-
Posts
5,501 -
Joined
-
Last visited
Content Type
Events
Profiles
Forums
Posts posted by ShyWriter
-
-
.
Compliments of Wiley Miller:

/Steve
-
.
Sorry for late posting on this - US-CERT hasn't added it to the ALERT list yet..
Oracle Critical Patch Update Pre-Release Announcement - April 14, 2014
Description:
This Critical Patch Update Pre-Release Announcement provides advance information about the Oracle Critical Patch Update for April 2014, which will be released on Tuesday, April 15, 2014. While this Pre-Release Announcement is as accurate as possible at the time of publication, the information it contains may change before publication of the Critical Patch Update Advisory.
A Critical Patch Update is a collection of patches for multiple security vulnerabilities. This Critical Patch Update contains 103 new security vulnerability fixes across hundreds of Oracle products. Some of the vulnerabilities addressed in this Critical Patch Update affect multiple products. Due to the threat posed by a successful attack, Oracle strongly recommends that customers apply Critical Patch Update fixes as soon as possible. (More...)
Rest of announcement here: http://www.oracle.com/technetwork/topics/security/cpuapr2014-1972952.html
Java Updates were not yet available at 1000 hrs eastern time
Affected Products and Components
Security vulnerabilities addressed by this Critical Patch Update affect the following products:
- Oracle Database 11g Release 1, version 11.1.0.7
- Oracle Database 11g Release 2, versions 11.2.0.3, 11.2.0.4
- Oracle Database 12c Release 1, version 12.1.0.1
- Oracle Fusion Middleware 11g Release 1, versions 11.1.1.7, 11.1.1.8
- Oracle Fusion Middleware 12c Release 1, versions 12.1.1.0, 12.1.2.0
- Oracle Fusion Applications, versions 11.1.2 through 11.1.8
- Oracle Access Manager, versions 10.1.4.3, 11.1.1.3.0, 11.1.1.5.0, 11.1.1.7.0, 11.1.2.0.0, 11.1.2.1.0, 11.1.2.2.0
- Oracle Containers for J2EE, version 10.1.3.5
- Oracle Data Integrator, version 11.1.1.3
- Oracle Endeca Server, version 2.2.2
- Oracle Event Processing, version 11.1.1.7.0
- Oracle Identity Analytics, version 11.1.1.5, Sun Role Manager, version 5.0
- Oracle OpenSSO, version 8.0 Update 2 Patch 5
- Oracle OpenSSO Policy Agent, version 3.0-03
- Oracle WebCenter Portal, versions 11.1.1.7, 11.1.1.8
- Oracle WebLogic Server, versions 10.0.2.0, 10.3.6.0, 12.1.1.0, 12.1.2.0
- Oracle Hyperion Common Admin, versions 11.1.2.2, 11.1.2.3
- Oracle E-Business Suite Release 11i, 12i
- Oracle Agile PLM Framework, versions 9.3.1.1, 9.3.3.0
- Oracle Agile Product Lifecycle Management for Process, versions 6.0.0.7, 6.1.1.3
- Oracle Transportation Management, versions 6.3, 6.3.4
- Oracle PeopleSoft Enterprise CS Campus Self Service, version 9.0
- Oracle PeopleSoft Enterprise HRMS Talent Acquisition Manager, versions 8.52, 8.53
- Oracle PeopleSoft Enterprise PT Tools, versions 8.52, 8.53
- Oracle Siebel UI Framework, version 8.1.1.10
- Oracle JavaFX, version 2.2.51
- Oracle Java SE, versions 5.0u61, 6u71, 7u51, 8
- Oracle Java SE Embedded, version 7u51
- Oracle JRockit, versions R27.8.1, R28.3.1
- Oracle Solaris, versions 9, 10, 11.1
- Oracle Secure Global Desktop, versions 4.63, 4.71, 5.0, 5.1
- Oracle VM VirtualBox, versions prior to 3.2.22, 4.0.24, 4.1.32, 4.2.24, 4.3.10
- Oracle MySQL Server, versions 5.5, 5.6
Java Updates were not yet available at 1000 hrs eastern time
Steve
-
.
Crimeware Helps File Fraudulent Tax Returns
by Brian Krebs | April 15th, 2014
Many companies believe that if they protect their intellectual property and customers’ information, they’ve done a decent job of safeguarding their crown jewels from attackers. But in an increasingly common scheme, cybercriminals are targeting the Human Resources departments at compromised organizations and rapidly filing fraudulent federal tax returns on all employees.
Last month, KrebsOnSecurity encountered a Web-based control panel that an organized criminal gang has been using to track bogus tax returns filed on behalf of employees at hacked companies whose HR departments had been relieved of W2 forms for all employees.
Click on image to zoom
An obfuscated look at the he control panel for a tax fraud operation involving more than a half dozen victim organizations.
According to the control panel seen by this reporter, the scammers in charge of this scheme have hacked more than a half-dozen U.S. companies, filing fake tax returns on nearly every employee. At last count, this particular scam appears to stretch back to the beginning of this year’s tax filing season, and includes fraudulent returns filed on behalf of thousands of people — totaling more than $1 million in bogus returns.
The control panel includes a menu listing every employee’s W2 form, including all data needed to successfully file a return, such as the employee’s Social Security number, address, wages and employer identification number. Each fake return was apparently filed using the e-filing service provided by H&R Block, a major tax preparation and filing company. H&R Block did not return calls seeking comment for this story.
Click on image to zoom
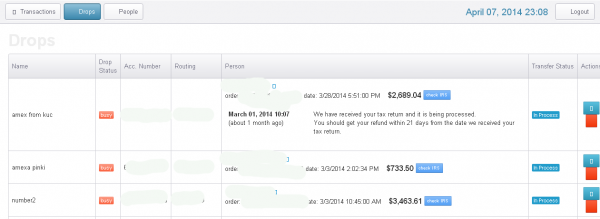
The “drops” page of this tax fraud operation lists the nicknames of the co-conspirators who agreed to “cash out” funds on the prepaid cards generated by the bogus returns — minus a small commission.
Fraudulent returns listed in the miscreants’ control panel that were successfully filed produced a specific five-digit tax filing Personal Identification Number (PIN) apparently generated by H&R Block’s online filing system. An examination of the panel suggests that successfully-filed returns are routed to prepaid American Express cards that are requested to be sent to addresses in the United States corresponding to specific “drops,” or co-conspirators in the scheme who have agreed to receive the prepaid cards and “cash out” the balance — minus their fee for processing the bogus returns.
Alex Holden, chief information security officer at Hold Security, said although tax fraud is nothing new, automating the exploitation of human resource systems for mass tax fraud is an innovation.
“The depth of this specific operation permits them to act as a malicious middle-man and tax preparation company to be an unwitting ‘underwriter’ of this crime,” Holden said. “And the victims maybe exploited not only for 2013 tax year but also down the road, and perhaps subject of higher scrutiny by IRS — not to mention potential financial losses. Companies should look at their human resource infrastructure to ensure that payroll, taxes, financial, medical, and other benefits are afforded the same level of protection as their other mission-critical assets.” (More...)
SOURCE: https://krebsonsecurity.com/2014/04/crimeware-helps-file-fraudulent-tax-returns/
/Steve
-
Thanks for the quick reply.
Cheers
EDIT: BOTH tests show MBAE working (calc exploit and dll insertion)
-
Pedro,
For some reason MBAE is showing nothing is protected in snap one while the log shows Mozilla *is* protected in snap 2.. Very odd; yes?? BTW, both snaps are from the same open application; just different tabs.
Win8.1 w/update 1 and MBAE 0.10.3.0100
Snap One:

Snap Two:

Thanks in advance,
Steve
-
.
Compliments of Briane Crane:

/Steve
-
.
Compliments of Gary Brookins & Susie MacNelly:

/Steve
-
.
Heartbleed Tester
Test for CVE-2014-0160OpenSSL Buffer Over-read
Great news is Malwarebyte's Forums site is NOT vulnerable...
Check other sites by entering the web address at THIS site:
http://heartbleed.criticalwatch.com/
With thanks to Brian Krebs blog post of April 10th, 2014..https://www.youtube.com/watch?&v=oZqXt0iddDQ
Learn more about Heartbleed in the above video
Steve
-
.
Breaches expose 552 million identities in 2013Posted on 10 April 2014.After lurking in the shadows for the first ten months of 2013, cybercriminals unleashed the most damaging series of cyberattacks in history. Symantec’s Internet Security Threat Report (ISTR), Volume 19, shows a significant shift in cybercriminal behavior, revealing the bad guys are plotting for months before pulling off huge heists – instead of executing quick hits with smaller rewards.
 “One mega breach can be worth 50 smaller attacks,” said Kevin Haley, director, Symantec Security Response. “While the level of sophistication continues to grow among attackers, what was surprising last year was their willingness to be a lot more patient – waiting to strike until the reward is bigger and better.”
“One mega breach can be worth 50 smaller attacks,” said Kevin Haley, director, Symantec Security Response. “While the level of sophistication continues to grow among attackers, what was surprising last year was their willingness to be a lot more patient – waiting to strike until the reward is bigger and better.”In 2013, there was a 62 percent increase in the number of data breaches from the previous year, resulting in more than 552 million identities exposed – proving cybercrime remains a real and damaging threat to consumers and businesses alike.
“Security incidents, managed well, can actually enhance customer perceptions of a company; managed poorly, they can be devastating,” wrote Ed Ferrara, VP and principal analyst, Forrester Research. “If customers lose trust in a company because of the way the business handles personal data and privacy, they will easily take their business elsewhere.” (More...)Read the rest at: http://www.net-security.org/secworld.php?id=16668
/Steve
-
.
Microsoft requires migration to Windows 8.1 Update within 5 weeks
'Just plain crazy' that Windows 8.1 users must apply Windows 8.1 Update before May 13 to keep getting patchesBy Gregg Keizer
April 8, 2014 11:27 AM ET
Computerworld - Microsoft yesterday confirmed that Windows 8.1 users must upgrade to Windows 8.1 Update, the refresh that begins rolling out to customers today. (April 8th - Tues)"Failure to install this Update will prevent Windows Update from patching your system with any future updates starting with updates released in May 2014," said Michael Hildebrand of Microsoft in a Monday blog.Elsewhere, Microsoft pegged Windows 8.1 Update as "the new servicing baseline for Windows 8.1," again emphasizing that customers who have moved to Windows 8.1 since October 2013 must deploy the Update to receive future bug fixes, security patches and feature enhancements. (More..)
Read the rest at: https://www.computerworld.com/s/article/9247520/Microsoft_requires_migration_to_Windows_8.1_Update_within_5_weeks
/Steve
-
.
Excerpt from
Brian Krebs | 4-08-2014
Microsoft offers free a Windows XP data transfer tool to ease the hassle of upgrading to a newer version of Windows. I would submit that if your PC runs XP and came with XP installed, that it might be time to upgrade the computer hardware itself in addition to the software. In any case, beyond this month is not the greatest idea, and it’s time for XP users to consider other options. Don’t forget that there are many flavors of Linux that will run quite happily on older hardware. If you’ve been considering the switch for a while, take a few distributions for a spin using one of dozens of flavors of Linux available via Live CD./Steve
-
Yep; but you and I have the dubious distinction of being the ONLY two users on the whole system with over 162,000 profile views each.. I can see why that many people wanted to see yours but can't figure out why they wanted to see mine.

-
.
Will my PC be at risk after support ends for Windows XP?
PCs running Windows XP after April 8, 2014 should not be considered to be truly protected.
After support ends for Windows XP on April 8, 2014, Microsoft will no longer provide security updates for Windows XP to help protect your PC against malware. On this same date, Microsoft will also stop providing Microsoft Security Essentials for download on Windows XP.
If you already have Microsoft Security Essentials installed when support ends for Windows XP, you will continue to receive Microsoft Security Essentials updates for a limited time to help identify malware on your PC. You can also still get the Malicious Software Removal Tool for Windows XP for a limited time through Windows Update and the Download Center.These updates to our antimalware products for Windows XP can help detect and block certain malware on your Windows XP PC while you complete your transition to a fully supported operating system. It’s important to note, however, that because antimalware products have limited effectiveness on PCs that do not have the latest security updates, your PC will still be at risk for infection.
We strongly recommend that you complete your migration to a supported operating system as soon as possible so that you can receive regular security updates to help protect your computer from malicious attacks.
SOURCE: Quoted from portion of http://windows.microsoft.com/en-us/windows/security-essentials-download?os=winxp&arch=other
/Steve
-
.
Why the 'retired' Windows XP ain't going nowhere
There are simply too many specialized apps and hardware devices that can't run anything but Windows XPBy Galen Gruman | InfoWorld | April 08, 2014
Today is the day that Microsoft has fully retired Windows XP: no more patches or updates after today, not even for security, and no more support. But if you think for a minute that XP will fade away in its retirement, think again. Windows XP may have been retired, but it will have an active retirement. About a third of PCs still run it, retired by Microsoft or not. Indeed, many have no choice but to run XP.
Yes, if you're an active Windows user without special needs, you should be running Windows 7 instead of XP. Windows 7 is more secure, more modern in look and feel, and more supportive of current technologies. But for a sizable portion of the computing population, Windows 7 is not an option.
There are two key groups of people that will be using XP for a long time. The major segment includes business users tied to specific hardware or software that requires XP itself or an XP-only version of Internet Explorer. That covers a lot of ground: homegrown apps, specialty apps from optometry office management to industrial controllers, ATMs, utility company gear, and on and on.
In many cases, the original software developers are gone or the price for the new version is unaffordable (I hear that a lot from local-government agencies and medical offices). As for hardware, much of it is essentially embedded -- electron microscopes, medical equipment, ATMs, pump regulators -- in systems that must be stable and need to run for decades. These are the equivalents of Cobol-running mainframes: Changing them out is both very expensive and very risky -- so you don't.
The other big group of XP users is composed of people who don't use computers much and are technology-averse -- people like my mom, who still doesn't quite get how a right-click works and is of an age where she's not interested in learning a new way of computing just to do what she already is doing: email, bill payment, Web research. For these people -- there are a lot of them -- Windows XP is like their 15-year-old car and 40-year-old house: old school, but perfectly serviceable. If they have a good antimalware package installed, let these people run XP forever.
A third group sometimes cited as XP-forever standbys are poor people, who can't afford a new computer. That group is not a significant one, as various Pew Research studies have shown. First, poor people are far less likely to have computers, new or old, so they tend to rely on computers at libraries and schools. Poor people also tend to use mobile devices as their computer. These two harsh facts mean they're not wed to XP as you might think. Yes, there are some people who can't afford a new PC and rely on an old XP unit, but it's not a segment that explains XP's current huge share of the PC installed base.
It's the first group that matters most, because those people are in organizations that use (or soon will use) Windows 7 as the primary OS, with XP the minority OS for those who can't move. That duality creates all sorts of headaches for both users and IT. But all a company can do is mimimize the use of XP to where there really is no good alternative, and isolate such systems where possible to prevent accidental IE and driver updates that would make them not work properly any longer.
These specialized uses aren't going away -- there's no place for them to migrate, a big failing on Microsoft's part. Yes, it created XP Mode and MED-V and other complex approaches for Windows 7, but they are complex and often do not work. They simply don't scale, and thus don't address the fundamental migration issue specialized users have. Likewise, the individuals who use XP because it's all they need and all they want to know aren't disappearing, either. As a result, XP will be an active OS for years to come, despite its formal retirement.SOURCE: This article, "Why the 'retired' Windows XP ain't going nowhere," was originally published at InfoWorld.com.
/Steve
-
.
Windows 8.1 Update is a mandatory update for Windows 8.1 users
Microsoft released Windows 8.1 in October 2013, and while it was recommended for all Windows 8 users, it was not a requirement to continue receiving support from the company. That won't be the case for Windows 8,1 users when it comes to Tuesday's release of Windows 8.1 Update as it will be delivered via Windows update.
In a Microsoft Premier Field Engineering Platform blog post, the company flat out says that Windows 8.1 Update is a required download for Windows 8.1 users. The blog post states:
Failure to install this Update will prevent Windows Update from patching your system with any future updates starting with Updates released in May 2014 (get busy!)
Windows 8 users who have yet to update to Windows 8.1 don't necessarily need to also download this update, although it might not be a bad idea. Microsoft has already announced that it will stop supporting Windows 8 in the very near future.
Previously, the company indicated that it will end support for Windows 8 two years after the launch of Windows 8.1, which would be on October 18th, 2015. Now a new FAQ page says that the final date for Windows 8 support has been moved back a few more months and it will now end on January 12th, 2016.
Mainstream support for Windows 8.1 will end January 9th, 2018 and Extended Support will stop on January 10th, 2023.
Source: Microsoft
/Steve
-
.
5-year-old hacks Xbox, now he's a Microsoft 'security researcher'
The boy got in via a glitch in the password verification screenBy Zach Miners
April 4, 2014 07:48 PM ET
IDG News Service - A 5-year-old San Diego boy has been commended by Microsoft for his security skills after finding a vulnerability in the company's Xbox games console.Kristoffer Von Hasssel's parents noticed earlier this year that he was logged into his father's Xbox Live account and playing games he was not supposed to.
He hadn't stolen his father's password. Instead, he stumbled upon a very basic vulnerability that Microsoft is said to have now fixed.
After typing an incorrect password, Kristoffer was taken to a password verification screen. There, he simply tapped the space bar a few times, hit "enter" and was let into his father's account.
The password allowed him to access not only the games but everything else on the Xbox, including a non-age-restricted YouTube account, his father, Robert Davies, said by telephone Friday.
"I was like, 'Wow, that's so cool,'" Davies said.Despite some who insist that Kristoffer must have had help, Davies said his son indeed accessed the Xbox account on his own.
Perhaps it was in his genes: Davies is a security engineer at the San Diego offices of ServiceNow, an enterprise IT cloud services company.
Davies reported the bug to Microsoft, which fixed it right away.
Kristoffer's name is now listed among Microsoft's March list of security researchers who have disclosed vulnerabilities in its products.
"We're always listening to our customers and thank them for bringing issues to our attention," Microsoft was quoted as saying in the report.Kristoffer received a reward of US$50, a year's subscription to Xbox Live and four games, his father said.
That's a bit less than some other bug finders receive. Microsoft launched several new bounty programs of its own last year, including one that pays up to $100,000 for "truly novel exploitation techniques."
SOURCE: The story was first reported by an ABC News affiliate.
Steve
-
.
Not dead yet: Dutch, British governments pay to keep Windows XP alive
Governments pay Microsoft millions to continue support for “end of life” OS.
Windows XP is supposed to be dead next week. But the Dutch and British governments have both inked deals with Microsoft to continue to keep it on life support, at least for them—under Microsoft’s Custom Support program.
On Wednesday, ComputerWeekly reported that the UK government agreed to pay Microsoft £5.548 million (approximately $9.1 million) for continued support of Windows XP, Office 2003, and Exchange 2003 for all British public sector customers. On Friday, the Dutch government cut its own “multi-million Euro” deal with Microsoft for custom XP support of over 30,000 computers still running the Windows XP operating system.
(Shy's note: Money can indeed buy anything...
 )
)Those deals may be just a drop in the bucket in comparison to what the US government may have to pay for support of the hundreds of thousands of systems still running Windows XP and other end-of-life software. Despite years of foreknowledge of the end of support for the operating system, there are still a large number of systems running Windows XP within government, including computers on sensitive networks and embedded systems. Many hospitals in the US still use Windows XP on workstations and healthcare devices because software developers have not had their products certified by regulators for use with later versions of Windows.
Steve
-
.
Microsoft reveals final Windows XP and Office 2003 security patches
In just five days, Microsoft will release the final updates for Windows XP and Office 2003. Today, the company posted a quick summary of the security bulletins it plans to release on April 8th, including those for XP and Office 2003.
Windows XP will receive a "Critical" update for IE6, 7 and 8, according to the summary, and will also get a patch labeled as "Important" on its own. Windows Server 2003 gets the same updates, but the first one is only been labeled as a "Moderate" patch. Office 2003 gets two patches as well. One is called "Critical" and is designed to fix the exploit found to affect all current versions of Word; the other patch has an "Important" label and fixes an issue in Microsoft Publisher 2003.
As usual, the details behind these security patches have been left out of this advanced bulletin so as to not give any help to potential hackers. However, PC owners who are among the 27.69 percent who still use Windows XP worldwide could face a ton of problems after April 8th as Microsoft won't be releasing any more software updates for the 12 year old operating system.
Source: Microsoft | Image via Microsoft
-
.
24 million routers expose ISPs to DNS-based DDoS attackPosted on 02 April 2014DNS-based DDoS amplification attacks have significantly increased in the recent months, targeting vulnerable home routers worldwide. A simple attack can create 10s of Gbps of traffic to disrupt provider networks, enterprises, websites, and individuals anywhere in the world.

Nominum’s latest research reveals:
- More than 24 million home routers on the Internet have open DNS proxies which expose ISPs to DNS-based DDoS attacks
- In February 2014, more than 5.3 million of these routers were used to generate attack traffic
- During an attack in January 2014, more than 70% of total DNS traffic on a provider’s network was associated with DNS amplification
- DNS is by far the most popular protocol for launching amplification attacks, with more available amplifiers than the next four protocols combined.
Traffic from amplification amounts to trillions of bytes a day disrupting ISP networks, websites and individuals. The impact on ISPs is fourfold:- Network impact generated by malicious traffic saturating available bandwidth
- Cost impact generated by a spike in support calls caused by intermittent service disruption
- Revenue impact as poor internet experience leads to increased churn or retention expenses
- Reputation impact as unwanted traffic is directed toward peers.
"Existing in-place DDoS defenses do not work against today’s amplification attacks, which can be launched by any criminal who wants to achieve maximum damage with minimum effort," explained Sanjay Kapoor, SVP of Strategy, Nominum. "Even if ISPs employ best practices to protect their networks, they can still become victims, thanks to the inherent vulnerability in open DNS proxies."SOURCE: http://www.net-security.org/secworld.php?id=16617
/Steve
-
No April Fools joke on the magic it's here somewhere....
Not sure about smilies. Okay in moderation but some people lack moderation at times. I've been on some forums where you have maybe 1/10 of a page is actual content and 9/10 is animated images and it's on every page.
No worries Ron.. (and congrats to you, for sure..) It's taken me four years but I'm about to catch up to.. and gleefully pass.. "Ms. Smilie" in a few 100 more posts.. (I've been in the Top 20 for almost a year..) *wicked grin*
Steve
-
.
Windows 8.1 Update will be available on April 8 -- here’s what’s new
- By Wayne Williams | 4-02-2014
Microsoft has just unveiled the Windows 8.1 Update at Build, and it will be rolling it out to users of the tiled operating system on April 8. MSDN subscribers can download it today.
Thanks to leaks, we already knew a lot about it, and even posted our thoughts here previously on BetaNews. I called it a Frankenstein product stitched together with compromises, which it undoubtedly is. My colleague Mark Wilson calls it the final nail in Windows 8.1’s coffin, but Brian Fagioli thinks it’s great. You’ll soon be able to try it out for yourself, but in the meantime here’s what it offers.
First up, yes the OS will automatically boot to the desktop if you’re using a keyboard and mouse system. Great news for many people who hate the Modern UI.There are two new buttons on the Start screen next to your username -- Search, which opens the Search charm, and Power, which lets you shutdown, restart, or send your computer to sleep. There’s a new PC Settings button on the Start screen as well, so you don’t have to mess around in Charms if you want to make changes in Windows.
Mouse users can now sort the Start screen in a more traditional way. Right-click an app and a context menu will pop up that will allow you to unpin that item from Start screen and/or taskbar, resize its tile or uninstall it. You can select and move tiles around by holding down Ctrl and selecting a bunch at once.
You can also now pin Windows Store apps to the taskbar by right-clicking an app, or holding down on it, and selecting Pin to Taskbar. The Windows Store app is pinned there by default. The OS can display all running apps on the taskbar.
Windows Store apps now come with a title bar, making it easier to minimize or close them, and split left or right. You can access the taskbar from within running apps. The taskbar also now pops up when you move your mouse to the bottom of a running Modern UI app, so you can easily switch between apps and "legacy" programs.
The store UI is being improved to make it easier to use with the keyboard and mouse too.
If, like me, you prefer to have the Apps screen as the default rather than the Start screen, there’s a new alphabetical view which lets you filter apps by letter.
When you install a new app, it will be highlighted in the Apps list to make it easier to find -- about time!
Finally, Internet Explorer 11 has been tweaked and comes with a new enterprise mode which lets IT managers deal with legacy sites by changing the user agent string, and how ActiveX controls are invoked, re-enable degraded features, and so on.
So that’s what new. What do you think of the changes? If you’ve yet to upgrade to Windows 8.1 will this persuade you to make the leap?
SOURCE: http://betanews.com/2014/04/02/windows-8-1-update-will-be-available-on-april-8-heres-whats-new/
/Steve
-
.
Who’s Behind the ‘BLS Weblearn’ Credit Card Scam?
by Brian Krebs | 3-31-2014
A new rash of credit and debit card scams involving bogus sub-$15 charges and attributed to a company called “BLS Weblearn” is part of a prolific international scheme designed to fleece unwary consumers. This post delves deeper into the history and identity of the credit card processing network that has been enabling this type of activity for years.onlinelearningaccess.com, one of the fraudulent affiliate marketing schemes that powers these bogus micropayments.
At issue are a rash of phony charges levied against countless consumers for odd amounts — such as $10.37, or $12.96. When they appear on your statement, the charges generally reference a company in St. Julians, Malta such as BLS*Weblearn or PLI*Weblearn, and include a 1-888 number that may or may not work (the most common being 888-461-2032 and 888-210-6574).I began hearing from readers about this early this month, in part because of my previous sleuthing on an eerily similar scheme that also leveraged payment systems in Malta to put through unauthorized junk charges ($9.84) for “online learning” software systems. Unfortunately, while the names of the companies and payment systems have changed, this latest scam appears to be remarkably similar in every way.
Reading up on this latest scam, it appears that the payments are being processed by a company called BlueSnap, which variously lists its offices in Massachusetts, California, Israel, Malta and London. Oddly enough, the payment network behind the $9.84 scams that surfaced last year — Credorax — also lists offices in Massachusetts, Israel, London and Malta.
And, just like with the $9.84 scam, this latest micropayment fraud scheme involves an extremely flimsy-looking affiliate income model that seems merely designed for abuse. According to information from several banks contacted for this story, early versions of this scam (in which fraudulent transactions were listed on statements as PLI*WEBLEARN) leveraged pliblue.com, formerly associated with a company called Plimus, a processor that also lists offices in California and Israel (in addition to Ukraine).
The very first time I encountered Plimus was in Sept. 2011, when I profiled an individual responsible for selling access to tens of thousands of desktop computers that were hacked and seeded with the TDSS botnet. That miscreant — a fellow who used the nickname “Fizot” — had been using Plimus to accept credit card payments for awmproxy.net, an anonymization service that was sold primarily to individuals engaged in computer fraud.
Apparently, the Internet has been unkind to Plimus’s online reputation, because not long ago the company changed its name to BlueSnap. This blog has a few ideas about what motivated the name change, noting that it might have been prompted in part by a class action lawsuit (PDF) against Plimus which alleges that the company’s marketing campaigns include the “mass production of fabricated consumer reviews, testimonials and fake blogs that are all intended to deceive consumers seeking a legitimate product and induce them to pay. Yet, after consumers pay for access to any of these digital goods websites, they quickly realize that the promotional materials and representations were blatantly false.” (Much more...)
Continue reading →
SOURCE: https://krebsonsecurity.com/2014/03/whos-behind-the-bls-weblearn-credit-card-scam/
/Steve -
.
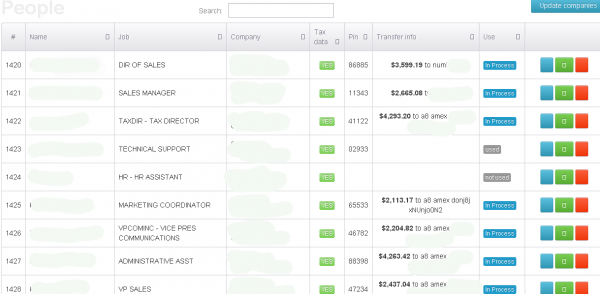
Who Built the ID Theft Service SSNDOB.ru?
by Brian Krebs | 3/27/2014
Previous stories on this blog have highlighted the damage wrought by an identity theft service marketed in the underground called ssndob[dot]ru, which sold Social Security numbers, credit reports, drivers licenses and other sensitive information on more than four million Americans. Today’s post looks at a real-life identity behind the Russian man likely responsible for building this service.
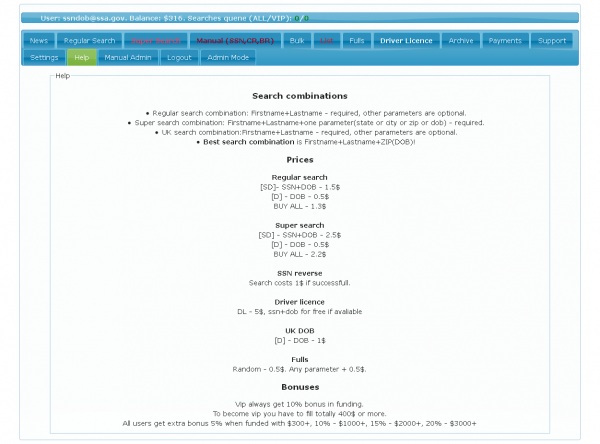
Click on image for easier reading
The administration page of ssndob[dot]ru. Note the logged in user, ssndob@ssa.gov, is the administrator.
Last summer, ssndob[dot]ru (hereafter referred to as “SSNDOB”) was compromised by multiple attackers, its own database plundered. A copy of the SSNDOB database was exhaustively reviewed by KrebsOnSecurity.com. The database shows that the site’s 1,300 customers have spent hundreds of thousands of dollars looking up SSNs, birthdays, drivers license records, and obtaining unauthorized credit and background reports on more than four million Americans.
Private messages and postings on various crime forums show that the service offered at ssndob[dot]ru was originally registered in 2009 at a domain called ssndob-search.info. A historic records lookup purchased from domaintools.com shows that ssndob-search was first registered to an Armand Ayakimyan from Apsheronsk, Russia. This registrant used the email address lxg89@rambler.ru.
In 2013, a copy of the carding forum carder[dot]pro was leaked online. Forum records show that the lxg89@rambler.ru address was used by a member who picked the username “Zack,” and who told other members to contact him on the ICQ instant messenger account 383337. On Vkontakte.ru, a popular Russian social networking site, Mr. Zack is the name of a profile for a 24-year-old Armand Ayakimyan from Sukhumi, a city in western Georgia and the capital of Abkhazia — a disputed region on the Black Sea coast.
Mr. Zack lists his date of birth as August 27 and current town as Sochi, the site of the 2014 Winter Olympics, (although the Mr. Zack account appears to have been dormant for some time). We can see some pictures of Mr. Ayakimyan (DOB: Aug. 27, 1989) at this profile by the same name at promodj.com, a music mixing site. That profile is tied to a group profile created by an Armand Ayakimyan in Sochi.
Mr. Ayakimyan appears to have used a number of different nicknames on various forums, including “Darkill,” “Darkglow” and “Planovoi”. That’s according to the administrators of verified[dot]cm, a top Russian crime forum at which he had apparently created numerous accounts. In an amusing multi-page thread on verified, the administrators respond to multiple member complaints about Plaovoi’s behavior by “doxing” him, essentially listing all of the identifiers that point from various email addresses, ICQ numbers and aliases back to accounts tied to Armand Ayakimyan.
KrebsOnSecurity attempted to reach Ayakimyan via multiple email addresses tied to his various profiles, including Facebook. An individual responding at the main Jabber address used by the operator of SSNDOB — ssndob@swissjabber.ch — declined to comment for this story, saying only “Я против блога. Выберите другой сервис,” or, “I am against the blog. Choose another service.” This reply came immediately after the user of this profile updated his status message notifying customers that his identity theft service was just freshly stocked with a huge new update of personal data on Americans.
The conclusion that Ayakimyan is/was involved with the operation of SSNDOB is supported with evidence gathered from Symantec, which published a blog post last week linking the young man to the identity theft service. According to Big Yellow, Ayakimyan is but one of several men allegedly responsible for creating and stocking the ID theft bazaar, a group Symantec calls the “Cyclosa gang.” From their report: (Much more...)
SOURCE: https://krebsonsecurity.com/2014/03/who-built-the-id-theft-service-ssndob-ru/
/Steve
-
Thanks for the post Steve.

Always a pleasure Arthur..



Celebrating 40K posts
in General Chat
Posted
Doctor plus wife have me on a special diet - no more Tootsie Roll Pops (along with 90% of the other actual food I like.. ) ..
) ..
Life sucks.. (Beats the alternative tho')