-
Posts
5,501 -
Joined
-
Last visited
Content Type
Events
Profiles
Forums
Posts posted by ShyWriter
-
-
Me too! And the FIX IT doesn't do diddly..


-
2.00.0.0503 Installed/working OK for me. MBAM2 notified me that an update was available and I hit enter.. Install asked if I wanted to exit old version to complete new version and did it for me on affirmative input. Database out-of-date notification and entered yes for update. Updated OK; retained settings; license..

Steve
-
The inference was that you didn't write it, and were not responsible for the horrible spelling and grammatical mistakes in the article.

Oh.. Well in that case, thank you..


 Along those lines if I see a typo or a word or two misspelled in an article I will correct it but in the majority of cases, this one being an example, I leave 'em alone as I sometimes can't believe them or they way they're written myself.
Along those lines if I see a typo or a word or two misspelled in an article I will correct it but in the majority of cases, this one being an example, I leave 'em alone as I sometimes can't believe them or they way they're written myself.  In the Software sub-Forums I will make an extra effort to correct the descriptions or fixes or other verbiage if the software site/author is obviously a non-English, first language speaker.
In the Software sub-Forums I will make an extra effort to correct the descriptions or fixes or other verbiage if the software site/author is obviously a non-English, first language speaker. 
Cheers,
Steve..
-
The one you copied and pasted.
The TechEye one then.. I'm not sure I like the inference in the way you said "copied and pasted" Arthur.. I never take credit for others work and the source is always listed! If you have a problem with the way I present information I'd be happy to stop posting altogether.
Have a NICE day
-
Which article; the TechEye original or the link within it??
Upon further research by myself, it appears DELL has been denying warranty repair on speakers since early 2012, mostly on laptops, but starting in 2013 with desktops, still blaming VLC for the problem.. Regardless; the gist of the situation is that VLC is a media player NOT an audio amplifier, thus nothing goes out greater than whatever is input by DELL's speaker board/chip..
Steve
-
They must the the USB Powered Speakers. Only they would need a BIOS update.
However, USB 5v @ 1amp = 5W or 2.5W /speaker. Where do they get the 10W value and to say that the audio is putting out 11W ?
Another reason to use powered speakers which employ their own power supply.
Dave,
They're saying the Dell Sound CARD puts out 10W max.. (5w per channel??)
DELL does make cheap crap which is why I stopped buying DELL in 1996.. (Bought wife's Walmart Special "DELL" in 2008; meant I don't buy for MY use..
 ) BTW; her USB speakers are rated at 5V @0.5A which is 2.5W per speaker input rating.
) BTW; her USB speakers are rated at 5V @0.5A which is 2.5W per speaker input rating.BUT; I agree with you on this point.. I use powered speakers on all my personal computers.
Steve
-
.
VLC slams cheap and nasty Dell speakers
Dell bans VLC software
10 Feb 2014 09:50 | by Edward Berridge

Tin box maker Dell has been accused of blaming the damage of its "poor quality speakers" on a popular open sauce media outfit.
Dell customer support pages issued a warning over the weekend claiming that if you installed the VLC player your warranty would be voided. They claimed that the software was blowing up Dell's speakers.
VLC has a feature that can make the audio go to 11 and much louder than other players, Dell claimed. VLC achieves this by using a process that creates hard which can damage small speakers. Dell has tested VLC and verified that the speakers can be damaged after several hours of using VLC.
However, an unnamed lead developer for VLC, said here that the story is just rubbish and this is just Dell putting crap components on their machine and blaming others. In fact VLC uses the same standards as the official APIs.
VLC just uses the Windows APIs (DirectSound), and sends signed integers of 16 bits to the Windows Kernel and it allows amplification of the INPUT above the sound that was decoded.
But this is exactly the same if you put your mp3 file through Audacity and increase it and play with WMP, or if you put a DirectShow filter that amplifies the volume after your codec output. For example, for a long time, VLC ac3 and mp3 codecs were too low (-6dB) compared to the reference output.
The worse thing that will happen is that it will reduce the dynamics and saturate a lot, but this is not going to break your hardware.
The developer said that VLC does not modify the OUTPUT volume to destroy the speakers. VLC is software using the OFFICIAL platforms APIs.
He claimed that Dell sound cards output power that Dell speakers cannot handle. Dell's sound card outputs at max 10W, and the speakers only can take 6W in, and neither their BIOS or drivers block this.
The developer said that it would be more logical for Dell to void warranties for anyone who listens to heavy metal. Dell should insist that people only listen to Céline Dion music, because Metal saturates more
.
What is interesting is that Dell has been providing users with a BIO update to fix the problem, which seems to suggest that VLC is not to blame. It is just they are using speakers which are too low power.
SOURCE: http://news.techeye.net/software/vlc-slams-cheap-and-nasty-dell-speakers
Steve
-
.
As usual, Florida can beat that. Several years ago, before I retired, a local, hometown, Bubba Bob cop ticketed a Fireman/Driver for parking his Fire Truck on the "shoulder" of the road and refusing to move it during an accident incident involving four cars that was still on-going.
Yep; good, old Florida.. We shoot people that throw popcorn at us; we are the Pill Mill Capital of the 50-states; we still have a town named Starke that the AAA tells all drivers to avoid like the ticket-writing, speed trap it is; we have met the enemy and it is us..

Glad I was born in Tennessee..

Steve
-
.
First there were CAPTCHAs, now there are GOTCHAs
New system uses abstract art to hide passwords.
by Yogi Patel
Feb 7 2014, 10:30am EST
 An example of one of the "inkblot" images used by the GOTCHA system.
An example of one of the "inkblot" images used by the GOTCHA system.Luis von Ahn and colleagues developed CAPTCHAs (Completely Automated Public Turing test to tell Computers and Humans Apart) in early 2000 to help fight against computer-generated spam. The test requires users to type in letters from a distorted image to prove that they're human. This system worked great for years, but as with many things on the Internet, there's always a hacker who wants to break the system.
Hackers have found ways to crack the CAPTCHA system—one example involves tricking users into thinking they are entering a CAPTCHA at a completely safe website while the user’s input is used to access another site. So it's up to the computer scientists to figure out how to beat the hackers again.
That's exactly what a team of researchers at Carnegie Mellon University set out to do. (The team consisted of PhD student Jeremiah Blocki, professor Manuel Blum, and associate professor Anupam Datta) The system they developed is called GOTCHA (Generating panOptic Turing Tests to Tell Computers and Humans Apart), and it uses a user-provided password to generate several multi-colored inkblots, with the blotches distributed randomly.
The user describes each inkblot with a text phrase, and the words in the phrase are then stored in random order, along with the password. When the user wants to sign in with the password, the inkblot and a set of descriptive phrases are shown. The user matches the inkblot and the phrase to complete the sign-in. In order to crack the user’s password offline, the hacker must know the user’s password and corresponding puzzle because the GOTCHA system requires real-time interaction with a human to solve the puzzle, says Datta.
GOTCHAs are small puzzles that are easy for humans to solve, but difficult for computers, says Blocki. Similar to CAPTCHAs, they rely on the human visual system to recognize patterns, making it difficult for computers and automated systems to beat. Their purpose, unlike CAPTCHAs, is to increase the security of passwords and make it difficult for anyone other than the creator to access an account.
To help test the robustness of their new method, the researchers are inviting fellow security researchers to use artificial intelligence techniques to crack the GOTCHA system at their online challenge. Three of the challenges have already been released on their website, and there are plans to release more.
SOURCE: http://arstechnica.com/science/2014/02/first-there-were-captchas-now-there-are-gotchas/
/Steve
-
.
Comcast web mail servers hacked, all users at risk

Hacking group NullCrew FTS declared today that it had exploited a security flaw in Comcast’s Zimbra webmail server. It’s believed that the group used what is known as a LFI exploit or local file inclusion vulnerability to obtain usernames and passwords of Comcast ISP users.
The hacking group claims it used this exploit to gain access to the Zimbra LDAP and MySQL database which house the user accounts and passwords. The group posted earlier on pastebin.com a list of what they gained access to, but with no usernames or passwords listed. The posting has since been removed by pastebin.
Every Comcast ISP user has a master account, which is accessible through their Zimbra webmail site. This account can be used to access your payment information, e-mail settings, user account creation and services you purchase from Comcast. Even if you do not use their mail service, you still will have a master account. It is strongly recommended that, if you are a Comcast user, you change your password as soon as possible.
Comcast performed out-of-schedule maintenance on their mail servers last night, hopefully to fix this exploit. No more information is available at this time on what maintenance was performed.
Source: ZDNet
/Steve
-
.
Two 'critical,' three 'important' Microsoft security patches coming Tuesday

In January, Microsoft didn't release any software security patches that it labeled as "critical" during its monthly "Patch Tuesday" event, but this month the company has announced that it will release two security updates with the "critical" branding on Tuesday, Feb. 11, along with three others that have been deemed "important."
Of the two "critical" patches, Microsoft's summary page says that one of them affects Windows 7, Server 2008 R2, 8/8.1, Server 2012/2012 R2 and RT/RT 8.1. The other "critical" update is just for one program, Microsoft Forefront Protection 2010 for Exchange Server. The three "important" updates are for all currently supported versions of Windows, including Windows XP. As we have reported extensively, Microsoft plans to cut off all software updates to XP on April 8. As usual, Microsoft does not offer any details of what thesepatches are designed to fix in these early summary reports, in order not to tip off hackers ahead of time.
In addition to these patches, Microsoft has already announced that it will release an automatic software update for its Xbox One console on Feb. 11, which will add a few new features, such as a storage management system. It's also expected that the company will release new firmware updates on that same day for one or more of its Surface tablets.
Source: Microsoft | Image via Lenovo
/Steve
-
I will report it to Malwarebytes as phishing, I'm not sure if the researchers browse this section.
Edit: the site is dead now

Thanks @Malware1 ... I never even thought to post the site in the Malware section. My bad..
 Appreciate you taking care of it for me.
Appreciate you taking care of it for me.Steve
-
I sent the letter with headers to Discover Card's fraud email - Contact info for fraud there can be reported to any of the following.
If you receive what appears to be a fraudulent e-mail from us, please call 1-800-DISCOVER (1-800-347-2683) or e-mail us at emailwatch@discover.com immediately.
Thank goodness I've drilled it into my wife's head to NEVER do anything with any email concerning money, credit cards, SSNs, etc except to let me know so I can check them out.

Steve
-
BEGIN ORIGINAL LONG EMAIL HEADER
Return-Path: <ringvald@brandeis.edu>
Received: from mail-qc0-f196.google.com (mail-qc0-f196.google.com [209.85.216.196])
(using TLSv1 with cipher RC4-SHA (128/128 bits))
(No client certificate requested)
by mtain-mp10.r1000.mx.aol.com (Internet Inbound) with ESMTPS id E3B56380000B2
for <saxxxxx@aol.com> Fri, 7 Feb 2014 08:52:00 -0500 (EST)
Received: by mail-qc0-f196.google.com with SMTP id c9so1703499qcz.3
for <saxxxxx@aol.com> Fri, 07 Feb 2014 05:52:00 -0800 (PST)
X-Google-DKIM-Signature: v=1; a=rsa-sha256; c=relaxed/relaxed;
d=1e100.net; s=20130820;
h=x-gm-message-state:message-id:content-type:mime-version:subject:to
:from:date;
bh=0izqEhXiX8d/7Dy/VSP5VLzajSYc9p0Hu52gEyZo56M=;
b=AaC1uoHqEBdzmGSIq9NEOzYf6nz8d8oo6MlhGlVp99uPhDjwACA/xumpCXtaW+vJbZ
Z756ApILU81RqsEbR2ErSBHcpQEifRN35Bm6/wCENnwdhq67FeGP9kffMWtR4XeBSBaB
JaqNfRSGTrodVZheiPkb2SxBhD4F+uDqFKrbHlgEjgrRCw2XZaaTGx7wtMsDtKBnK2Kx
wU8iNfOgPUICtR8A2x6cRvO3lyqamKw1s/t2jdFMKe4PyqBX3U7u8SgZsVRBusa54wyU
NI2DTyFWsGIhpz1EvupNhSMG++mB+AWPMzSHR0VuW3XWoJXsv80wODY0Thm7NZr0Ujr4
ZUGA==
X-Gm-Message-State: ALoCoQniRh1bQKi9bUUP9EsB1Bz4qdFP+J0NW0PgBpLdwY+NagMGZL3VQOPEa394ivsI9WIBrUw1
X-Received: by 10.224.88.131 with SMTP id a3mr22464325qam.34.1391781120674;
Fri, 07 Feb 2014 05:52:00 -0800 (PST)
Received: from term.KarrShermanCo.local (smtpout.karrsherman.com. [66.193.29.122])
by mx.google.com with ESMTPSA id d7sm13496851qad.10.2014.02.07.05.51.58
for <multiple recipients>
(version=TLSv1 cipher=RC4-SHA bits=128/128);
Fri, 07 Feb 2014 05:52:00 -0800 (PST)
Message-ID: <52f4e500.8707e00a.11c0.ffffe1b8@mx.google.com>
Content-Type: multipart/alternative; boundary="===============0757205506=="
MIME-Version: 1.0
Subject: =?utf-8?q?Online_Update=3A_Regarding_Your_Discover_Card=C2=AE?=
To: Recipients <safe@discover.com>
From: Discover Card <ringvald@brandeis.edu>
Date: Fri, 07 Feb 2014 08:51:52 -0500
x-aol-global-disposition: G
Authentication-Results: mx.aol.com;
spf=pass (aol.com: the domain brandeis.edu reports 209.85.216.196 as a permitted sender.) smtp.mailfrom=brandeis.edu;
x-aol-sid: 3039ac1dc14e52f4e5001adb
X-AOL-IP: 209.85.216.196
X-AOL-SPF: domain : brandeis.edu SPF : pass
END ORIGINAL LONG HEADER
BEGIN PHISHINGFrom: ringvald@brandeis.edu
To: safe@discover.com
Sent: 2/7/2014 8:52:01 A.M. Eastern Standard Time
Subj: Online Update: Regarding Your Discover Card®
Dear Cardmember
The security of your personal information is our primary concern.
Recently we observe suspicious login attempt to your Discover Card® account
All information associated with this account has been temporarily limited
We implore you to confirm your account by following our secure site [https://www.discovercard.com] (actual URL= http://dicasdosmelhores.com/iso.php) to avoid account suspended << (should have said "suspension")Sincerely,
Discover Card® Customer Service
-----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------
IMPORTANT INFORMATION
This e-mail was sent to you from Discover.
You are receiving this Discover e-mail as a confirmation of your account activity.
Please do not reply to this e-mail as we are not able to respond to messages sent to this address.
END PHISHING LETTER
Thanks for looking in to this..
Antxxxx xxxxxxxxxxder
xxxxxxxx@tampabay.rr.comNOTE: Had to use quote to preserve malformed URLS as editor wouldn't accept them..
-
.
Target Hackers Broke in Via HVAC Company
By Brian Krebs
5 February 2014
Last week, Target told reporters at The Wall Street Journal and Reuters that the initial intrusion into its systems was traced back to network credentials that were stolen from a third party vendor. Sources now tell KrebsOnSecurity that the vendor in question was a refrigeration, heating and air conditioning subcontractor that has worked at a number of locations at Target and other top retailers.
Sources close to the investigation said the attackers first broke into the retailer’s network on Nov. 15, 2013 using network credentials stolen from Fazio Mechanical Services, a Sharpsburg, Penn.-based provider of refrigeration and HVAC systems.
Fazio president Ross Fazio confirmed that the U.S. Secret Service visited his company’s offices in connection with the Target investigation, but said he was not present when the visit occurred. Fazio Vice President Daniel Mitsch declined to answer questions about the visit. According to the company’s homepage, Fazio Mechanical also has done refrigeration and HVAC projects for specific Trader Joe’s, Whole Foods and BJ’s Wholesale Club locations in Pennsylvania, Maryland, Ohio, Virginia and West Virginia.
Target spokeswoman Molly Snyder said the company had no additional information to share, citing a “very active and ongoing investigation.”
It’s not immediately clear why Target would have given an HVAC company external network access, or why that access would not be cordoned off from Target’s payment system network. But according to a cybersecurity expert at a large retailer who asked not to be named because he did not have permission to speak on the record, it is common for large retail operations to have a team that routinely monitors energy consumption and temperatures in stores to save on costs (particularly at night) and to alert store managers if temperatures in the stores fluctuate outside of an acceptable range that could prevent customers from shopping at the store.
“To support this solution, vendors need to be able to remote into the system in order to do maintenance (updates, patches, etc.) or to troubleshoot glitches and connectivity issues with the software,” the source said. “This feeds into the topic of cost savings, with so many solutions in a given organization. And to save on head count, it is sometimes beneficial to allow a vendor to support versus train or hire extra people.”CASING THE JOINT
Investigators also shared additional details about the timeline of the breach and how the attackers moved stolen data off of Target’s network.
Sources said that between Nov. 15 and Nov. 28 (Thanksgiving and the day before Black Friday), the attackers succeeded in uploading their card-stealing malicious software to a small number of cash registers within Target stores.
Those same sources said the attackers used this time to test that their point-of-sale malware was working as designed.
By the end of the month — just two days later — the intruders had pushed their malware to a majority of Target’s point-of-sale devices, and were actively collecting card records from live customer transactions, investigators told this reporter. Target has said that the breach exposed approximately 40 million debit and credit card accounts between Nov. 27 and Dec. 15, 2013.
DATA DROPS
While some reports on the Target breach said the stolen card data was offloaded via FTP communications to a location in Russia, sources close to the case say much of the purloined financial information was transmitted to several “drop” locations.
These were essentially compromised computers in the United States and elsewhere that were used to house the stolen data and that could be safely accessed by the suspected perpetrators in Eastern Europe and Russia.
For example, card data stolen from Target’s network was stashed on hacked computer servers belonging to a business in Miami, while another drop server resided in Brazil. (More...)
Read the rest at: https://krebsonsecurity.com/2014/02/target-hackers-broke-in-via-hvac-company/
/Steve
-
.
Windows 8.1 Update 1 now looking like April
Summary: Microsoft's new ship target for its coming Windows 8.1 Update 1 may have shifted from March to April, according to sources.
I've heard from two of my sources in the past week that Microsoft's ship target for Windows 8.1 Update 1 has shifted from March 2014 to April 2014.

The idea remains to use Patch Tuesday to distribute the coming so-called "Spring" update via Windows Update, my sources said. If that is the case, Windows 8.1 Update 1 should be pushed to users on April 8, rather than March 11.
Windows 8.1 Update 1 is a collection of features and fixes for Windows 8.1. Most of the new features are aimed at making Windows 8.1 more palatable to those who prefer using a mouse to navigate the latest Windows release.
A leaked Windows 8.1 Update 1 test build (from mid-January) showed off a number of the expected new features, including the ability to pin Metro apps to the Desktop task bar; new right-clickable context-sensitive menus; and adding dedicated search and power buttons to the Start screen. A new Enterprise Mode for Internet Explorer 11 is also part of the leaked build, according to some who've downloaded it.
There were reports that Windows 8.1 Update 1 might change the default start-up experience so that the desktop, rather than the Metro Start screen became the default on all machines running Update 1. As I noted last week, I heard this is not Microsoft's plan. Those downloading the leaked Windows 8.1 Update 1 build from January noted that boot-to-desktop was not set as the default configuration.
Windows leaker WZor indicated on February 2 that a more likely scenario may be that boot to desktop will be installed by default on new PCs/devices without a touch screen. Users who are upgrading from Windows 8.1 to Windows 8.1 Update 1 who don't have boot to desktop set as their default already also won't see their settings change to boot to default, according to WZor.
I am not sure why the ship target for Update 1 has allegedly been pushed back a month, but have heard that the original March target was fairly ambitious. OEMs are still likely to get the Windows 8.1 Update 1 bits in early March for preloading on new PCs, my sources said.
SOURCE: http://www.zdnet.com/windows-8-1-update-1-now-looking-like-april-7000026009/
Steve
-
.
Adobe Pushes Fix for Flash Zero-Day Attack
Adobe Systems Inc. is urging users of its Flash Player software to upgrade to a newer version released today. The company warns that an exploit targeting a previously unknown and critical Flash security vulnerability exists in the wild, and that this flaw allows attackers to take complete control over affected systems.
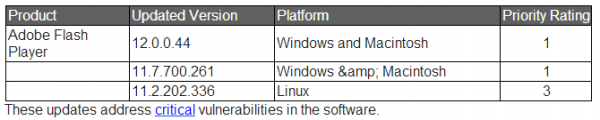
The latest versions that include the fix for this flaw (CVE-2014-0497) are listed by operating system in the chart below.
The Flash update brings the media player to version 12.0.0.44 for a majority of users on Windows and Mac OS X.
This link will tell you which version of Flash your browser has installed. IE10/IE11 and Chrome should auto-update their versions of Flash to v. 12.0.0.44. If your version of Flash on Chrome (on either Windows, Mac or Linux) is not yet updated, you may just need to close and restart the browser. The version of Chrome that includes this fix is 32.0.1700.107 for Windows, Mac, and Linux (to learn what version of Chrome you have, click the stacked bars to the right at of the address bar, and select “About Google Chrome” from the drop down menu). (More...)
Continued at: http://krebsonsecurity.com/2014/02/adobe-pushes-fix-for-flash-zero-day-attack/
Steve
-
.
File Your Taxes Before the Fraudsters Do
Brian Krebs
Jan. 31 marked the start of the 2014 tax filing season, and if you haven’t yet started working on your returns, here’s another reason to get motivated: Tax fraudsters and identity thieves may very well beat you to it.
According to a 2013 report from the Treasury Inspector General’s office, the U.S. Internal Revenue Service (IRS) issued nearly $4 billion in bogus tax refunds in 2012. The money largely was sent to people who stole Social Security numbers and other information on U.S. citizens, and then filed fraudulent tax returns on those individuals claiming a large refund but at a different address.
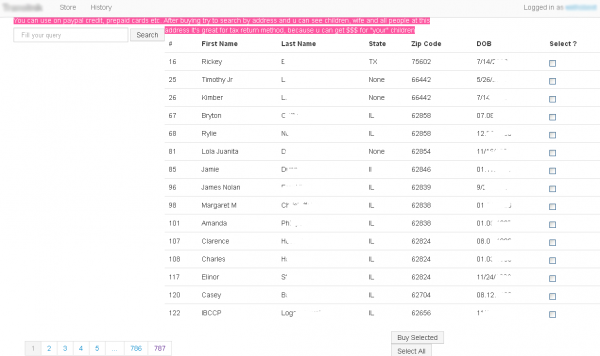
There are countless shops in the cybercrime underground selling data that is especially useful for scammers engaged in tax return fraud. Typically, these shops will identify their wares as “fullz,” which include a consumer’s first name, last name, middle name, email address (and in some cases email password) physical address, phone number, date of birth, and Social Security number.
Click on Image to Enlarge
This underground shop caters sells consumer identity data, catering to tax return fraud.
The shop pictured above, for example, caters to tax fraudsters, as evidenced by its advice to customers of the service, which can be used to find information that might help scammers establish lines of credit (PayPal accounts, credit cards) in someone else’s name:
“You can use on paypal credit, prepaid cards etc. After buying try to search by address and u can see children, wife and all people at this address,” the fraud shop explains, advising customers on ways to find the names and additional information on the taxpayer’s children (because more dependents mean greater tax deductions and higher refunds): “It’s great for tax return method, because u can get $$$ for ‘your’ children.”Continue reading → - https://krebsonsecurity.com/2014/02/file-your-taxes-before-the-fraudsters-do/#more-24439
/Steve
-
.
A'hah.. Now I know why it is set OFF as the recommended setting.. And it was my pleasure to post my successful results due to a positive suggestion (clarification) by @Samuel where I didn't have to run logs, etc.. As always, many thanks to all.
Steve
-
Wow... I can't believe as big as Target is that they don't have at least one or more network administrators that would have balked at installing an account like that.
Probably have a couple looking for new jobs right now.. How'd you like to be one of those guys asking for a letter of recommendation? *evil-grin*
-
.
Used RevoPro-Uninstaller with program left-over scraps scan/delete and removed both MBAMPro 1.75 and EAM.
Re-booted system..
Installed MBAM-Consumer 2.0 with TEST license..
Set up all the various scan parameters and update schedule..
Ran MBAM 2 scan; OK..
Ran Firefox 27.0rc1 with no problems.. System did not slow down or "hourglass" at any time..
Will leave EAM uninstalled until I'm certain nothing else is causing any type of problem with MBAM2..
I love the GUI and the way it's set up. I have one question on the settings; Why does "self-protection" have to be manually checked ON
-
Try uninstalling EAM, reinstalling MBAM 2.0 beta and starting protection, then reinstall EAM. For some reason if you don't do it in that order EAM will prevent MBAM's driver from loading which can cause this issue.
Samuel,
Thanks for the info; I'll try it a little bit later and post the results - around suppertime EST.
@DD - Thanks for taking the time to answer via phone - rest in PM
Steve
-
.
Target hackers may have exploited backdoor in widely used server software
KrebsonSecurity digs in to point-of-sale malware infecting retailer's network.
by Dan Goodin - Jan 29 2014, 4:19pm EST

Widely used management software running on Target's internal network may have given an important leg-up to attackers who compromised 40 million payment cards belonging to people who recently shopped at the retail giant, according to an article published Wednesday by KrebsonSecurity.
As journalist Brian Krebs reported two weeks ago, malware that infected Target's point-of-sale terminals used the account name "Best1_user" and the password "BackupU$r" to log in to a control server inside the Target network. The malware used the privileged insider access to temporarily stash payment card data siphoned out of the terminals used in checkout lines so it could then periodically be downloaded to a different service for permanent storage. In Wednesday's post, Krebs filled in some intriguing new details that suggest a poorly secured feature inside a widely used server management program may have played a role. Krebs explained:
That “Best1_user” account name seems an odd one for the attackers to have picked at random, but there is a better explanation: That username is the same one that gets installed with an IT management software suite called Performance Assurance for Microsoft Servers. This product, according to its maker — Houston, Texas based BMC Software — includes administrator-level user account called “Best1_user.”
This knowledge base article (PDF) published by BMC explains the Best1_user account is used by the software to do routine tasks. That article states that while the Best1_user account is essentially a “system” or “administrator” level account on the host machine, customers shouldn’t concern themselves with this account because “it is not a member of any group (not even the ‘users’ group) and therefore can’t be used to login to the system.”“The only privilege that the account is granted is the ability to run as a batch job,” the document states, indicating that it could be used to run programs if invoked from a command prompt.
Krebs went on to quote a part of the BMC article that said:
Perform Technical Support does not have the password to this account and this password has not been released by Perform Development. Knowing the password to the account should not be important as you cannot log into the machine using this account. The password is known internally and used internally by the Perform agent to assume the identity of the “Best1_user” account.Krebs asked BMC if "BackupU$r" is the password that controls access to the "Best1_user" account. Company representatives have yet to provide an answer.
Krebs also cited a report that Dell SecureWorks privately distributed to clients earlier this week. "The Best1_user account appears to be associated with the Performance Assurance component of BMC's Software's Patrol product," Dell SecureWorks researchers wrote. "According to BMC's documentation, this account is normally restricted, but the attackers may have usurped control to facilitate lateral movement within the network."
Krebs also repeated what Ars noted two weeks ago—that there's a compelling case to be made that, just like the co-conspirators of now-convicted Albert Gonzalez, the people who hacked Target may have first penetrated the network by mounting a SQL injection attack on Target's website. Wednesday's report from Krebs has many more details, including a recent dump of more than 2 million compromised payment cards, all of them used at Target between November 27 and December 15.
SOURCE: http://arstechnica.com/security/2014/01/target-hackers-may-have-exploited-backdoor-in-widely-used-server-software/
/Steve -
.
Removed MBAMPro 1.75.0.1300 and installed public beta MBAM 2.00.0.0502
Set up MBAM2 with schedule, protection on, updated and ran scan.. All OK
Tried to use other programs on computer and everything slowed to 0% Couldn't get Firefox 27 to any sites; hourglass showing for any program or action I tried.
Removed MBAM2 and reinstalled MbamPro - Everything worked perfectly.
Running Win8.1, KIS2014, EAM
Just an FYI as I don't have the will or time to run logs/developer mode. Don't mean to be uncooperative, etc, but I feel I do enough in the Software Forums to justify my being. (no bad mojo, karma or sarcasm intended - just don't have time - sorry
 :( )
:( )Steve


Major Failure
in Malwarebytes Anti-Malware 2.00 Beta Test
Posted
Curious as to why all of a sudden?? The only change since I installed it 2 days ago has been Database Updates .. no components were changed. (I don't think..)
Thanks for looking into it.
Steve