions of Web sites were shuttered Monday morning after Microsoft executed a legal sneak attack against a malware network thought to be responsible for more than 7.4 million infections of Windows PCs worldwide.
A diagram showing how crooks abused no-ip.com’s services to
control malware networks. Source: Microsoft.
In its latest bid to harness the power of the U.S. legal system to combat malicious software and cybercrooks, Microsoft convinced a Nevada court to grant the software giant authority over nearly two dozen domains belonging to no-ip.com, a company that provides dynamic domain name services.
Dynamic DNS services are used to map domain names to numeric Internet address that may change frequently. Typically, the biggest users of dynamic DNS services are home Internet users who wish to have a domain name that will always point back to their home computer, no matter how many times their ISP changes the numeric Internet address assigned to that computer.
In this case, however, the attackers responsible for leveraging these two malware families — remote-access Trojans known as “njrat” and “njw0rm” — were using no-ip.com’s services to guarantee that PCs infected with this malware would always be able to reach the Internet servers that the attackers were using to control them.
Microsoft told the court that miscreants who were using these two malware strains were leveraging more than 18,400 hostnames that belonged to no-ip.com. On June 26, the court granted Microsoft the authority to temporarily seize control over 23 domains owned by no-ip.com — essentially all of the domains that power no-ip.com’s free dynamic DNS services.
Microsoft was supposed to filter out the traffic flowing to and from those 18,400+ hostnames, and allow the remaining, harmless traffic to flow through to its rightful destination. But according to no-ip.com marketing manager Natalie Goguen, that’s not at all what happened.
“They made comments that they’d only taken down bad hostnames and were supposedly redirecting all good traffic through to users, but it’s not happening, and they’re not able to handle our traffic volumes,” Goguen said. “Many legitimate users that use our services have been down all day.”Goguen said while Microsoft claimed that there were more than 18,000 malicious hostnames involved, no-ip.com could only find a little more than 2,000 from that list that were still active as of Monday morning. Meanwhile, some four million hostnames remain offline, with customer support requests piling up.
“So, to go after 2,000 or so bad sites, [Microsoft] has taken down four million,” Goguen said.
/Steve
-
.
For Internet Explorer 11 users, no update now means no security fixes
Windows Update no longer offers patches for the original IE11 release.
by Peter Bright - June 16 2014, 3:40pm PST
When Microsoft released the Windows 8.1 Update, IT feathers were ruffled by Microsoft's decision to make it a compulsory update: without it, Windows 8.1 systems would no longer receive security fixes. As spotted by Computerworld's Gregg Keizer, Microsoft is applying the same rules, at least in part, to Windows 7.
Windows 7 users who've installed Internet Explorer 11 are required to install the KB2929437 update. This is the Internet Explorer 11 update that corresponds to the Windows 8.1 Update; it doesn't just include security fixes for Microsoft's browser. There are also some new and improved features, including a more capable WebGL implementation and some additional high performance JavaScript features. If users don't install the update, Windows Update will not provide any more security fixes for their browser.
For the next couple of months, Microsoft is actually still making security fixes for the original Internet Explorer 11 on Windows 7 release, but anyone who wants to use them will have to..(more...)
Read the complete article at: http://arstechnica.com/information-technology/2014/06/internet-explorer-11s-new-update-ethos-for-security-fixes-youll-need-new-features/
/Steve
-
.
Adobe, Microsoft Push Critical Security Fixes
by Brain Krebs | 10 june 2014
Adobe and Microsoft today each released updates to fix critical security vulnerabilities in their software. Adobe issued patches for Flash Player and AIR, while Microsoft’s Patch Tuesday batch includes seven update bundles to address a whopping 66 distinct security holes in Windows and related products.
The vast majority of the vulnerabilities addressed by Microsoft today are in Internet Explorer, the default browser on Windows machines. A single patch for IE this month (MS14-035) shores up at least 59 separate security issues scattered across virtually every supported version of IE. Other patches fix flaws in Microsoft Word, as well as other components of the Windows operating system itself.
Most of the vulnerabilities Microsoft fixed today earned its “critical” rating, meaning malware or bad guys could exploit the flaws to seize control over vulnerable systems without any help from users, save perhaps for having the Windows or IE user visit a hacked or booby-trapped Web site. For more details on the individual patches, see this roundup at the Microsoft Technet blog.
Adobe’s update for Flash Player fixes at least a half-dozen bugs in the widely-used browser plugin. The Flash update brings the media player to v. 14.0.0.125 on Windows and Mac systems, and v. 11.2.202.378 for Linux users. To see which version of Flash you have installed, check this link.
/Steve
-
Thanks DD.. I'll take a look. (I'd also forgotten about RUBICON) - I swear almost every darned program these networks get me hooked on don't get renewed. MAD MEN has 6 eps in the can for a 2015 showing but is one of those that HAS outlived itself.) USA has a couple of great ones like SUITS which was renewed and a few others..) NBC gets a BIGGGGGGGGGGGGGGGGG raspberry for cancelling REVOLUTION..
And I hate ALL of them for cancelling all the various lawyer shows (except SUITS), as well as TERRA NOVA (*snif*) and STARGATE-UNIVERSE (*Wahhhhhh*)
BLACKLISTED got renewed.. (high 5!!)
On and ON..
BUT; a reality show.. Singing with the Duds, etc, et al + BABY BOO-BOO.. Auto-renewal.. shows where the American IQ has dropped to these days.

Cheers,
Steve
-
.
HALT and CATCH FIRE on AMC.. Cable TV series about a 3-some designing a IBM compatible computer (early 1980s) that looks suspiciously like the Osbourne Executive (which ran CPM instead of M$ Basic) so 'tisn't it.. From the pilot I originally thought it was going to be a fictionized story about how COMPAQ came about *but* Compaq is already mentioned in a passing example (of beating IBM's patents) in the story and already exists.
- Halt and Catch Fire, known by the mnemonic HCF, refers to several computer machine code instructions that cause a computer's CPU to cease meaningful operation. The expression "catch fire" is intended as a joke; the CPU does not literally catch fire, but it does stop functioning. It is also occasionally referred to as "SDI" for "Self Destruct Immediate".
- One apocryphal story about the HCF instruction goes back to the late 1960s, when computers used magnetic core memory. The story goes that in order to speed up the core memory on their next model the engineers increased the read/write currents in the very fine wires that were threaded through the cores. This worked fine when the computer was executing normal programs, since memory accesses were spread throughout memory. However, the HALT instruction was implemented as a "Jump to self". This meant that the same core memory location was repeatedly accessed, and the very fine wires became so hot that they started to smoke — hence the instruction was labeled "Halt and Catch Fire"
/Steve
-
.
Not Too Late
Beautiful lyrics and voice
Norah Jones sings/plays
Scroll Credits Song in the romantic movie LAST LOVE
Steve
-
.
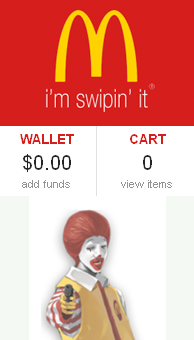
Peek Inside a Professional Carding Shop
by Brian Krebs | 4 June 2014
Over the past year, I’ve spent a great deal of time trolling a variety of underground stores that sell “dumps” — street slang for stolen credit card data that buyers can use to counterfeit new cards and go shopping in big-box stores for high-dollar merchandise that can be resold quickly for cash. By way of explaining this bizarro world, this post takes the reader on a tour of a rather exclusive and professional dumps shop that caters to professional thieves, high-volume buyers and organized crime gangs.
The subject of this post is “McDumpals,” a leading dumps shop that first went online in late April 2013. Featuring the familiar golden arches and the bastardized logo, “i’m swipin’ it,” the site’s mascot is a gangstered-up Ronald McDonald pointing a handgun at the viewer.
Nevermind that this shop is violating a ridiculous number of McDonald’s trademarks in one fell swoop: It’s currently selling cards stolen from data breaches at main street stores in nearly every U.S. state.
Like many other dumps shops, McDumpals recently began requiring potential new customers to pay a deposit (~$100) via Bitcoin before being allowed to view the goods for sale. Also typical of most card shops, this store’s home page features the latest news about new batches of stolen cards that have just been added, as well as price reductions on older batches of cards that are less reliable as instruments of fraud.
I’ve put together a slideshow (below) that steps through many of the updates that have been added to this shop since its inception. One big takeaway from this slideshow is that many shops are now categorizing their goods for sale by the state or region of the victim company.
This was a major innovation that we saw prominently on display in the card shop that was principally responsible for selling cards stolen in the Target and Sally Beauty retail breaches: In those cases, buyers were offered the ability to search for cards by the city, state and ZIP of the Target and Sally Beauty stores from which those cards were stolen. Experienced carders (as buyers are called) know that banks will often flag transactions as suspicious if they take place outside of the legitimate cardholder’s regular geographic purchasing patterns, and so carders tend to favor cards stolen from consumers who live nearby.
The slideshow may make more sense if readers familiarize themselves with a few terms and phrases that show up in the text:
/Steve
-
.
Krebs on Security has posted a new item.
An article in The Wall Street Journal this week quoted executives from antivirus
pioneer Symantec uttering words that would have been industry heresy a few years
ago, declaring antivirus software "dead" and stating that the company is
focusing on developing technologies that attack online threats from a different
angle. This hardly comes as news for anyone in the security industry who's been
paying attention over the past few years, but I'm writing about it because this
is a great example of how the cybercrime underground responds to -- and in some
cases surpasses -- innovations put in place by the good guys.
http://krebsonsecurity.com/2014/05/antivirus-is-dead-long-live-antivirus/
Please use the link above to continue reading this posting. -- Brian Krebs/Steve
-
.
I've been updating the link in this forum for the past versions as well as 2.0.2.1010
The current Topic title is:
There is a new PUBLIC beta - 2.0.2.1010 - Available 5/05/2014
https://forums.malwarebytes.org/index.php?showtopic=148209&p=827419
People need to read..

-
I mentioned in a previous Topic that if one used FireFox with NoScript that boxcdn.net and box.net had to be allowed.
See https://forums.malwarebytes.org/index.php?showtopic=148209&p=827419 which I've re-posted twice to keep it up to date on build number. The pertinent excerpt:
You may download the new version from Box.com directly here. (EDIT: If using Firefox with NoScript, boxcdn.net and box.net must be "allowed".)Steve
EDIT: I disabled FLASH and was *still* able to download the file so evidently Flash is NOT required.
PS: BTW; How many accounts do you have on Malwarebytes??
-
Uninstalled broken version of MBAE with RevoUninstaller and cleaned up all the left-over junk. Installed MBAE as a regular user and everything is NOW OK..
Closed topic - And thanks to @DD for her assistance..
-
Check Known Issue #4 to see if it might have something to do.
Pedro,
See https://forums.malwarebytes.org/index.php?showtopic=148119&p=827051
TIA,
Steve
EDIT: I *did* try both installs as ADMIN; will try as a regular user this time.
-
Do you have MBAM v2 Self-Protection enabled???
[...]

Steve
-
.
Sorry.. Topic title is inaccurate - MBAE Protection is not started.is the problem.. Restarted.. no dice.. rebooted, same error.

Previous version worked fine. None of the known issues; conflicts apply.
??
Steve
-
.
Microsoft’s decision to patch Windows XP is a mistake
There will always be one more emergency.
by Peter Bright - May 1 2014, 5:15pm EST
Aurich LawsonMicrosoft officially ended support of the twelve-and-a-half-year-old Windows XP operating system a few weeks ago. Except it apparently didn't, because the company has included Windows XP in its off-cycle patch to fix an Internet Explorer zero-day that's receiving some amount of in-the-wild exploitation. The unsupported operating system is, in fact, being supported.
Explaining its actions, Microsoft says that this patch is an "exception" because of the "proximity to the end of support for Windows XP.The decision to release this patch is a mistake, and the rationale for doing so is inadequate.
A one-off patch of this kind makes no meaningful difference to the security of a platform. Internet Explorer received security patches in 11 of the last 12 Patch Tuesdays. Other browsers such as Chrome and Firefox receive security updates on a comparable frequency.
Web browsers are complex. They're necessarily exposed to all manner of potentially hostile input that the user can't really control, and as such, they're a frequent target for attacks. They need regular updates and ongoing maintenance. The security of a browser is not contingent on any one bugfix; it's dependent on a continuous delivery of patches, fixes, and improvements. One-off "exceptions" do not make Internet Explorer on Windows XP "safe." There's no sense in which this patch means that all of a sudden it's now "OK" to use Internet Explorer on Windows XP.
And yet it seems inevitable that this is precisely how it will be received. The job of migrating away from Windows XP just got a whole lot harder. I'm sure there are IT people around the world who are now having to argue with their purse-string-controlling bosses about this very issue. IT people who have had to impress on their superiors that they need the budget to upgrade from Windows XP because Microsoft won't ship patches for it any longer. Microsoft has made these IT people into liars. "You said we had to spend all this money because XP wasn't going to get patched any more. But it is!"
Bosses who were convinced that they could stick with Windows XP because Microsoft would blink are now vindicated.
After all, if Microsoft can blink once, who's to say it won't do so again? The next Patch Tuesday patch for Internet Explorer is almost certainly going to include flaws that affect Internet Explorer on Windows XP: the nature of software means that most flaws in Internet Explorer 7 (supported for the remainder of Windows Vista's life cycle) and Internet Explorer 8 (tied to Windows 7's life cycle) will also be flaws in Internet Explorer 7 and 8 when run on Windows XP. Many of them will also hit Internet Explorer 6.
In fact, this is precisely the pattern we've seen with this flaw. The first in-the-wild exploits hit only Internet Explorer 9, 10, and 11, on Windows 7 and 8. As security firm FireEye reports, it's only later that attacks for (unsupported) Internet Explorer 8 on Windows XP materialized.
Patch delay comes two months after previous lapse for critical "goto fail" fix.
Virtually every time Microsoft updates one of its remaining supported platforms, the company will also simultaneously be disclosing a zero-day vulnerability for Windows XP (something Apple has recently been criticized for doing). (More...)
Read the rest at: http://arstechnica.com/security/2014/05/microsofts-decision-to-patch-windows-xp-is-a-mistake
/Steve -
Is it possible the UAC box is being covered by the run box??
-
.
Krebs on Security has posted a new item.
Microsoft said that later today it will issue an emergency security update to
fix a zer0-day vulnerability that is present in all versions of its Internet
Explorer Web browser and that is actively being exploited.In an unexpected twist, the company says Windows XP users also will get the update, even though Microsoft officially ceased supporting XP last month. [...] (More...)
http://krebsonsecurity.com/2014/05/microsoft-issues-fix-for-ie-zero-day-includes-xp-users/
Please use the link above to continue reading this posting./Steve
-
.
Why must I pay a licence for 3 computers and only use it in two?
What do I do with the remaining one?
Why pay it every year for 3 and only use it for 2?
The same reason one buy a car that holds seven people but there are only two drivers in the family.. ?? AND, one still has to change the oil and rotate the tires at least annually if not sooner.
Cheers,
Steve
-
.
Adobe Update Nixes Flash Player Zero Day
by Brian Krebs | April 28, 2014
Adobe Systems Inc. has shipped an emergency security update to fix a critical flaw in its Flash Player software that is currently being exploited in active attacks. The exploits so far appear to target Microsoft Windows users, but updates also are available for Mac and Linux versions of Flash.
The Flash update brings the media player to v. 13.0.0.206 on Windows and Mac systems, and v. 11.2.202.356 for Linux users. To see which version of Flash you have installed, check this link.
IE10/IE11 and Chrome should auto-update their versions of Flash. If your version of Flash on Chrome (on either Windows, Mac or Linux) is not yet updated, you may just need to close and restart the browser.
The most recent versions of Flash are available from the Adobe download center, but beware potentially unwanted add-ons, like McAfee Security Scan). To avoid this, uncheck the pre-checked box before downloading, or grab your OS-specific Flash download from here. Windows users who browse the Web with anything other than Internet Explorer will need to apply this patch twice, once with IE and again using the alternative browser (Firefox, Opera, e.g.).
In its advisory about this vulnerability, Adobe said it is aware of reports that an exploit for the flaw (CVE-2014-0515) exists in the wild, and is being used to target Flash Player users on the Windows platform.
SOURCE: https://krebsonsecurity.com/2014/04/adobe-update-nixes-flash-player-zero-day/
/Steve
-
Unfortunately I have some network monitoring tools that use Java, I have it updated up to 7.51 then Java 8 came out. When I installed java 8 it borked my software, had to revert back to java 7.51
7u55 is out if you need to use version SEVEN... It fixes 37 bugs
Java SE 7u55 Downloads (Win, Mac & Linux) at;
http://www.oracle.com/technetwork/java/javase/downloads/jre7-downloads-1880261.html
REASON: You must accept the Oracle Binary Code License Agreement for Java SE to download this software.
Cheers
Steve


2.1.8.1057 MBAMPro on wife's computer.. 2.1.6.1022 on mine ?
in Malwarebytes for Windows Support Forum
Posted
MBAMPro just did an auto-update to 2.1.8.1057 on my wife's lifetime activated version on Win7.. My lifetime activated version on Win8.1 won't update past 2.1.6.1022?
TIA,
Steve