-
Posts
5,501 -
Joined
-
Last visited
Content Type
Events
Profiles
Forums
Posts posted by ShyWriter
-
-
Danke !
I don't know you guy's opinion on this but I'm one of those people that keep my system more, or less, updated and anyone still running Java SE 7 Update 21 and earlier deserve what they get.

In other words I DON'T suffer fools gladly.. (And I'm kind of a nice person... in most cases.)

Steve
-
.
Compliments of Wiley Miller:

Steve
-
.
Two-thirds of Americans surf the Web at less than 10Mbps
Average speed improved in nearly every state (sorry, Ohio).by Jon Brodkin - Jan 28 2014, 5:21pm EST

Despite Internet speed improvements in nearly every state, most US residents are still surfing the Web at less than 10Mbps, according to Akamai's latest State of the Internet Report.
Drawing data from Akamai's globally distributed network of servers, the report covering Q3 2013 put the US in 9th place worldwide in the proportion of residents with "high broadband," or at least 10Mbps average download speeds:
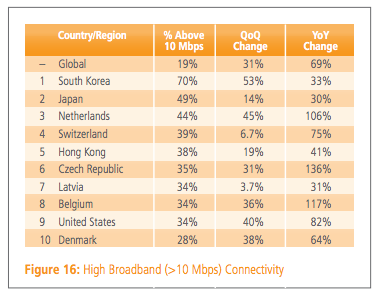 Akamai
AkamaiNOTE: Regular broadband is defined as 4Mbps—75 percent of US connections hit that mark.
Akamai's data from its Internet content delivery network includes 158.5 million unique IP addresses in the US, and many millions more in countries around the world.
"The global average connection speed continued its upward trend in the third quarter of 2013, climbing 10 percent over the previous quarter to 3.6Mbps," Akamai said in a press release. "A total of 122 countries/regions that qualified for inclusion saw average connection speeds increase during the third quarter, with growth ranging from 0.5 percent in Namibia (to 1.1Mbps) to a 76 percent increase in Nepal (to 3.6Mbps)."Akamai measured both the average speed of Internet connections and the average peak speed, which may not be representative of typical experience but is "more representative of Internet connection capacity." (More...)
Continued at: http://arstechnica.com/information-technology/2014/01/two-thirds-of-americans-surf-the-web-at-less-than-10mbps
/Steve
-
.
Java-based malware hits Windows, Mac and LinuxPosted on 29.01.2014Kaspersky Lab researchers have recently analysed a piece of malware that works well on all three of the most popular computer operating systems - the only thing that it needs to compromise targeted computers is for them to run a flawed version of Java.

The Trojan is written wholly in Java, and exploits an unspecified vulnerability (CVE-2013-2465) in the JRE component in Oracle Java SE 7 Update 21 and earlier, 6 Update 45 and earlier, and 5.0 Update 45 and earlier.
Shy's note: Latest Oracle Java SE 7 Update 51 is NOT affected by this malware.
Once the malware is launched, it copies itself into the user’s home directory and sets itself to run every time the system is booted. It then contacts the botmasters' IRC server via the IRC protocol, and identifies itself via a unique identifier it generated.
The malware's main reason of existence is to make the infected machine flood specified IP addresses with requests when ordered to via a predefined IRC channel. The botmasters simply have to define the address of the computer to be attacked, the port number, the duration of the attack, and the number of threads to be used in it.
At the time of analysis, the botnet formed by machines "zombified" by this particular Trojan was targeting a bulk email service.
SOURCE: https://www.net-security.org/malware_news.php?id=2693
/Steve
-
Here is a tool to test speed results for DNS you may be interested int.
Good ol' Steve Gibson.. (author of the mentioned DNS Benchmark program)
 Wish I was smart as he is (without his attitude) and could code in assembly language..
Wish I was smart as he is (without his attitude) and could code in assembly language..That guy is one of those obnoxious "geniuses" that is both brilliant and narcissistic as well as a pain in M$'s (mostly) and others injustices when it comes to holes in software, etc.. I've "known" that guy since the earliest days of SPINRITE, his main claim to fame and money generator. I used to use his stuff all the time but hadn't heard him doing anything recently until this DNS program. I'm running it now after I changing from Time Warner's DNS servers t
o @David's GTE DNS (same #'s as he's using)to one of the OpenDNS and one of the BHN DNS after running the time-lag/optimize for DNS program from Gibson. :blush:
:blush:Thanks for the info @Ron.. and @David..
Steve
-
.
Google Fiber: Why you need to get online 100 times faster
I’ve seen the future. It’s called gigabit Internet by Google Fiber, and it just launched in my hometown of Provo, Utah, the second of three scheduled cities to get speeds that are 100 times faster than the rest of America.
“What good is really fast Internet if the content stays the same?” you may ask yourself. I certainly did, before testing the service. Besides, my “high speed” Internet from Comcast seemed fast enough, enabling my household to stream HD videos, load web pages quickly, and connect multiple devices as needed, largely without hiccup.
I was wrong.
Using gigabit Internet, even in its infancy, opened my eyes to speed and reminded me of why I love the Internet.
Most of us are conditioned to endure slow Google Maps, for example, even though we don’t realize it. We expect them to load in chunks when we zoom. We expect Street View to load sluggishly. We’re patient with satellite view because it’s cool, and because it requires patience to use. So we wait. And wait.
With gigabit Internet, maps load instantaneously. The performance is startling. I zoomed in on Manhattan from space faster than I could have fallen on it — no blurs, granulized lines or pixels. Just incredible speed and clarity.
Then I streamed 10 full HD videos in separate browsing tabs from YouTube -- with nary a loading bar in sight. They all ran without the slightest screen tear.
“Why would anyone want to watch 10 videos at once?” you ask. One person wouldn’t. But many people would. If you’re a household of 10 and everyone wants to stream their own movie on their own device, they can.
Capacity is the point. With Google Fiber, there’s no more bandwidth rationing, unless you opt for Google’s Free Fiber. That service is good for only one device, but still good enough for a single HD stream, according to users I spoke to. Not bad for free.
Other everyday web pages load with a bit more pop, but that might have been the stars in my eyes. Or it could have been the 915 megabits per second (both up and down!) I independently clocked, which is more than 120 times faster than the average U.S. broadband connection (8.6 Mbps), and more than double the fastest download speed and nine times the fastest upload speed of Verizon FiOS, the largest fiber optic Internet provider in the country. (More...)
Read the rest at : http://www.foxnews.com/tech/2014/01/24/google-fiber-why-need-to-get-online-100-times-faster/
/Steve
-
.
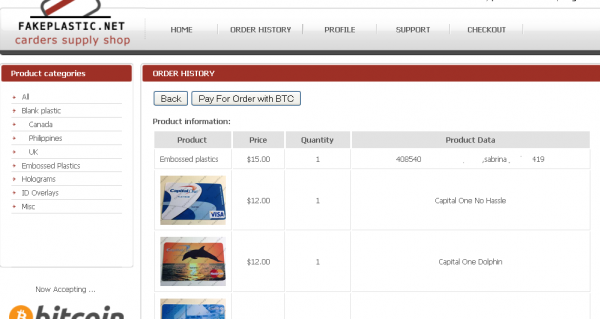
Feds Infiltrate, Bust Counterfeit Card Shop
Federal authorities in New Jersey announced a series of arrests and indictments of 14 individuals thought to be connected to an online one-stop shop selling embossed, counterfeit credit cards and holographic overlays.
According to documents released by prosecutors in New Jersey and North Carolina, the men ran or otherwise profited from the Web site fakeplastic[dot]net, which specializes in selling high-quality, custom-made counterfeit credit and debit cards, as well as holographic overlays used to create fake driver’s licenses.
A customer’s purchases from fakeplastic[dot]net, which federal authorities secretly seized on Dec. 5, 2013.
The FBI and the U.S. Postal Investigative Service began investigating fakeplastic[dot]net in January 2013. Charged with running the site is 39-year-old Sean Roberson of Palm Bay, Fla. Investigators allege that Roberson began selling counterfeit cards in April 2011, and launched the site in June 2012. (More....)
Continue reading at: https://krebsonsecurity.com/2014/01/feds-infiltrate-bust-counterfeit-card-shop/
/Steve
-
.
Oracle and Java, Apple and the FTC, Google and privacy - 60 Sec Security
by Paul Ducklinon January 18, 2014Filed Under: Adobe, Apple, Featured, Google, iOS, Malware, Microsoft, Oracle, Privacy, Security threats, Video, Vulnerability
60 Second Security:
• Why was this month's Java update a "must patch"?
• Should in-app purchases be allowed to target children?
• Is it a good idea to give Google control of your home?
Find all the answers in 60 Second Security for 18 January 2014.
Found in this episode:
- Patch Tuesday January 2014 - Microsoft, Adobe and Oracle
- Apple settles over shabby sales security in the App Store
- Google pays $3.2 billion for Nest, a smart-home gadget maker
/Steve
-
.
ATM/WinXP is nothing folks; MOST stores POS run WinXP embedded in homegrown software..
[...]
It’s not clear what type of software powers the point-of-sale devices running at registers in Target’s U.S. stores, but multiple sources say U.S. stores have traditionally used a home-grown software called Domain Center of Excellence, which is housed on Windows XP Embedded and Windows Embedded for Point of Service (WEPOS). Target’s Canadian stores run POS devices from Retalix, a company recently purchased by payment hardware giant NCR. According to sources, the Retalix POS systems will be rolled out to U.S. Target locations gradually at some point in the future.
[...]
SOURCE: https://krebsonsecurity.com/2014/01/a-first-look-at-the-target-intrusion-malware/
Read the complete article for more context as well as his 2 follow-up articles
/Steve
-
95% of ATM machines still use Windows XP, and will be exposed to vulnerabilities after April 8th, 2014

The world's ATM machines will soon face a major issue on April 8th: The end of support for their operating system. According to BusinessWeek, 95 percent of active ATMs in the world, or nearly all of the 420,000 currently operating in the United States, run on Windows XP - a system which Microsoft is officially ending support for in under 90 days.
Despite being one of the most frequently used consumer technologies in the world, many ATMs run on outdated operating systems. and with the April 8th deadline looming, their owners must make the upgrade. But this may be easier said than done for many of the machines, which run on outdated hardware that may struggle to keep up with a newer OS, like Windows 7. According to Suzanne Cluckey, the editor of ATM Marketplace,
"A lot of ATMs will have to either have their components upgraded or be discarded altogether and sold into the aftermarket—or just junked."The machines that aren't promptly upgraded could face significant security vulnerabilities as more and more weak points in the OS are uncovered. And while Microsoft promised to continue support for Microsoft Security Essentials until 2015, the operating system as a whole will still lack regular security patches - something which could end badly for the machines which thousands deposit cash into every day. Small shops which lack the resources available to larger businesses would be hit the hardest, as they're the slowest to change. And while consumers are protected under industry protections, those operating the machines will be hit the hardest by any malicious attacks.
Hopefully ATM operators will heed these warnings and upgrade as soon as possible: The malware infection rate for Windows XP is already almost six times higher than Windows 8 systems, and despite pleas from the Chinese government for Microsoft to continue support, and a warning to the Indian banking industry that details 'major risks' if they don't switch operating systems, those less than tech-savvy operators may still see their ATMs face a significant threat.
Source: BusinessWeek | Image via Shutterstock - ATM Machine
/Steve
-
.
It's official: Winamp (and Shoutcast) saved via Radionomy purchase
For a while, it was not looking good for Winamp. Its long time owner AOL announced a couple of months ago it would shut down development of the popular media player software on December 20th. However, that day came and went with the Winamp player and website still online and working, fueling Internet rumors that a deal to acquire the software was in the works.
Today, the Internet streaming audio company Radionomy confirmed previous rumors that it has bought Winamp from AOL, along with its related Shoutcast streaming audio service. Financial terms of the deal were not disclosed, but TechCrunch claims, via unnamed sources, that Radionomy paid between $5-10 million for the properties and AOL also bought a 12 percent stake in the company.
Radionomy launched in 2008 and in addition to letting users listen to Internet radio stations, it also offers tools to let people create their own online music or talk show stations they can host themselves. The company claims it currently has 13 million unique listeners.
In today's press release, Radionomy CEO Alexandre Saboundjian stated they plan to develop "new functionalities" for Winamp "dedicated to desktop, mobile, car systems, connected devices and all other platforms." The acquisition of Shoutcast will also expand Radionomy's U.S. presence, with the company claiming that it will now be able to offer its listeners access to "approximately half of all streamed internet radio worldwide."
Source: TechCrunch | Image via Winamp
/Steve
-
-
.
Just My Imagination
https://www.youtube.com/watch?v=dE8naMEJk9Y
Gwyneth Paltrow with Babyface (in HD)
-
.
Free Window-Eyes reading software offered for Microsoft Office 2010 and 2013 users
Microsoft is offering a new way for visually impaired users of its Office software a better way to interact with its tools, thanks to a newly revealed agreement with GW Micro. The two companies announced today that the Window-Eyes screen reading software from GW Micro will now be offered for free for owners of Microsoft Office 2010 and 2013, along with paid subscribers to Office 365. Financial terms of this deal were not disclosed.
The WindowEyesForOffice.com website has more details on this free software offer, which will enable visually impaired users to access Word, Excel, PowerPoint, OneNote and Outlook via computer speech or Braille in over 15 languages. In a press release, GW Micro believes offering better access to software like Window Eyes will become more important in the years to come "as the number of people with age-related macular degeneration and other retinal degenerative diseases increases."
In its own press release, Microsoft stated, "Whether people want to use Office at home, school or work they now have more flexibility and an improved opportunity to take advantage of our latest software innovations." Microsoft Speech Platform will be the default synthesizer for Window Eyes but additional voices can be purchased if the robotic tone of the default is not to the user's liking.
-
.
Microsoft: You will still need to activate Windows XP after April 8th with a fresh install
When Windows 7 was released in 2009, some of its SKUs included a feature called "XP mode". In the simpliest terms, the Professional, Enterprise and Ultimate versions of Windows 7 could allow older Windows XP programs to run in a simulated environment; the idea was to help small businesses make the transition from XP to 7 easier.

With Windows XP now set to lose all security and software update support from Microsoft on April 8th, some Windows 7 users might be wondering about the future of "XP mode" as well. ZDNet reports that, according to a statement from Microsoft, the company has no plans to release a patch for Windows 7 that does away with "XP mode".
Having said that, Microsoft states that people who continue to use that feature to run older programs in Windows 7 could still face security risks because Windows XP won't get any more updates in less than three months. In other words, it's best to simply stop using "XP mode" after April 8th.
ZDNet also reports that if, for some reason, you want to install Windows XP on your PC after April 8th, Microsoft will still require that the OS be activated before it can run on your computer. A spokesperson said,
"Computers running Windows XP will still work, they just won’t receive any new security updates. Support of Windows XP ends on April 8, 2014, regardless of when you install the OS."Source: ZDNet | Image via Microsoft
/Steve
-
.
Oracle preps 147 security patches, including 36 for Java
Many of the Java weaknesses can be exploited remotely, according to OracleBy Chris Kanaracus
January 10, 2014 02:48 PM ET
IDG News Service - Oracle is about to release one of its largest security patch batches in recent memory, with some 147 fixes coming Tuesday for vulnerabilities in Java SE, its flagship database, business applications and assorted other products.Tuesday's release will contain 36 fixes for Java SE, according to a pre-release announcement posted on Oracle's website this week. Thirty-four of the weaknesses being targeted can be exploited by an attacker over a network without the need for authentication, Oracle said.
Some 25 fixes will be released for various products in Oracle's Fusion Middleware catalog, including WebCenter and GlassFish Server. Twenty-two of them concern weaknesses that can be remotely exploited without the need for a user name and password.
Sixteen patches in Tuesday's set are aimed at Oracle's supply chain software, with six of them remotely exploitable without authentication. Another 17 fixes will be issued for PeopleSoft applications, five for Oracle's database, 11 for the Solaris OS, and nine for Oracle's virtualization software.
There will be five patches for Oracle's database, as well as 18 for MySQL, according to the announcement.
Oracle issued 127 patches in its last release, which came in October. That update included 51 fixes for Java./Steve
-
.
Hackers Steal Card Data from Neiman Marcus
Responding to inquiries about a possible data breach involving customer credit and debit card information, upscale retailer Neiman Marcus acknowledged today that it is working with the U.S. Secret Service to investigate a hacker break-in that has exposed an unknown number of customer cards.
Earlier this week, I began hearing from sources in the financial industry about an increasing number of fraudulent credit and debit card charges that were being traced to cards that had been very recently used at brick-and-mortar stores run by the Dallas, Texas based high-end retail chain. Sources said that while it appears the fraud on those stolen cards was perpetrated at a variety of other stores, the common point of purchase among the compromised cards was Neiman Marcus.
Today, I reached out to Neiman Marcus and received confirmation that the company is in fact investigating a breach that was uncovered in mid-December.
Neiman Marcus spokesperson Ginger Reeder said the company does not yet know the cause, size or duration of the breach, noting that these are questions being sought by a third-party forensics firm which has yet to complete its investigation. But she said there is no evidence that shoppers who purchased from the company’s online stores were affected by this breach.
The entirety of the company’s formal statement is as follows:
“Neiman Marcus was informed by our credit card processor in mid-December of potentially unauthorized payment card activity that occurred following customer purchases at our Neiman Marcus Group stores.
We informed federal law enforcement agencies and are working actively with the U.S. Secret Service, the payment brands, our credit card processor, a leading investigations, intelligence and risk management firm, and a leading forensics firm to investigate the situation. On January 1st, the forensics firm discovered evidence that the company was the victim of a criminal cyber-security intrusion and that some customers’ cards were possibly compromised as a result. We have begun to contain the intrusion and have taken significant steps to further enhance information security.
The security of our customers’ information is always a priority and we sincerely regret any inconvenience. We are taking steps, where possible, to notify customers whose cards we know were used fraudulently after making a purchase at our store.
The disclosure comes as many in the retail sector are seeking more information about the causes of the breach at nationwide retail giant Target, which extended from around Thanksgiving 2013 to Dec. 15, and affected some 40 million customer debit and credit cards. (Hackers also pilfered personal data on additional 70 million Target customers)[More...]
/Steve
-
.
Intel dropping the McAfee brand for consumer products
Intel has started dropping the McAfee brand name from its consumer security products and will be using the "Intel Security" moniker instead.
McAfee, the iconic security software company of the 80s and 90s was acquired by Intel in 2010. However, until now Intel did not make any changes to the McAfee brand which was synonymous with security for most users who used it for decades. Now, in light of recent antics of McAfee's founder John McAfee, the brand seems to have taken a hit and Intel is cautiously moving away from the name as observed from the company's keynote at the Consumer Electronics Show 2014, last night.

The rebranding which is expected to complete over the next year, will cover McAfee's consumer security suite "McAfee Security" which will now be known as "Intel Security" but will continue to have the famous "shield" logo. The software will still remain unchanged and will be developed for more platforms in the future. Intel CEO, Brian Krzanich, announced that, "Intel is bringing its award-winning mobile security to every mobile device, phones, tablets, wearables." Intel is planning to introduce Intel Device Protection app for mobile devices later this year, aimed at protecting people using those devices at work.
Intel is yet to officially announce the phase-out but in response to CNET's request for a comment, an executive for the company has revealed that there will be more to share in the coming months.
Source: CNET | Image via MaximumPC
/Steve
-
.
Critical backdoor in Linksys and Netgear routers foundPosted on 03 January 2014.
A backdoor in some Linksys and Netgear wireless routers that allows malicious users to reset the devices' configuration to factory settings and, therefore, to default router administration username and password, has been discovered and its existence shared with the world.
French security systems' engineer Eloi Vanderbeken has first discovered the backdoor in his own Linksys WAG200G wireless DSL gateway, after deciding to limit the bandwidth used by his holiday guests and remembering he forgot the complex username and password combination he chose for accessing the router's administration panel.
By probing and prodding the device's firmware, he discovered that there was an unknown service listening on network port TCP 32764. The service accepts thirteen types of messages, among which are two that allowed him to peak into the configuration settings, and one that restored the router to its default factory settings.
After sharing the colourful details of his "quest" on his Github account, other hackers around the world took it upon themselves to check what other routers have the same backdoor.
Unfortunately, there are quite a few. The list allowed people to speculate that the affected devices have one thing in common: they have been manufactured by Sercomm, a firm that builds routers both under its own name and for several other companies, including Linksys and Netgear.
Other companies Sercomm works for are 3Com, Aruba and Belkin, so it's likely that those devices also sport the flawed firmware. Hopefully all of these companies will be pushing out a patched version as soon as possible.
SANS ISC CTO Johannes Ullrich has noted that since the revelation of the existence of the backdoor, they have been seeing an increase in probes for port TCP 32764.
"Our data shows almost no scans to the port prior to today, but a large number from 3 source IPs today. The by far largest number of scans come from 80.82.78.9. ShodanHQ has also been actively probing this port for the last couple of days," he shared.
"At this point, I urge everybody to scan their networks for devices listening on port 32764/TCP. If you use a Linksys router, try to scan its public IP address from outside your network."
Sophos' Paul Ducklin also offered good advice on what to do and check.SOURCE: https://www.net-security.org/secworld.php?id=16155
/Steve
-
.
Has Winamp been sold to Radionomy?
John Callaham 12 hours ago
The Winamp media player and its associated website were supposed to be shut down on December 20th by its current owner AOL, but as we have reported before both the application and the site continued to stay alive past that deadline. Meanwhile, rumors about a acquisition of Winamp have continued for the past several weeks.
Now there's more evidence pointing towards the possible buyer. A member of Winamp's forums noticed late on Tuesday that the domain name servers for Winamp.com have been switched from AOL to Radionomy, a streaming music and radio service.
Neowin has confirmed that the domain servers for Winamp.com are now under Radionomy's control via a WHOIS search, although the actual website ownership still technically remains in AOL's hands at the moment. We have emailed both AOL and Radionomy for comment.
Radionomy launched in 2008 thanks to four Belgium entrepreneurs in Europe; it became widely available in the US in 2012. Unlike other streaming music services like Pandora or Spotify, Radionomy also offers tools to let users create their own online music or talk show stations they can host themselves. It gets revenues from those stations by requiring them to run four minutes of ads every hour. The service claims to have 13 million unique listeners.
Source: Network Solutions via Winamp forums | Image via Winamp
/Steve
-
.
Target: Encrypted PIN numbers taken in recent credit card data theft
Last week, retailer Target announced that 40 million credit and debit card numbers had been taken from its database. So far, the identities of the people behind the cyber attack are still unknown but today Target revealed the theft also involved the PIN numbers that were linked to those cards.

In theory, the thieves who took the PIN numbers could use them in combination with the credit card data to make withdrawals from customer bank accounts. However, Target's statement today claims that the numbers are "strongly encrypted", adding that the encryption key needed to unlock those PINs is part of an external and independent payment database.
Target said, "The most important thing for our guests to know is that their debit card accounts have not been compromised due to the encrypted PIN numbers being taken."The credit card data was taken from Target's servers between November 27th and December 15th. The Krebs on Security website, which first broke the story of the Target cyber attack, says that many of those credit card numbers are now being distributed in underground online shops frequented by hackers.
Target has said it plans to offer free credit monitoring to the customers that have been affected by this incident but details have not been announced.
Source: Target | Credit card encrypt image via Shutterstock
via SOURCE: http://www.neowin.net/news/target-encrypted-pin-numbers-taken-in-recent-credit-card-data-theft
/Steve
-
Me, or Brian Krebs?

You, you stinker!



I could never stay mad at you @Amethyst... *wry smile* (as for Brian; the man, is a very good writer and researches his topics well.
 )
) Merry Christmas kiddo,
Best to you and yours,
Steve
-
http://krebsonsecurity.com/2013/12/whos-selling-credit-cards-from-target/
Wow. Maybe all these Target threads can be combined?
Troublemaker -

Steve
-
.
Weak U.S. card security made Target a juicy target
- Associated Press
Sunday, December 22, 2013 10:31pm
NEW YORK — The United States is the juiciest target for hackers hunting credit card information. And experts say incidents like the recent data theft at Target's stores will get worse before they get better.
That's in part because U.S. credit and debit cards rely on an easy-to-copy magnetic strip on the back of the card, which stores account information using the same technology as cassette tapes.
"We are using 20th century cards against 21st century hackers," said Mallory Duncan, general counsel at the National Retail Federation. "The thieves have moved on, but the cards have not."In most countries outside the United States., people carry cards that use digital chips to hold account information. The chip generates a unique code every time it's used. That makes the cards more difficult for criminals to replicate. So difficult that they generally don't bother.
"The U.S. is the top victim location for card counterfeit attacks like this," said Jason Oxman, chief executive of the Electronic Transactions Association.
The breach that exposed the credit card and debit card information of as many as 40 million Target customers who swiped their cards between Nov. 27 and Dec. 15 is still under investigation. It's unclear how the breach occurred and what data, exactly, criminals have.
Companies haven't further enhanced security because it can be expensive. And while global credit and debit card fraud hit $11.27 billion last year, those costs accounted for just 5.2 cents of every $100 in transactions, according to the Nilson Report, which tracks global payments.
Another problem: Retailers, banks and credit card companies each want someone else to foot most of the bill. Card companies want stores to pay to improve their internal systems. Stores want card companies to issue more sophisticated cards. Banks want to keep the profits they get from older processing systems.
Card payment systems work much the way they have for decades. The magnetic strip on the back of a credit or debit card contains the cardholder's name, account number, the card's expiration date and a security code different from the three or four-digit security code printed on the back of most cards.
When the card is swiped at a store, an electronic conversation is begun between two banks. The store's bank, which pays the store right away for the item the customer bought, needs to make sure the customer's bank approves the transaction and will pay the store's bank. On average, the conversation takes 1.4 seconds.
During that time the customer's information flows through the network and is recorded, sometimes only briefly, on computers within the system controlled by payment processing companies. Retailers can store card numbers and expiration dates, but they are prohibited from storing more sensitive data such as the security code printed on the backs of cards or other personal identification numbers.
Hackers have been known to snag account information as it passes through the network or pilfer it from databases where it's stored. Target says there is no indication that security codes on the back of customer credit cards were stolen. That would make it hard to use stolen account information to buy from most Internet retail sites. But the security code on the back of a card is not needed for in-person purchases. And because the magnetic strips on cards in the United States are so easy to make, thieves can simply reproduce them and issue fraudulent cards.
"That's where the real value to the fraudsters is," said Chris Bucolo, a senior manager at ControlScan, which helps merchants comply with card processing security standards.
Once thieves capture the card information, they check the type of account, balances and credit limits, and sell replicas on the Internet. A simple card with a low balance and limited customer information can go for $3. A no-limit card can go for $1,000, according to Al Pascual, a senior analyst at Javelin Strategy and Research, a security risk and fraud consulting firm.
Credit card companies in the United States have a plan to replace magnetic strips with digital chips by the fall of 2015. Retailers worry the card companies won't go far enough. They want cards to have a chip, but they also want each transaction to require a personal identification number, or PIN, instead of a signature, to increase security.
SOURCE: TampaBayTimes / APNews
/Steve



Speed dating for lawyers..
in Tailwaggers and Jokes
Posted
*grin*
Thanks!