-
Posts
5,501 -
Joined
-
Last visited
Content Type
Events
Profiles
Forums
Posts posted by ShyWriter
-
-
.
Microsoft: 0Day Exploit Targeting Word, Outlook
by Brian Krebs | 3-24-2014
Microsoft warned today that attackers are exploiting a previously unknown security hole in Microsoft Word that can be used to foist malicious code if users open a specially crafted text file, or merely preview the message in Microsoft Outlook.In a notice published today, Microsoft advised:
“Microsoft is aware of a vulnerability affecting supported versions of Microsoft Word. At this time, we are aware of limited, targeted attacks directed at Microsoft Word 2010. The vulnerability could allow remote code execution if a user opens a specially crafted [rich text format] RTF file using an affected version of Microsoft Word, or previews or opens a specially crafted RTF email message in Microsoft Outlook while using Microsoft Word as the email viewer. An attacker who successfully exploited the vulnerability could gain the same user rights as the current user.”To be clear, Microsoft said the exploits it has seen so far attacking this vulnerability have targeted Word 2010 users, but according to Microsoft’s advisory the flaw is also present in Word 2003, 2007, 2013, Word Viewer and Office for Mac 2011.
Microsoft says it’s working on an official fix for the flaw, but that in the meantime affected users can apply a special Fix-It solution that disables the opening of RTF content in Microsoft Word. Microsoft notes that the vulnerability could be exploited via Outlook only when using Microsoft Word as the email viewer, but by default Word is the email reader in Microsoft Outlook 2007, Outlook 2010 and Outlook 2013.
One way to harden your email client is to render emails in plain text. For more information on how to do that with Microsoft Outlook 2003, 2007, 2010 and 2013, see these two articles.
SOURCE: https://krebsonsecurity.com/2014/03/microsoft-warns-of-word-2010-exploit/
/Steve -
Sorry - I was quoting BETANEWS.. Please delete ..
Thank you.
Steve
-
.
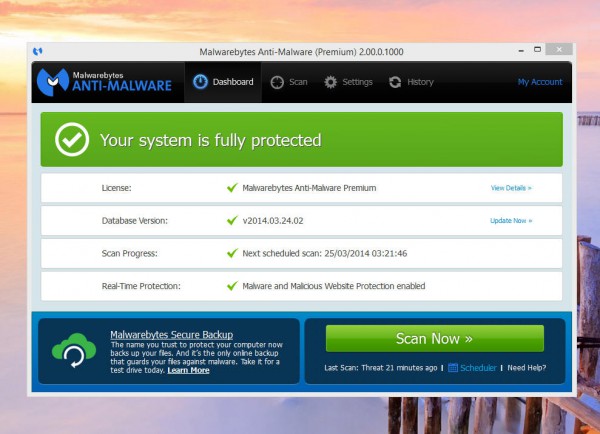
Malwarebytes commits to lifetime support for XP usersBy Ian Barker
The antivirus industry is getting steamed up about the forthcoming end of XP support. Last week we saw Avast warning of the vulnerabilities users might face.
Today anti-virus specialist Malwarebytes announces its new Anti-Malware Premium product and at the same time is pledging that it will continue to support XP users for life.
The company says that XP users currently make up 20 percent of its user base and could be at greater risk after 8 April when support for the old operating system ends.The new Premium product has a streamlined dashboard interface that makes it easy to see the protection status of the PC along with a heuristics engine designed to detect and eliminate malicious software based on its behavior. It also has anti-rootkit technology and adds malicious URL blocking and protection from potentially unwanted programs. As before Malwarebytes will run alongside traditional security software to provide an additional layer of protection. A Chameleon mode allows Malwarebytes to open even if the system has an infection that tries to close down security software.
The company hopes that continuing support for XP will boost its presence in the business market. Marcin Kleczynski, Founder and CEO of Malwarebytes says, "Corporate users can't just upgrade, they may have legacy software running on XP and don't what to spend millions on updating".The new program doesn't replace the free Malwarebytes cleanup tool which has been downloaded more than 200 million times and will continue to be offered. Anti-Malware Premium will be available later today, existing users with lifetime licenses for Malwarebytes Anti-Malware PRO will get a free upgrade to the new version.
Kleczynski concludes, "We are proud of what we have created and believe it builds upon the success of our existing products to give people a strong proactive countermeasure against today’s advanced online threats".SOURCE: http://betanews.com/2014/03/24/malwarebytes-commits-to-lifetime-support-for-xp-users/
/Steve
-
.
WARNING: If using MBAE you MUST "Stop Protection" for a successful install of Java. "Start Protection" again after install.
RE: https://forums.malwarebytes.org/index.php?showtopic=82617&p=804727
Thank you,
Steve
-
.


Security updates for March 11, 2014- Learn how to get security updates automatically
- Get updates from Microsoft Update
- Watch a video about the update

Q&A
How do I know if I already have antivirus software?
If your computer is running Windows 8, you already have antivirus software. If your computer is running Windows 7, Windows Vista, or Windows XP, check to see whether you're protected from viruses, spyware, and other malicious software. Learn more.
Top Stories
5 things you need to know about tech support scams
Unsolicited calls from Microsoft tech support are usually scams designed to install malicious software on your computer, steal your personal information, or both.
The secrets of teens and social media
In her new book, It's Complicated: The Social Lives of Networked Teens, danah boyd leverages more than ten years of research and interviews with teens to help shed light on teenagers and social networking.
5 safety tips for online dating
Valentine's Day has come and gone, but you can still get tips on how to protect your privacy when you're connecting online.

Microsoft vs. malware: a history
For the first time ever, you can read the full story of our battle against worms, viruses, and other malware and the people who create them.
© 2014 Microsoft Corporation Terms of Use | Trademarks
Microsoft respects your privacy. To learn more please read our online Privacy Statement.
Microsoft Corporation
One Microsoft Way
Redmond, WA 98052 USAvia /Steve
-
.
Upcoming Patch Tuesday looks small once againby Ross Barrett | Posted on 07 March 2014Senior Manager, Security Engineering, Rapid7Microsoft’s March Patch Tuesday is again shaping up to be on the lighter side of some months, continuing the 2014 trend of smaller Patch Tuesdays.
We only see 2 issues that are critical/remote code execution, one of which is the usual IE, the other is an Operating System issue which affects most versions of Windows from XP up to 8.1/2012r2. These two are where we should focus our patching efforts.
Of the remaining issues, one is an important privilege issue, probably going to be a kernel or kernel driver patch. Never something to ignore but less important than a critical/remote issue.
The other two are the seldom seen “security mechanism bypass” type, probably the same issue being patched in Windows and in Silverlight. We will have to wait and see how exploitable this turns out to be. If it turns out that some of these issues are “in the wild” and under exploitation, then that will be change the circumstances of what to prioritize.
SOURCE: https://www.net-security.org/secworld.php?id=16487via /Steve -
.
Experian Lapse Allowed ID Theft Service Access to 200 Million Consumer Records
by Brian Krebs | March 14th, 2014
In October 2013, KrebsOnSecurity published an exclusive story detailing how a Vietnamese man running an online identity theft service bought personal and financial records on Americans directly from a company owned by Experian, one of the three major U.S. credit bureaus. Today’s story looks deeper at the damage wrought in this colossal misstep by one of the nation’s largest data brokers.
Vietnamese national Hieu Minh Ngo pleaded
guilty last week to running the ID theft
service Superget.info.
Last week, Hieu Minh Ngo, a 24-year-old Vietnamese national, pleaded guilty to running an identity theft service out of his home in Vietnam. Ngo was arrested last year in Guam by U.S. Secret Service agents after he was lured into visiting the U.S. territory to consummate a business deal with a man he believed could deliver huge volumes of consumers’ personal and financial data for resale.
But according to prosecutors, Ngo had already struck deals with one of the world’s biggest data brokers: Experian. Court records just released last week show that Ngo tricked an Experian subsidiary into giving him direct access to personal and financial data on more than 200 million Americans.
HIEU KNOWS YOUR SECRETS?
As I reported last year, the data was not obtained directly from Experian, but rather via Columbus, Ohio-based US Info Search. US Info Search had a contractual agreement with a California company named Court Ventures, whereby customers of Court Ventures had access to the US Info Search data as well as Court Ventures’ data, and vice versa.
Posing as a private investigator operating out of Singapore, Ngo contracted with Court Ventures, paying for his access to consumer records via regular cash wire transfers from a bank in Singapore. Through that contract, Ngo was able to make available to his clients access to the US Info Search database containing Social Security, date of birth and other records on more than 200 million Americans.
Experian came into the picture in March 2012, when it purchased Court Ventures (along with all of its customers — including Mr. Ngo). For almost ten months after Experian completed that acquisition, Ngo continued siphoning consumer data and making his wire transfers.
Ngo’s ID theft business attracted more than 1,300 customers who paid at least $1.9 million between 2007 and Feb. 2013Until last week, the government had shared few details about the scope and the size of the data breach, such as how many Americans may have been targeted by thieves using Ngo’s identity theft service. According to a transcript of Ngo’s guilty plea proceedings obtained by KrebsOnSecurity, Ngo’s ID theft business attracted more than 1,300 customers who paid at least $1.9 million between 2007 and Feb. 2013 to look up Social Security numbers, dates of birth, addresses, previous addresses, phone numbers, email addresses and other sensitive data.
The government alleges that the service’s customers used the information for a variety of fraud schemes, including filing fraudulent tax returns on Americans, and opening new lines of credit and racking up huge bills in the names of unsuspecting victims. The transcript shows government investigators found that over an 18-month period ending Feb. 2013, Ngo’s customers made approximately 3.1 million queries on Americans. (Much More...)
Continue reading → https://krebsonsecurity.com/2014/03/experian-lapse-allowed-id-theft-service-to-access-200-million-consumer-records/#more-25125
/via Steve
-
.
X-Posted from Security because it affects everyone here including those that don't read the SECURITY sub-Forum.
.

US Tax Season Phishing Scams and Malware Campaigns
Original release date: February 26, 2014
In the past, US-CERT has received reports of an increased number of phishing scams and malware campaigns that seek to take advantage of the United States tax season. The Internal Revenue Service has issued an advisory on its website warning consumers about potential scams. Tax season phishing campaigns may include, but are not limited to:
- Information that refers to a tax refund,
- Warnings about unreported or under-reported income,
- Offers to assist in filing for a refund, or
- Links to counterfeit e-file websites.
These messages, which can appear to be from the IRS, may ask users to submit personal information via email, or include links to sites that request personal information or host malicious code.
To protect themselves against these types of phishing scams and malware campaigns, users and administrators are encouraged to take the following measures:
- Do not follow links in unsolicited email messages.
- Keep antivirus software up to date.
- Refer to US-CERT's Security Tips on Recognizing and Avoiding Email Scams and Avoiding Social Engineering and Phishing Attacks for additional techniques and recommendations.
- Visit the IRS page for instructions on how to report suspected tax season phishing messages.
This product is provided subject to this Notification and this Privacy & Use policy.
/Steve
-
.
Netflix mocks Amazon Prime Air with hilarious 'Drone 2 Home' video
February 25th, 2014 at 6:56AM ET
Netflix's not-Qwikster DVD-by-mail business doesn't get the same amount of attention as the company's streaming arm, but as this video (embedded after the break) shows, it still has some imagination. Dug up by Hacking Netflix, the Drone 2 Home demo video imagines Netflix's famous red envelopes being delivered by quadcopter -- wherever you may be (camping, in the office, in the bathroom -- wherever).
Posted by a couple of employees, it was apparently produced for the DVD division's annual meeting. We're still not sure if Jeff Bezos' holiday-timed Amazon Prime Air drone-delivery reveal was anything more than a publicity stunt, but GM Hank Breeggemann's tongue is firmly in cheek as he announces Netflix's "return to our creative roots."
Of course, there are some drawbacks to spending "literally days" working out the bugs -- but you'll have to watch to find out.
This tongue-in-cheek humor is not intended as an advertisement for any
service and hopefully, not construed as SPAM. This poster, ShyWriter,
occasionally buys product from Amazon (5-day ground delivery only)
and subscribes to NETFLIX streaming service; no discs involved.

/Steve
-
.
It will be interesting to see if the non-Update, non-ServicePak for Windows 8.1 that may be available actually works, much less screw anything up. I can't BEAR to watch..

*snort*
Steve
-
.
New attack completely bypasses Microsoft zero-day protection app
Whitehats' ability to sidestep EMET strongly suggest criminal hackers can, too.
by Dan Goodin - Feb 24 2014, 2:25pm EST
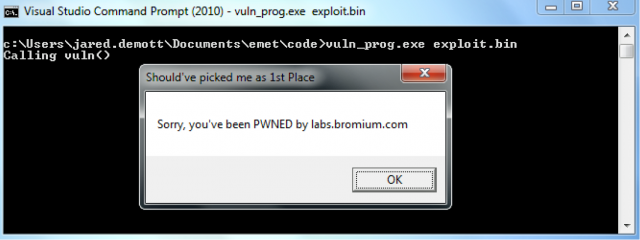 Bromium Labs
Bromium LabsResearchers have developed attack code that completely bypasses Microsoft's zero-day prevention software, an impressive feat that suggests criminal hackers are able to do the same thing when exploiting vulnerabilities that allow them to surreptitiously install malware.
The exploit code, which was developed by researchers from security firm Bromium Labs, bypasses each of the many protections included in the freely available EMET, which is short for Enhanced Mitigation Experience Toolkit, according to a whitepaper published Monday. Microsoft has long held out EMET as an important tool for extending the security of Windows computers. The proof-of-concept exploit shows the limitations of those protections. The Bromium exploit included an example of a real-world attack that was able to circumvent techniques designed to mitigate the damage malicious code can do when targeting security bugs included in third-party applications.
"The impact of this study shows that technologies that operate on the same plane of execution as potentially malicious code offer little lasting protection," Bromium Labs researchers wrote in a blog post. "This is true of EMET and other similar userland protections. That’s because a defense that is running in the same space as potentially malicious code can typically be bypassed, since there's no 'higher' ground advantage as there would be from a kernel or hypervisor protection. We hope this study helps the broader community understand the facts when making a decision about which protections to use."The Bromium research was presented Monday at the BSides SF 2014 security conference in San Francisco. The researchers said their attack was able to slice through each of the protections available in EMET, including stack pivot protection, export address table access filtering, and measures to block a malicious coding technique known as return-oriented programming. The researchers privately informed security personnel at Microsoft before going public with their findings; the software giant plans to credit the research when releasing the upcoming version 5 of EMET. Among the researchers who developed the exploit was Jared Demott, who earned third place in the Bluehat contest, in which Microsoft paid cash awards for the creation of exploit mitigations.
Microsoft worked with Bromium on the original research, Jonathan Ness, principal security development manager in Microsoft's Trustworthy Computing group said in a statement. What's more, EMET 4.1, which was released several months ago, already contained a setting to address some issues and help customers. Ness didn't answer Ars's question asking when EMET 5 would be released. Despite Microsoft's work to update EMET, the Bromium Labs researchers warned that there may not be much Microsoft developers can do to fix some weaknesses.
However, as was seen in our research, deploying EMET does mean attackers have to work a little bit harder; payloads need to be customized, and EMET bypass research needs to be conducted. Thus, EMET is good for the price (free), but it can be bypassed by determined attackers. Microsoft freely admits that it is not a perfect protection, and comments from Microsoft speakers at conference talks admit that as well. The objective of EMET is not perfection, but to raise the cost of exploitation. So the question really is not can EMET be bypassed. Rather, does EMET sufficiently raise the cost of exploitation? The answer to that is likely dependent upon the value of the data being protected. For organizations with data of significant value, we submit that EMET does not sufficiently stop customized exploits.As complete and effective as the Bromium Labs exploit is, the researchers said that EMET may still be worth using, depending on the specific computers being protected. They explained:
"The bypasses leverage generic limitations, and are not easily repaired," they wrote.
A recent in-the-wild attack that exploited a previously undocumented vulnerability in Internet Explorer was designed to remain dormant on machines running EMET. The takeaway from Monday's disclosure should be that EMET remains an effective—but by no means infallible—protection.
/Steve
-
. Microsoft officially acknowledges Windows 8.1 'spring' update
Summary: Microsoft execs have acknowledged publicly what's been rumored for months: An update to Windows 8.1 is coming to users this spring.
For the first time publicly, Microsoft officials are acknowledging that the company is working on an update to Windows 8.1 that will be out this spring.

While we Microsoft watchers have been writing about the so-called Windows 8.1 Update 1 for months, and builds of the update have been leaking for weeks, February 23 was the first time that Microsoft execs officially commented on the coming release.
At Microsoft's press event at the Mobile World Congress show in Barcelona, Microsoft went public with some of the already-known features coming in the update that is meant to improve Windows 8.1's usability and acceptance by mouse/keyboard users.
Officials discussed 8.1 update tweaks, such as inclusion of a title bar at the top of Modern/Windows Store apps, and the addition of power and search buttons on the Start Screen, according to a report by The Verge's Tom Warren, who attended the Microsoft event. Officials also acknowledged the smaller footprint (1 GB of RAM; 16 GB of storage) of the update, which will enable device makers to put Windows 8.1 with the update on smaller, cheaper tablets. Microsoft also is reportedly planning to offer PC makers a price cut on Windows 8.1 on machines costing $250 or less to entice OEMs to get cheaper Windows 8.1 devices to market.
AnandTech (also attending the event) noted that Microsoft execs also acknowledged Windows 8.1 Update 1 will include IE8 compatibility mode in IE11 -- previously reported as IE11 Enterprise Mode.
Microsoft officials didn't provide a specific timeframe as to when the spring update will be available, but my sources previously have said the target release date will be April 8, with Microsoft delivering it via Windows Update to existing Windows 8.x users.
Update: The Windows Server team is also confirming it will deliver a minor update to Windows Server 2012 R2 that will hit alongside the Windows 8.1 Update 1 release "this spring." The server-side update will include "minor UI enhancements and bug fixes, as well as previously-released monthly update rollups and security fixes," officials said. Microsoft will be working to make sure existing Windows Server apps, from both Microsoft and third party developers, "just work" with the update. More details on the server-side update will be provided at a future date, officials said.
SOURCE: http://www.zdnet.com/microsoft-officially-acknowledges-windows-8-1-spring-update-7000026632
/Steve
-
.
Microsoft releases fix for Windows Update corruption errors
Summary: Non-critical patch addresses problems in the Windows Update system files which could cause errors in future updates.
Microsoft has released a non-critical, non-security update to fix a bug in the Windows Update system in certain versions of Windows.
Microsoft found problems in the Windows servicing store which may prevent the successful installation of future updates, service packs, and software. This update is a tool which checks the system for these problems and tries to resolve them.
Errors in Windows Update with the following codes are addressed by this update: 0x80070002, 0x8007000D, 0x800F081F, 0x80073712, 0x800736CC, 0x800705B9, 0x80070246, 0x8007370D, 0x8007370B, 0x8007370A, 0x80070057, 0x800B0100, 0x80092003, 0x800B0101, 0x8007371B, 0x80070490.
On Windows 7, Windows Server 2008 R2, Windows Server 2008, and Windows Vista the tool is called the System Update Readiness Tool. The various versions of the update may be downloaded directly from KB947821. Installation instructions are on that page.
On Windows 8.1, Windows 8, Windows Server 2012 R2 or Windows Server 2012 you can use the included Deployment Image Servicing and Management (DISM) tool. Follow instructions in KB947821.
This fix may appear at some point in Windows Update itself, but it is not there as of today.
This update was announced on Microsoft's Description of Software Update Services and Windows Server Update Services changes in content for 2014, dated February 25, 2014. A second update scheduled for that date, Update for Windows 7 and Windows Server 2008 R2 (KB2923545), will "resolve issues in Windows", and has not yet gone live.
SOURCE: http://www.zdnet.com/microsoft-releases-fix-for-windows-update-corruption-errors-7000026582/
/Steve
-
.
Microsoft is pushing two out-of-cycle updates for Windows 8.1
Update 1 is rated IMPORTANT:
Security Update for Internet Explorer Flash Player for Windows 8.1 for x64-based Systems (KB2934802)
Update type: Important
A security issue has been identified in a Microsoft software product that could affect your system. You can help protect your system by installing this update from Microsoft. For a complete listing of the issues that are included in this update, see the associated Microsoft Knowledge Base article. After you install this update, you may have to restart your system.
More information:
http://support.microsoft.com/kb/2934802
Help and Support:
http://support.microsoft.com
Update 2 is rated OPTIONAL but fixes close to 20 bugs..
Update for Windows 8.1 for x64-based Systems (KB2919394)
Update type: Optional
Install this update to resolve issues in Windows. For a complete listing of the issues that are included in this update, see the associated Microsoft Knowledge Base article for more information. After you install this item, you may have to restart your computer.This update package fixes the issues that are documented in the following Microsoft Knowledge Base (KB) articles:
- 2918245 "Landscape (flipped)" orientation is changed to "Landscape" when you sign out of Windows 8.1
- 2918573 Compliance check is incorrect when you use Exchange ActiveSync to perform a compliance check in Windows 8.1
- 2919827 Gridview items are blurry when you zoom in or zoom out in Windows 8.1
- 2920136 Netflix users encounter error H7353 when resuming movie playback from a previously saved bookmark in Windows 8.1
- 2920196 You cannot create or change the name of a debugger named pipe for a VM when it is running in Windows 8.1 or Windows Server 2012 R2
- 2920469 You cannot change the schedule for CAU self-updating mode in Windows Server 2012 or Windows Server 2012 R2 by using CAU GUI
- 2921059 Windows Location Provider fails the geolocation lookup in Windows 8.1
- 2921066 Computer never goes to sleep even if the timer is set in Windows 8.1
- 2921101 Video frame rate is low in remote sessions to a Windows 8.1 or Windows Server 2012 R2 virtual machine
- 2922809 First letter of an autocorrect suggestion is not capitalized in Windows 8.1
- 2922812 Shutdown time is longer when shutting down from the Start hint context menu in Windows 8.1
- 2922817 Error 8e5e0530 when installing Windows Store apps in a Windows 8.1 system that was deployed by using the CopyProfile unattend setting
- 2922850 Stop error 0x9F in the Usbhub.sys driver in Windows 8.1
- 2923125 Hotfix randomizes the DSM task creation time in Windows 8.1
- 2923126 Application crashes when the search path is constructed for non-static dependencies of the module in Windows 8.1
- 2923551 You cannot obtain a developer license by using only the keyboard in Windows 8.1 or Windows Server 2012 R2
- 2924014 0xD1 Stop error occurs when running tests in 3DMark on a Windows 8.1-based computer
- 2878604 Drive is unexpectedly mapped to the root of a nested share in Windows 8 or Windows Server 2012
- 2922514 White line appears when printing an image by using an XPS printer driver in Windows 8.1, Windows 8, Windows Server 2012 R2 and Windows Server 2012
- 2866345 "AD / SYSVOL version mismatch" message is displayed unexpectedly in the Group Policy Results report in Windows
More information:
http://support.microsoft.com/kb/2919394Help and Support:
http://support.microsoft.com
Posted for those that manually check for updates..
Steve
-
.
I posted the update yesterday morning in General Software sub-Forum.
https://forums.malwarebytes.org/index.php?showtopic=124898&p=794207
12.0.0.70 was the download one got even tho' the table showed ".44" as the newest. A test of the version one had would also show ".44" installed (before downloading) without showing a newer version was available. Downloading would show 12.0.0.70 installed. In other words, the download people got their file made available before the documentation people got the wording done.

@Arthur
11.2.202.341 is the last version Adobe made for linux. Other than security fixes (these fixes were for Windows vulnerabilities) the Linux version will stay at 11.2.202.341. I.e.; it's EOL except for security fixes. Google (pepper flash - 12.0.0.70) is doing their own thing on linux and is not officially an Adobe product.
Cheers,
Steve
Your friendly software updater, punching bag, etc, et al..

-
.
Adobe, Microsoft Push Fixes For 0-Day Threats
by Brian Krebs
For the second time this month, Adobe has issued an emergency software update to fix a critical security flaw in its Flash Player software that attackers are already exploiting. Separately, Microsoft released a stopgap fix to address a critical bug in Internet Explorer versions 9 and 10 that is actively being exploited in the wild.
The vulnerabilities in both Flash and IE are critical, meaning users could get hacked just by visiting a compromised or booby-trapped Web site. The Flash patch comes just a little over two weeks after Adobe released a rush fix for another zero-day attack against Flash.
Adobe said in an advisory today that it is aware of an exploit that exists for one of three security holes that the company is plugging with this new release, which brings Flash Player to v. 12.0.0.70 for (Chrome-Linux), Mac and Windows systems.
This link will tell you which version of Flash your browser has installed. IE10/IE11 and Chrome should auto-update their versions of Flash, although IE users may need to check with the Windows Update feature built into the operating system. (Much more..)
Read the rest plus access SHIM fix at: https://krebsonsecurity.com/2014/02/adobe-microsoft-push-fixes-for-0-day-threats/
Steve
-
.
Kickstarter hacked. Change your password now
Summary: The popular crowdfunded site Kickstarter has been hacked and the breach included usernames and passwords. Change your password now to prevent further damage.
Kickstarter suffered a data breach that may have led to the disclosure of personal information.
On Saturday, I received this notification in my inbox. If you have a Kickstarter account or campaign, you need to read and heed the following message:
Kickstarter, for those of you who don't know, is a crowdfunding site for projects of all kinds including movies, books, art, and new products.
"On Wednesday night, law enforcement officials contacted Kickstarter and alerted us that hackers had sought and gained unauthorized access to some of our customers' data. Upon learning this, we immediately closed the security breach and began strengthening security measures throughout the Kickstarter system.
No credit card data of any kind was accessed by hackers. There is no evidence of unauthorized activity of any kind on your account.
While no credit card data was accessed, some information about our customers was. Accessed information included usernames, email addresses, mailing addresses, phone numbers, and encrypted passwords. Actual passwords were not revealed, however it is possible for a malicious person with enough computing power to guess and crack an encrypted password, particularly a weak or obvious one.
As a precaution, we strongly recommend that you change the password of your Kickstarter account, and other accounts where you use this password.
To change your password, log in to your account at Kickstarter.com and look for the banner at the top of the page to create a new, secure password. We recommend you do the same on other sites where you use this password. For additional help with password security, we recommend tools like 1Password and LastPass.
We’re incredibly sorry that this happened. We set a very high bar for how we serve our community, and this incident is frustrating and upsetting. We have since improved our security procedures and systems in numerous ways, and we will continue to do so in the weeks and months to come. We are working closely with law enforcement, and we are doing everything in our power to prevent this from happening again.
Kickstarter is a vibrant community like no other, and we can’t thank you enough for being a part of it. Please let us know if you have any questions, comments, or concerns. You can reach us at accountsecurity@kickstarter.com.
As soon as you login to Kickstarter, you're prompted to change your password due to the security breach.
As you might know, I'm not a big fan of Kickstarter because of the way projects are funded but I have to say that I'm proud of the chief executive for coming forward so quickly about the breach. Other companies should follow the same transparent ideal and admit when something like this happens so that customers and members can take immediate action.
I think that this is a move in the right direction for companies and sites that have been hacked. Though not much is currently known about the hack, therefore you should take all precautions against brute force attacks against the password files that were captured by changing your password immediately.
SOURCE: http://www.zdnet.com/kickstarter-hacked-change-your-password-now-7000026388/
/Steve
-
.
Microsoft sets Oct. 31 as stop date for Windows 7 consumer PC sales
But extends end-of-sales date for business PCs running Windows 7 Professional
By Gregg KeizerFebruary 15, 2014 02:09 PM ETComputerworld - Microsoft has set Oct. 31 as the end of sales of new consumer-grade Windows 7 PCs, but for now has left open the do-not-sell-after-this-date for business machines.
On the site where it posts such policies, Microsoft now notes that Oct. 31, 2014, is the end-of-sales date for new PCs equipped with Windows 7 Home Basic, Home Premium or Ultimate. All three are consumer-oriented versions of Windows 7; Home Premium has been the overwhelming choice of OEMs (original equipment manufacturers) for consumer systems.
Microsoft's practice, first defined in 2010, is to stop selling an older operating system in retail one year after the launch of its successor, and halt delivery of the previous Windows edition to OEMs two years after a new version launches. The company shipped Windows 8, Windows 7's replacement, in October 2012.
The setting of a deadline for consumer Windows 7 PCs followed a glitch last year when Microsoft named the same Oct. 31 date for all Windows 7 PCs, but then quickly retracted the posting, claiming that the notification had been posted "in error."
Some OEMs, notably Hewlett-Packard, have made headlines for marketing consumer-grade Windows 7 PCs, a sign of the fragmentation of the once-dominant Windows oligarchy, which always pushed the newest at the expense of older editions.
But while it has established an end-of-sales date for consumer PCs with Windows 7 pre-installed, Microsoft has yet to do the same for business PCs.
Microsoft will give a one-year warning before it demands that OEMs stop selling PCs with Windows 7 Professional, the commercial-quality version. Under that rule, Microsoft will allow computer makers such as Lenovo, HP and Dell to continue selling PCs with Windows 7 Professional until at least February 2015.
It's likely that the extension will be much longer.
Windows 7 has become the standard version for businesses, which have spurned Windows 8, largely because of its two-user interface (UI) model, which they consider disruptive to productivity and a needless cost that would require employee retraining.
Most analysts believe that Windows 7 will remain the most popular Microsoft operating system deployed by companies for years to come.
"There's a good chance that enterprises will stay on Windows 7 as long as possible," said Gartner analyst Michael Silver in an October 2013 interview. If his prediction turns out to be accurate, Windows 7 may reprise the stubborn persistence of Windows XP, the nearly-13-year-old OS that Microsoft will retire in April.
Even after Windows 8's launch, Windows 7's user share, a rough measurement of the prevalence of the OS on operational machines, has continued to grow. From October 2012 to January 2014, Windows 7's user share increased nearly 3 percentage points, representing a 6% gain during that period, according to data from analytics company Net Applications.
Some of Windows 7's gains certainly came at the expense of Windows XP, which has fallen more than 11 percentage points, a 28% decline, since October 2012 as users abandoned the old OS.
By making Windows 7 available, Microsoft and its OEMs not only continue to serve customers who want the OS, but make sure that new PC sales do not slump even more dramatically than they have already. (More...)
-
Can I charge it to your Visa, Shy?
No thank you..
 I can't even afford what I charge to it.
I can't even afford what I charge to it. 
I have plenty of Coke Reward points you're welcome to tho'.. *wry smile*
Steve
-
Tell me about it.. I just spent all yesterday thru midnight watching all 13 new episodes of season 2... NOW; I have to wait a year for season 3.. aarrghhhhhhh!! I won't mention any spoilers but it sure looks like the way real politics work.. *evil grin*
I was lucky; the granddaughters were here keeping the wife busy and out of my hair..
Steve
-
.
Update: Third of Internet Explorer users at risk from attacks
Microsoft confirms both IE9 and IE10 contain vulnerability, urges customers to upgrade to IE11; leaves Vista users out in the cold
By Gregg KeizerFebruary 14, 2014 05:15 PM ETComputerworld - Microsoft on Friday said that both Internet Explorer 10 and its predecessor, IE9, contained an unpatched vulnerability, but that hackers were currently exploiting only the newest, IE10.
The extension of the vulnerability to IE9 followed confirmation earlier yesterday that active attacks are compromising the newer IE10 and hijacking PCs running the browser.
"Microsoft is aware of limited, targeted attacks against Internet Explorer 10. Our initial investigation has revealed that Internet Explorer 9 and Internet Explorer 10 are affected," a Microsoft spokesperson said via email today.
With both IE9 and IE10 vulnerable, it means that about a third of all those using Internet Explorer are at risk.
According to Web analytics vendor Net Applications, IE9 accounted for 15.3% of the total IE user share last month; IE10's share was 15.9%. Together, the two editions represented 31.2% of Internet Explorer's January user share.
Milpitas, Calif.-based FireEye was the first to spot the attacks, and said that they had been aimed at IE10 as part of a campaign targeting current and former U.S. military personnel when they visited the Veterans of Foreign Wars (VFW) website.
While FireEye said it identified the "zero-day" vulnerability -- a term to indicate that the flaw is currently unpatched -- on Feb. 11, yesterday San Diego security company Websense said it had found evidence that the exploit may have been used as early as Jan. 20, or more than three weeks ago.
Websense also speculated that those earlier attacks had been aimed at visitors to a French aerospace association's website. Members of the organization, GIFAS (Groupement des Industries Francaises Aeronautiques et Spatiales), include defense and space contractors and subcontractors.
GIFAS is best known to the general public as the sponsor, through a subsidiary, of the Paris Air Show, an annual extravaganza where aircraft makers, both commercial and military, strut their newest wares.
Microsoft's advice to customers that they upgrade to IE11 was not possible for those still running Windows Vista. That 2007 operating system cannot run either IE10 or IE11. Most Vista users are likely running IE9, since Microsoft automatically upgraded their copies of from IE7 or IE8 to the then-new IE9 in the first half of 2012.
The only silver lining is that few Windows users run Vista: Last month, the oft-disparaged OS represented just 3.6% of all editions of Windows.
Microsoft has not said if it will issue an "out-of-band" security update -- a rush fix shipped before the next regularly-scheduled Patch Tuesday of March 11 -- or yet issued a formal security advisory. It will certainly do the latter, and at that time may, as it often does, provide a work-around to protect IE9 and IE10 users.
Steve
-
Even if you hate politics (hand in air - fraking politicians - Uugghhhh!), HOUSE OF CARDS is OUTSTANDING!!
As usual for NetFlix originals, one can watch ALL the episodes, one after another - no weekly wait/no commercials/EXCELLENT acting..
Steve
-
Ummmm.. Guys; why not take the last good database (.5 or .6 from today) and rename it to a much higher version (like .12) and then not put any more updates on the server until the problem is fixed. BTW; I had no problem moving those 3 files earlier; unfortunately it didn't fix my MBAM2 problem and 1.75 runs but no "protection".
Steve
-
Samuel,
The 3-file fix didn't fix MBAM2 for me. Went back and installed 1.75 instead which updated to today's .9 database.. Now 1.75 won't work either - can't check the boxes in the pix. Yes-activated license first..


Win8.1 / x64



Malwarebytes commits to lifetime support for XP users
in Malwarebytes News
Posted
Thanks Marcin.. This is a VERY generous offer from a great company.
You're the best,
Steve