-
Posts
12,084 -
Joined
-
Days Won
42
Content Type
Events
Profiles
Forums
Posts posted by 1PW
-
-
The Tor Browser 13.0.1 (All Platforms) has been released. (25-October-2023)
Tor Browser 13.0.1 is now available from the Tor Browser download page and also from our distribution directory.Blog/Announcement | Full Changelog |
Full changelog
The full changelog since Tor Browser 13.0 is:
-
All Platforms
- Bug tor-browser#42185: Rebase stable browsers on top of 115.4.0esr
- Bug tor-browser#42191: Backport security fixes (Android & wontfix) from Firefox 119 to 115.4 - based Tor Browser
- Bug tor-browser-build#40975: libstdc++.so.6 is included twice in tor-browser
-
Windows + macOS + Linux
- Updated Firefox to 115.4.0esr
- Bug tor-browser#42182: Default Search Engine Does Not Persist Through Shift to New Identity
-
Android
- Updated GeckoView to 115.4.0esr
-
Build System
-
All Platforms
- Updated Go to 1.21.3
- Bug tor-browser-build#40976: Update download-unsigned-sha256sums-gpg-signatures-from-people-tpo to fetch from tb-build-02 and tb-build-03
- Bug rbm#40062: Copy input directories to containers recursively
-
Windows + Linux
- Bug tor-browser-build#40991: Fix creation of downloads-windows-x86_64.json and downloads-linux-x86_64.json
-
Windows
- Bug tor-browser-build#40984: The PDBs for .exe are not included
-
Linux
- Bug tor-browser-build#40979: Add redirects from old Linux bundle filename to the new one
-
All Platforms
-
 1
1
-
All Platforms
-
Hello @Aryna:
QuoteWe fixed several previously reported crashes. Please do let us know if any of the issue persists.
For my MBP18,1, the issue persists.
Please let me know if I can assist further.
Thank you.
-
Hello @drdas:
In this instance, you and I are running the same software. Of course, Apple's restrictions would not permit a similar Malwarebytes Browser Guard (MBG) that compares closely to those for Firefox/Chrome-based browsers.
Be that as it may, the behaviors you described parallel what I see on my laptop. Devs/staffers may have some additional insight.
HTH
-
Hello @Aryna and
 :
:
Would you please confirm whether users are required to uninstall Malwarebytes-Mac-4.6.13.3835.pkg or Malwarebytes-Mac-5.0.72.422.pkg before installing Malwarebytes-Mac-5.0.102.681.pkg?
I might recall that an uninstall of MB4 for Mac was compulsory.
My MBP18,1 experienced MB5_mac_preview crashes (reported in this sub-forum) under macOS Ventura and Sonoma. Have these crashes been resolved?
Thank you.
-
As previously announced in the post before this one, OpenSSL has released the promised updated versions 3.1.4 and 3.0.12 on 24-October-2023.
Newslog | Downloads | Changelog |
-----BEGIN PGP SIGNED MESSAGE----- Hash: SHA256 OpenSSL Security Advisory [24th October 2023] ============================================= Incorrect cipher key & IV length processing (CVE-2023-5363) =========================================================== Severity: Moderate Issue summary: A bug has been identified in the processing of key and initialisation vector (IV) lengths. This can lead to potential truncation or overruns during the initialisation of some symmetric ciphers. Impact summary: A truncation in the IV can result in non-uniqueness, which could result in loss of confidentiality for some cipher modes. When calling EVP_EncryptInit_ex2(), EVP_DecryptInit_ex2() or EVP_CipherInit_ex2() the provided OSSL_PARAM array is processed after the key and IV have been established. Any alterations to the key length, via the "keylen" parameter or the IV length, via the "ivlen" parameter, within the OSSL_PARAM array will not take effect as intended, potentially causing truncation or overreading of these values. The following ciphers and cipher modes are impacted: RC2, RC4, RC5, CCM, GCM and OCB. For the CCM, GCM and OCB cipher modes, truncation of the IV can result in loss of confidentiality. For example, when following NIST's SP 800-38D section 8.2.1 guidance for constructing a deterministic IV for AES in GCM mode, truncation of the counter portion could lead to IV reuse. Both truncations and overruns of the key and overruns of the IV will produce incorrect results and could, in some cases, trigger a memory exception. However, these issues are not currently assessed as security critical. Changing the key and/or IV lengths is not considered to be a common operation and the vulnerable API was recently introduced. Furthermore, it is likely that application developers will have spotted this problem during testing since decryption would fail unless both peers in the communication were similarly vulnerable. For these reasons, we expect the probability of an application being vulnerable to this to be quite low. However, if an application is vulnerable then this issue is considered very serious. For these reasons, we have assessed this issue as Moderate severity overall. The OpenSSL SSL/TLS implementation is not affected by this issue. The OpenSSL 3.0 and 3.1 FIPS providers are not affected by this because the issue lies outside of the FIPS provider boundary. OpenSSL 3.1 and 3.0 are vulnerable to this issue. OpenSSL 3.0 users should upgrade to OpenSSL 3.0.12. OpenSSL 3.1 users should upgrade to OpenSSL 3.1.4. This issue was reported on 21st September 2023 by Tony Battersby of Cybernetics. The fix was developed by Dr. Paul Dale. This problem was independently reported on the 3rd of December 2022 as part of issue #19822, but it was not recognised as a security vulnerability at that time. General Advisory Notes ====================== URL for this Security Advisory: https://www.openssl.org/news/secadv/20231024.txt Note: the online version of the advisory may be updated with additional details over time. For details of OpenSSL severity classifications, please see: https://www.openssl.org/policies/general/security-policy.html OpenSSL 1.1.1 is out of support and no longer receiving public updates. Extended support is available for premium support customers: https://www.openssl.org/support/contracts.html -----BEGIN PGP SIGNATURE----- iQIzBAEBCAAdFiEE78CkZ9YTy4PH7W0w2JTizos9efUFAmU33bsACgkQ2JTizos9 efVwAg/8Dh8qiBA3LEzTP39JtwAZzf0MPUEe0I5bvS7GUXIX8EemYojcNyoa/i+x Lr/DQtRJ0j/woiy2PhMFbej+NNMwtHD4Cu83JB+wEEiXbnt4n5yi+rWb9hw19Fs6 g17EDbsi1j5fgCQ81Psgxg02bgC/3iE2AnDYty6mRQnfMPe599SMUEnUsRfeGdTh QGOwLbAH58a3OydMFD5tUHY6JKKwU7WhLrYanAT7YIlU4oQbAIEKL7+K0roIzhyq 3o7EjtfKAr2ttcl+iOXdJYRb+0OwP59y/BBAOOOdCcb2oqDs1fPvXB8BXHhR43Ew i5EF47fUFxICu2kuXEe00RbbJipAqF5S0KvIKurYPjepukWjOqnNBQc4euned0gN bYcQgMLjYoZAp79V42kRMTQ+uMP1ElUCx4gwY8iOn6R65TmHloiNWv/q0I3XhWeH piLOv9lm/pMNmArpFGpySQzTY/wyyEvc9ZQcThSdWSiJOIebG4wFLYP+LvzG81/Q KX0yMK1dB8nyD6n+p14aIxhaWHr/7YgNO0882YbG11OQftIB5HXIXsQT5XFdVm8h OUCJfj1iPv1O3Xr7UkTISzGzRZyYLoUxFSi9+DrMHWaK9pQqSYDjqB6XE8vImnZN wJJj9hGRRZzCON5pXuh5+bIPSozdUPaZtWWm9ICobB/PLyvD05M= =aGd3 -----END PGP SIGNATURE-----
-
 1
1
-
-
Version 119.0, first offered to Release channel users on October 24, 2023
New
-
Firefox View includes more content. You can now see all open tabs, from all windows. If you sync open tabs, you’ll see all tabs from other devices. Browsing history is now listed and you can sort by date or by site. As before, recently closed tabs are also listed on Firefox View.
To access Firefox View, select the file folder icon at the top left of your tab strip.
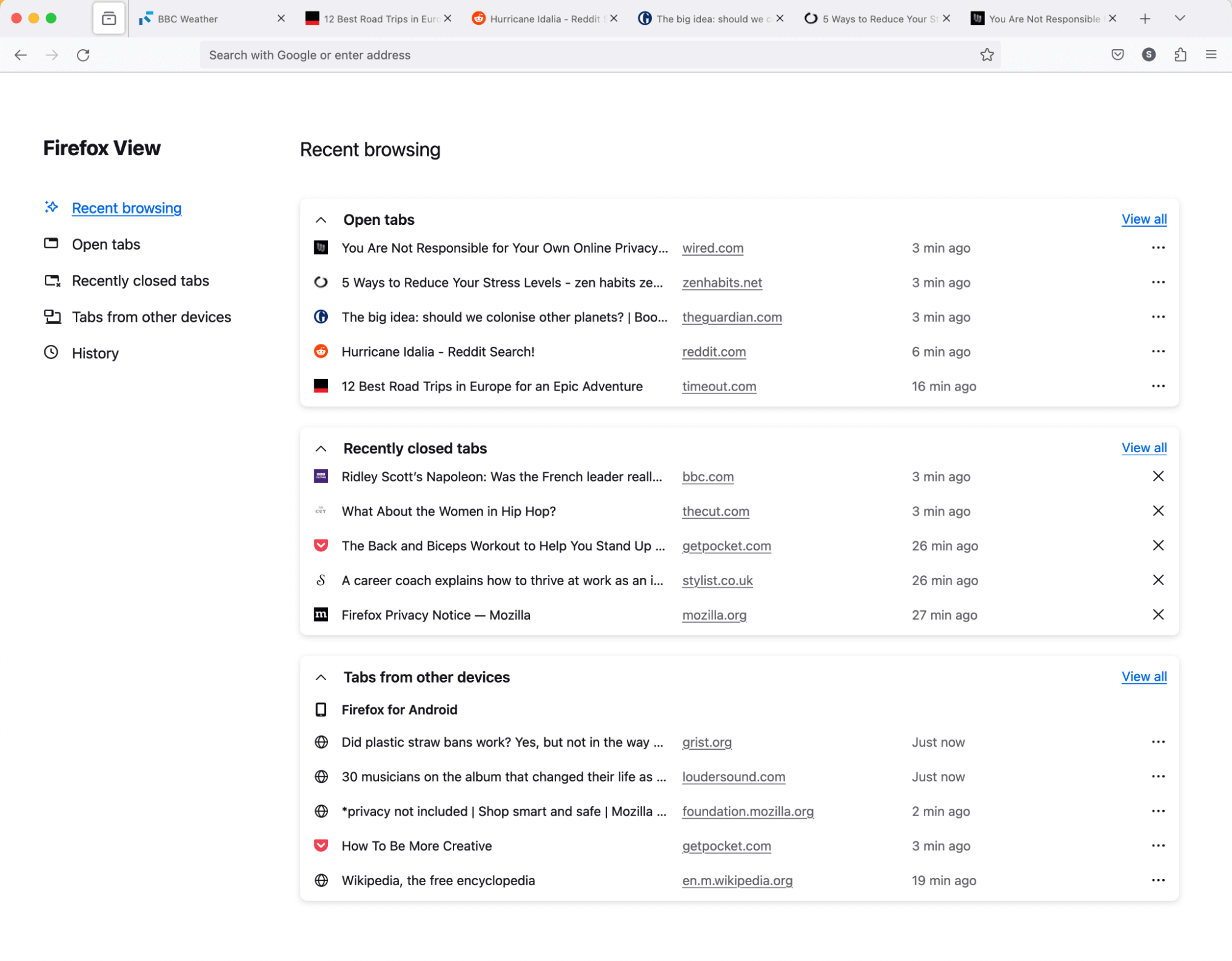
-
Gradually rolling out in Fx119, Firefox now allows you to edit PDFs by adding images and alt text, in addition to text and drawings.
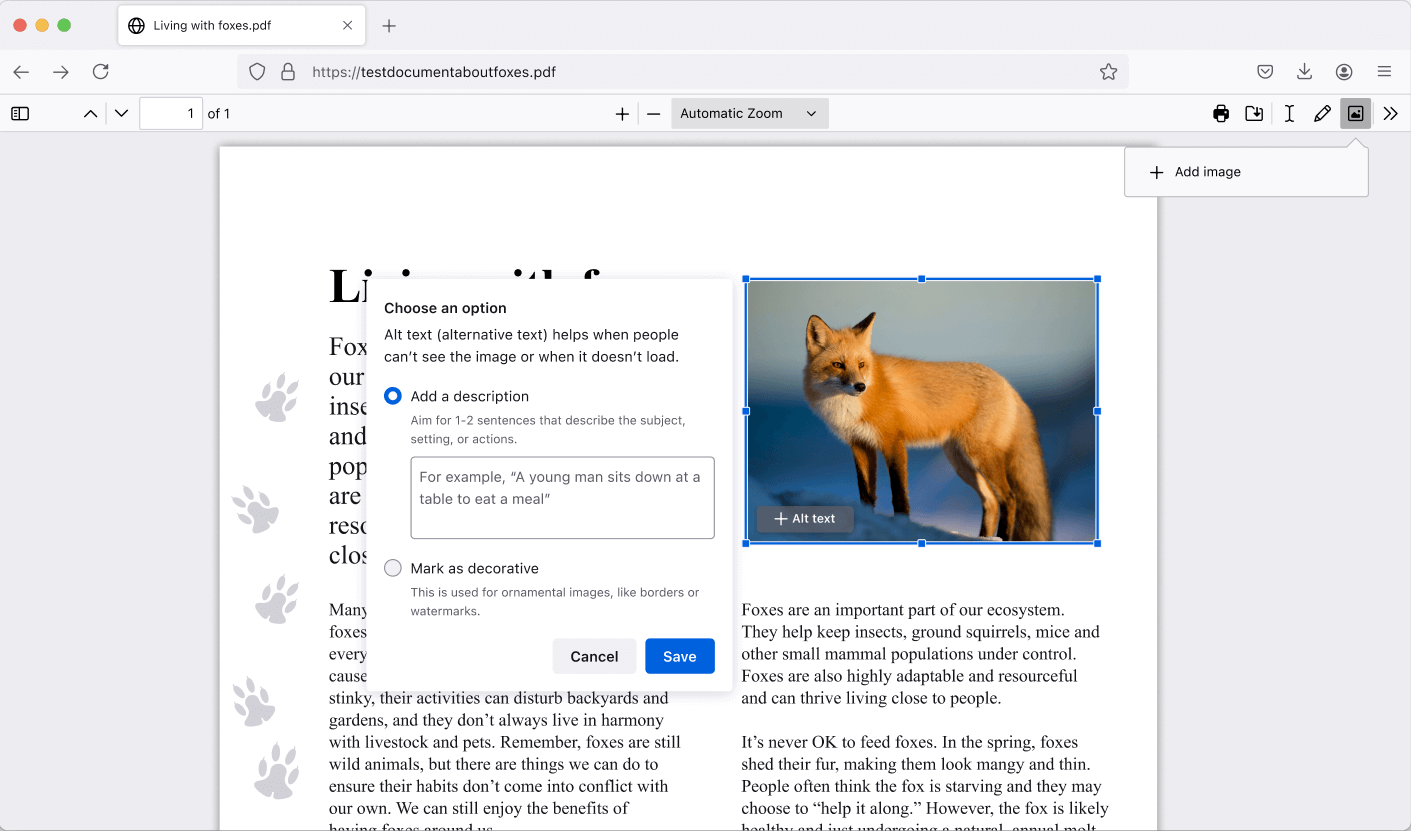
-
Recently closed tabs now persist between sessions that don't have automatic session restore enabled. Manually restoring a previous session will continue to reopen any previously open tabs or windows.
-
If you're migrating your data from Chrome, Firefox now offers the ability to import some of your extensions as well.
-
As part of Total Cookie Protection, Firefox now supports the partitioning of Blob URLs, this mitigates a potential tracking vector that third-party agents could use to track an individual.
-
The visibility of fonts to websites has been restricted to system fonts and language pack fonts in Enhanced Tracking Protection strict mode to mitigate font fingerprinting.
-
The Storage Access API web standard was updated to improve security while mitigating website breakages and further enabling the phase out of third-party cookies in Firefox.
-
Encrypted Client Hello (ECH) is now available to Firefox users, delivering a more private browsing experience. ECH extends the encryption used in TLS connections to cover more of the handshake and better protect sensitive fields. Read more about the launch of ECH on Mozilla Distilled.
-
Media sniffing is no longer applied to files served as type
application/octet-stream, this allows these files to be downloaded instead of attempting playback. -
On Windows, the mouse pointer will disappear while typing if the relevant Windows mouse properties system setting is enabled.
-
Firefox is now available in the Santali (sat) language.
Fixed
-
Fixed an issue causing unexpected jumps in scroll position on Facebook.
-
Various security fixes.
Mozilla Foundation Security Advisory 2023-45
Security Vulnerabilities fixed in Firefox 119
11 Total: 3 High, 7 Moderate, 1 Low
- Announced
- October 24, 2023
- Impact
- high
- Products
- Firefox
- Fixed in
-
- Firefox 119
#CVE-2023-5721: Queued up rendering could have allowed websites to clickjack
- Reporter
- Kelsey Gilbert
- Impact
- high
Description
It was possible for certain browser prompts and dialogs to be activated or dismissed unintentionally by the user due to an insufficient activation-delay.
References
#CVE-2023-5722: Cross-Origin size and header leakage
- Reporter
- annevk
- Impact
- moderate
Description
Using iterative requests an attacker was able to learn the size of an opaque response, as well as the contents of a server-supplied Vary header.
References
#CVE-2023-5723: Invalid cookie characters could have led to unexpected errors
- Reporter
- Daniel Veditz
- Impact
- moderate
Description
An attacker with temporary script access to a site could have set a cookie containing invalid characters using
document.cookiethat could have led to unknown errors.References
#CVE-2023-5724: Large WebGL draw could have led to a crash
- Reporter
- pwn2car
- Impact
- moderate
Description
Drivers are not always robust to extremely large draw calls and in some cases this scenario could have led to a crash.
References
#CVE-2023-5725: WebExtensions could open arbitrary URLs
- Reporter
- Shaheen Fazim
- Impact
- moderate
Description
A malicious installed WebExtension could open arbitrary URLs, which under the right circumstance could be leveraged to collect sensitive user data.
References
#CVE-2023-5726: Full screen notification obscured by file open dialog on macOS
- Reporter
- Edgar Chen and Hafiizh
- Impact
- moderate
Description
A website could have obscured the full screen notification by using the file open dialog. This could have led to user confusion and possible spoofing attacks.
Note: This issue only affected macOS operating systems. Other operating systems are unaffected.References
#CVE-2023-5727: Download Protections were bypassed by .msix, .msixbundle, .appx, and .appxbundle files on Windows
- Reporter
- Marco Bonardo
- Impact
- moderate
Description
The executable file warning was not presented when downloading .msix, .msixbundle, .appx, and .appxbundle files, which can run commands on a user's computer.
Note: This issue only affected Windows operating systems. Other operating systems are unaffected.References
#CVE-2023-5728: Improper object tracking during GC in the JavaScript engine could have led to a crash.
- Reporter
- anbu
- Impact
- moderate
Description
During garbage collection extra operations were performed on a object that should not be. This could have led to a potentially exploitable crash.
References
#CVE-2023-5729: Fullscreen notification dialog could have been obscured by WebAuthn prompts
- Reporter
- Shaheen Fazim
- Impact
- low
Description
A malicious web site can enter fullscreen mode while simultaneously triggering a WebAuthn prompt. This could have obscured the fullscreen notification and could have been leveraged in a spoofing attack.
References
#CVE-2023-5730: Memory safety bugs fixed in Firefox 119, Firefox ESR 115.4, and Thunderbird 115.4
- Reporter
- Jed Davis, Andrew McCreight, Randell Jesup, and the Mozilla Fuzzing Team
- Impact
- high
Description
Memory safety bugs present in Firefox 118, Firefox ESR 115.3, and Thunderbird 115.3. Some of these bugs showed evidence of memory corruption and we presume that with enough effort some of these could have been exploited to run arbitrary code.
References
#CVE-2023-5731: Memory safety bugs fixed in Firefox 119
- Reporter
- Steve Fink, Stefan Arentz, and the Mozilla Fuzzing Team
- Impact
- high
Description
Memory safety bugs present in Firefox 118. Some of these bugs showed evidence of memory corruption and we presume that with enough effort some of these could have been exploited to run arbitrary code.
References
-
 1
1
-
-
-
Malwarebytes Windows Firewall Control (WFC) 6.9.7.0 has been released. (20-October-2023)
Homepage | Download | Change History | FAQ | User Guide | Support | Forum
QuoteWindows Firewall Control v.6.9.7.0
Change log:
- Fixed: Cannot delete invalid rules located under C:\$WINDOWS.~BT folder.
- Fixed: Adding multiple rules at once to the same group fails if the rules have no description set.
- Fixed: Cannot create a duplicate of a temporary rule.
- Fixed: Notifications are disabled after WFC restart and must be re-enabled again.
- Fixed: When unchecking the 'Blocked connections' in Connections Log, the notifications still appear as enabled when they are, in fact, disabled.
- Added back translations for Chinese, Dutch, Polish, since they were updated to the current version.
Download location: https://binisoft.org/download/wfc6setup.exe
SHA1: 00d42ce20765f920b575de3b090a871ec1178020
SHA256: 4705777f045450023b739e9e87c73c9d53f158faf788fe720a23df8cf2d89280
Thank you for your feedback and your support,
Alexandru Dicu
It appears that the major changes that were made in version 6.9.3.0 created some new bugs and also helped to discover older bugs. The first 3 fixed bugs from the changelog existed for many years ago.-
 1
1
-
-
This document is a one-stop resource to help organizations reduce the risk of ransomware incidents through best practices to detect, prevent, respond, and recover, including step-by-step approaches to address potential attacks. This publication was developed through the Joint Ransomware Task Force (JRTF), an interagency body established by Congress in the Cyber Incident Reporting for Critical Infrastructure Act of 2022 (CIRCIA) to ensure unity of effort in combating the growing threat of ransomware attacks. More...
-
 1
1
-
-
Microsoft's Sysinternals Suite 2023.10.18 was released on 18-October-2023.
-
 1
1
-
-
Quote
New OpenSSL Releases
Matt Caswell matt at openssl.org
Tue Oct 17 17:48:26 UTC 2023- Messages sorted by: [ date ] [ thread ] [ subject ] [ author ]
The OpenSSL project team would like to announce the upcoming release of OpenSSL versions 3.1.4 and 3.0.12. These releases will be made available on Tuesday 24th October 2023 between 1300-1700 UTC. These are security-fix releases. The highest severity issue fixed in each of these two releases is Moderate: https://www.openssl.org/policies/secpolicy.html Yours The OpenSSL Project Team
-
 1
1
-
Note: It was later discovered that version 6.9.6.0 was also released on this same day but missed in this topic.
Malwarebytes Windows Firewall Control (WFC) 6.9.5.0 has been released. (18-October-2023)
Homepage | Download | Change History | FAQ | User Guide | Support | Forum
QuoteWindows Firewall Control v.6.9.5.0
Change log:
- Fixed: Global hotkeys can't be set properly without restarting the software.
- Improved: Uninstall dialog will now resize the content so that it displays the entire content in all languages.
- Removed: Unmaintained language files were removed from the software.
Download location: https://binisoft.org/download/wfc6setup.exe
SHA1: da1a2207468f22704752956ab5871948e75b4c8a
SHA256: 9d49fcb5f3e7bc05db4da11ebfc793d71699762a1015ddcd7db19141dba9d5d4-
 1
1
-
-
Malwarebytes Windows Firewall Control (WFC) 6.9.4.0 has been released. (17-October-2023)
Homepage | Download | Change History | FAQ | User Guide | Support | Forum
Windows Firewall Control v.6.9.4.0
Change log:
- New: Added compatibility with Smart App Control from Windows 11. The process wfc.exe was renamed to wfcUI.exe.
- Improved: Replaced WCF with GRPC for inter process communication. WFC requires now NET Framework 4.6.2 or a newer version.
- Improved: Global hotkey which can toggle between Low and Medium profiles can now toggle between all profiles.
- Improved: User settings are now applied per user account. Only the settings from Security tab are still global per machine.
- Fixed: Main Panel opens multiple times if you press fast on the tray icon.
- Fixed: Secure Boot is not enabling High Filtering profile if wfc.exe is not running.
- Fixed: Installer does not work if there is a WCF related problem with .NET Framework installation.
- Fixed: After a failed policy import, notifications are not displayed anymore and a program restart is required to re-enable them.
- Fixed: Notification dialog becomes unresponsive if a program generates a lot of blocked connections.
- Fixed: WFC service fails to start if EventLog service is unavailable.
- Fixed: Shell Integration allows creating new firewall rules even if WFC is locked with a password.
Due to the fact that this build uses GRPC instead of WCF, the minimum required .NET Framework version is now 4.6.2 instead of 4.5.
Unfortunately, a clean install is required. You have to uninstall any previous version, select the third option in the uninstaller to keep the firewall rules, then install the new version while preserving the existing firewall rules.
Updated language strings:
310 = Toggle between filtering profiles
501 = Use the shortcuts below to launch various system utilities
Download location: https://binisoft.org/download/wfc6setup.exe
SHA1: 068b9f7bc2870cb1609d714526779067942c20f7
SHA256: 92965864dc52f619d4ba904bb26ac6a82efad62411ea7f3d7eeda4ee8a988cc7
Thank you for your feedback and your support,
Alexandru Dicu-
 1
1
-
-
Notepad++ 8.5.8 has been released. (17-October-2023)
Notepad++ v8.5.8 Release:
https://notepad-plus-plus.org/news/v858-released/
Notepad++ v8.5.8 Change log:
- Fix “Clear Read-Only Flag” command not working immediately regression. (Fix #14138 )
- Fix saving files losing Alternate Data Stream issue. (Fix #1498 , #8451 , #8013 )
- Fix data loss issue due to no room on disk for saving. (Fix #5664 , #14089 )
- Add Win10/Win11 Restart-application feature. (Fix #9722 , #11721 , #11934 )
- Fix user created session being modified behaviour on exit. (Implement part 1 , part 2 , part 3 )
- Improve document list display performance. (Fix #13479 , #12632 )
- Update Scintilla to v5.3.7 & Lexilla to v5.2.7. (Fix #13991 , #14062 )
- fix unwanted Afrikaans installer language issue. (Fix #3844 , #7574 )
- Fix a crash issue while reading settings from cloud. (Fix #14131 )
- Fix security issue CVE-2022-31901. (Fix #13520 )
- Enhance non-saved search text’s persistence in Find dialog combobox while pressing arrow key. (Fix #14174 )
- Make auto-checking of Find InSelection configurable (resizable & can be disabled). (Fix #14108 , #13677 , #12639 )
- Perl enhancement: Update Stylers & the keywords for Perl v5.38. (Fix #14192 )
- Fix “Single Line Uncomment” uncommenting an extra line issue. (Fix #12829 )
- Fix “Next Bookmark” command not resetting current column issue. (Fix #14137 )
- Allow menu command Window->Windows to be assigned a shortcut. (Fix #14179 )
- Fix wrong categories in Shortcuts Mapper. (Fix #13285 )
-
 1
1
-
Bitwarden Editions 2023.9.3 have been released. (17-October-2023)
Release notes & downloads for all editions
Quote- Bug fixes
-
 1
1
-
cURL and libcurl 8.4.0 have been released. (11-October-2023)
Download | News | Releaselogs | Changelog | Release Video |
3 changes & 136 bugfixes.
Fixed in 8.4.0 - October 11, 2023
Changes:
- curl: add support for the IPFS protocols via HTTP gateway
- curl_multi_get_handles: get easy handles from a multi handle
- mingw: delete support for legacy mingw.org toolchain
Bugfixes:
- acinclude.m4: Document proper system truststore on FreeBSD
- appveyor: fix yamlint issues, indent
- appveyor: rewrite batch in PowerShell + CI improvements
- autotools: adjust `CURL_CA_PATH` value to CMake
- autotools: restore `HAVE_IOCTL_*` detections
- base64: also built for curl
- bufq: remove Curl_bufq_skip_and_shift (unused)
- build: delete checks for C89 standard headers
- build: do not publish `HAVE_BORINGSSL`, `HAVE_AWSLC` macros
- cf-socket: simulate slow/blocked receives in debug
- cmake, configure: also link with CoreServices
- cmake: add check for suseconds_t
- cmake: add feature checks for `memrchr` and `getifaddrs`
- cmake: add missing checks
- cmake: delete old `HAVE_LDAP_URL_PARSE` logic
- cmake: detect `HAVE_CLOCK_GETTIME_MONOTONIC_RAW`
- cmake: detect `HAVE_GETADDRINFO_THREADSAFE`
- cmake: detect `sys/wait.h` and `netinet/udp.h`
- cmake: detect TLS-SRP in OpenSSL/wolfSSL/GnuTLS
- cmake: disable unity mode with Windows Unicode + TrackMemory
- cmake: fix `HAVE_LDAP_SSL`, `HAVE_LDAP_URL_PARSE` on non-Windows
- cmake: fix `HAVE_WRITABLE_ARGV` detection
- cmake: fix duplicate symbols when linking tests
- cmake: fix missing `zlib.h` when compiling `libcurltool`
- cmake: fix stderr initialization in unity builds
- cmake: fix the help text to the static build option in CMakeLists.txt
- cmake: fix unity builds for more build combinations
- cmake: fix unity symbol collisions in h2 builds
- cmake: fix unity with Windows Unicode + TrackMemory
- cmake: improve OpenLDAP builds
- cmake: lib `CURL_STATICLIB` fixes (Windows)
- cmake: move global headers to specific checks
- cmake: pre-cache `HAVE_BASENAME` for mingw-w64 and MSVC
- cmake: pre-cache `HAVE_POLL_FINE` on Windows
- cmake: tidy-up `NOT_NEED_LBER_H` detection
- cmake: validate `CURL_DEFAULT_SSL_BACKEND` config value
- configure: check for the capath by default
- configure: remove unused checks
- configure: replace adhoc domain with `localhost` in tests
- configure: sort AC_CHECK_FUNCS
- connect: expire the timeout when trying next
- connect: only start the happy eyeballs timer when needed
- cookie: do not store the expire or max-age strings
- cookie: remove unnecessary struct fields
- cookie: set ⇾ running in cookie_init even if data is NULL
- create-dirs.d: clarify, it also uses --output-dirs
- curl.h: mark CURLSSLBACKEND_NSS as deprecated since 8.3.0
- curl_easy_pause.3: mention h2/h3 buffering
- curl_easy_pause.3: mention it works within callbacks
- curl_easy_pause: set “in callback” true on exit if true
- CURLOPT_DEBUGFUNCTION.3: warn about internal handles
- docs/libcurl/opts/Makefile.inc: add missing manpage files
- docs: adapt SEE ALSO sections to new requirements
- docs: explain how PINNEDPUBLICKEY is independent of VERIFYPEER
- docs: replace made up domains with example.com
- docs: update curl man page references
- docs: use CURLSSLBACKEND_NONE
- doh: inherit DEBUGFUNCTION/DATA
- escape: replace Curl_isunreserved with ISUNRESERVED
- FAQ: How do I upgrade curl.exe in Windows?
- GHA/linux: run singleuse to detect single-use global functions
- GHA: add workflow to compare configure vs. cmake outputs
- h2-proxy: remove left-over mistake in drain_tunnel()
- h2: testcase and fix for pausing h2 streams
- h3: add support for ngtcp2 with AWS-LC builds
- http2: refused stream handling for retry
- http: fix CURL_DISABLE_BEARER_AUTH breakage
- http: h1/h2 proxy unification
- http: remove wrong comment for http_should_fail
- http: use per-request counter to check too large headers
- http_aws_sigv4: fix sorting with empty parts
- idn: fix WinIDN null ptr deref on bad host
- idn: if idn2_check_version returns NULL, return error
- inet_ntop: add typecast to silence Coverity
- lib: disambiguate Curl_client_write flag semantics
- lib: enable hmac for digest as well
- lib: failf/infof compiler warnings
- lib: let the max filesize option stop too big transfers too
- lib: move handling of `data->req.writer_stack` into Curl_client_write()
- lib: provide and use Curl_hexencode
- lib: remove TIME_WITH_SYS_TIME
- lib: use wrapper for curl_mime_data fseek callback
- libssh2: fix error message on failed pubkey-from-file
- libssh: cap SFTP packet size sent
- Makefile.mk: always set `CURL_STATICLIB` for lib (Windows)
- MANUAL.md: change domain to example.com
- misc: better random strings
- MQTT: improve receive of ACKs
- multi: do CURLM_CALL_MULTI_PERFORM at two more places
- multi: fix small timeouts
- multi: remove Curl_multi_dump
- multi: round the timeout up to prevent early wakeups
- multi: set CURLM_CALL_MULTI_PERFORM after switch to DOING_MORE
- openssl: improve ssl shutdown handling
- openssl: use X509_ALGOR_get0 instead of reaching into X509_ALGOR
- pytest: exclude test_03_goaway in CI runs due to timing dependency
- quic: set ciphers/curves the same way regular TLS does
- quiche: fix build error with --with-ca-fallback
- RELEASE-PROCEDURE.md: updated coming release dates
- runtests: display the test status if tests appear hung
- runtests: eliminate a warning on old perl versions
- socks: return error if hostname too long for remote resolve
- src/mkhelp: make generated code pass `checksrc`
- test1056: disable on Windows
- test1474: disable test on NetBSD, OpenBSD and Solaris 10
- test1592: greatly increase the maximum test timeout
- test1903: actually verify the cookies after the test
- test1906: set a lower timeout since it's hit on Windows
- test2600: remove special case handling for USE_ALARM_TIMEOUT
- test650: fix an end tag typo
- test661: return from test early in case of curl error
- test: add missing <feature>s
- tests: close the shell used to start sshd
- tests: fix a race condition in ftp server disconnect
- tests: fix compiler warnings
- tests: Fix zombie processes left behind by FTP tests.
- tests: improve SLOWDOWN test reliability by reducing sent data
- tests: increase lib571 timeout from 3s to 30s
- tests: log the test result code after each libtest
- tests: propagate errors in libtests
- tests: set --expect100-timeout to improve test reliability
- tests: show which curl tool `runtests.pl` is using
- tests: stop overriding the lock timeout
- tftpd: always use curl's own tftp.h
- tool: use our own stderr variable
- tool_cb_wrt: fix debug assertion
- tool_getparam: accept variable expansion on file names too
- tool_setopt: remove unused function tool_setopt_flags
- upload-file.d: describe the file name slash/backslash handling
- url: fall back to http/https proxy env-variable if ws/wss not set
- url: fix netrc info message
- warnless: remove unused functions
- wolfssh: do cleanup in Curl_ssh_cleanup
- wolfssl: allow capath with CURLOPT_CAINFO_BLOB
- wolfssl: if CURLOPT_CAINFO_BLOB is set, ignore the CA files
- wolfssl: ignore errors in CA path
-
 1
1
-
Mullvad Browser 13.0 has been released. (13-October-2023)
Changelog | Update: Auto-update or download.
Changelog
All Platforms
- Updated Firefox to 115.3.1esr
- Bug 40050: FF103 Audit [tor-browser-spec]
- Bug 40051: FF104 Audit [tor-browser-spec]
- Bug 40052: FF105 Audit [tor-browser-spec]
- Bug 40053: FF106 Audit [tor-browser-spec]
- Bug 40054: FF107 Audit [tor-browser-spec]
- Bug 40055: FF108 Audit [tor-browser-spec]
- Bug 40056: FF109 Audit [tor-browser-spec]
- Bug 40057: FF110 Audit [tor-browser-spec]
- Bug 40058: FF111 Audit [tor-browser-spec]
- Bug 40059: FF112 Audit [tor-browser-spec]
- Bug 40060: FF113 Audit [tor-browser-spec]
- Bug 40061: FF114 Audit [tor-browser-spec]
- Bug 40062: FF115 Audit [tor-browser-spec]
- Bug 66: Localize Mullvad Browser [mullvad-browser]
- Bug 166: Enable built-in URL anti-tracking query parameters stripping [mullvad-browser]
- Bug 175: Change the default start window size from 1000x1000 [mullvad-browser]
-
Bug 177: Change help links in
about:preferencesand menu [mullvad-browser] - Bug 183: Rebase Mullvad Browser to Firefox 115 [mullvad-browser]
- Bug 195: Choose which locales to translate Mullvad Browser to [mullvad-browser]
- Bug 196: Enumerate Mullvad Browser-specific strings for localization [mullvad-browser]
- Bug 199: Mullvad Browser changes required to use Mullvad Browser-specific localization strings [mullvad-browser]
- Bug 208: Improve letterboxing's dimensions [mullvad-browser]
- Bug 211: Change "Mullvad Browser Home" to "New tab" [mullvad-browser]
- Bug 213: Add search engines to the default list [mullvad-browser]
- Bug 214: Enable cross-tab identity leak protection in "quiet" mode [mullvad-browser]
- Bug 215: Update re-adds manually removed default toolbar buttons [mullvad-browser]
- Bug 218: uBO and Mullvad Browser Extension hidden in unified extensions panel [mullvad-browser]
- Bug 220: "Firefox Suggest" string appears when search matches a bookmark [mullvad-browser]
- Bug 223: Trademarks in the about popup are not translated [mullvad-browser]
- Bug 226: First window after update should go to the user-friendly release page on GitHub [mullvad-browser]
- Bug 228: Remove popup asking for preferred language on websites [mullvad-browser]
- Bug 231: Fix the Security Level "read more" link in popup/settings panel [mullvad-browser]
- Bug 243: Make sure about:mullvadbrowser is treated as a new tab page [mullvad-browser]
- Bug 26277: When "Safest" setting is enabled searching using duckduckgo should always use the Non-Javascript site for searches [tor-browser]
- Bug 30556: Re-evaluate letterboxing dimension choices [tor-browser]
- Bug 33282: Increase the max width of new windows [tor-browser]
- Bug 33955: Selecting "Copy image" from menu leaks the source URL to the clipboard. This data is often dereferenced by other applications. [tor-browser]
- Bug 41327: Disable UrlbarProviderInterventions [tor-browser]
- Bug 41477: Review some extensions.- preferences [tor-browser]
- Bug 41496: Review 000-tor-browser.js and 001-base-profile.js for 115 [tor-browser]
- Bug 41528: Hard-coded English "based on Mozilla Firefox" appears in version in "About" dialog [tor-browser]
- Bug 41576: ESR115: ensure no remote calls for weather & addon suggestions [tor-browser]
- Bug 41581: ESR115: figure out extension pinning / unified Extensions [tor-browser]
- Bug 41642: Do not hide new PBM in the hamburger menu if auto PBM is not enabled [tor-browser]
- Bug 41675: Remove javascript.options.large_arraybuffers [tor-browser]
- Bug 41691: "Firefox Suggest" text appearing in UI [tor-browser]
- Bug 41727: WebRTC privacy-hardening settings [tor-browser]
- Bug 41739: Remove "Website appearance" [tor-browser]
- Bug 41740: ESR115: change devicePixelRatio spoof to 2 in alpha for testing [tor-browser]
- Bug 41752: Review changes done by Bug 41565 [tor-browser]
- Bug 41765: TTP-02-006 WP1: Information leaks via custom homepage (Low) [tor-browser]
- Bug 41774: Hide the new "Switching to a new device" help menu item [tor-browser]
- Bug 41791: Copying page contents also puts the source URL on the clipboard [tor-browser]
- Bug 41797: Lock RFP in release builds [tor-browser]
- Bug 41833: Reload extensions on new identity [tor-browser]
- Bug 41834: Hide "Can't Be Removed - learn more" menu line for uninstallable add-ons [tor-browser]
- Bug 41874: Visual & A11 regressions in add-on badges [tor-browser]
- Bug 41876: Remove Firefox View from title bar [tor-browser]
- Bug 41877: NoScript seems to be blocking by default in the first 115-based testbuild [tor-browser]
- Bug 41881: Developer tools/Network/New Request remembers requests [tor-browser]
- Bug 41903: The info icon on the language change prompt is not shown [tor-browser]
- Bug 41936: Review Mozilla 1770158: Use double-conversion library instead of dtoa for string-to-double conversion [tor-browser]
- Bug 41937: Review Mozilla 1780014: Add specific telemetry for conservative and first-try handshakes [tor-browser]
- Bug 41938: Review Mozilla 1769994: On systems with IPv6 preferred DNS resolution clients will fail to connect when "localhost" is used as host for the WebSocket server [tor-browser]
- Bug 41939: Review Mozilla 1728871: Support fetching data from Remote Setting [tor-browser]
- Bug 41940: Review Mozilla 1739348: When a filetype is set to "always ask" and the user makes a save/open choice in the dialog, we should not also open the downloads panel [tor-browser]
- Bug 41941: Review Mozilla 1775254: Improve Math.pow accuracy for large exponents [tor-browser]
- Bug 41943: Lock javascript.options.spectre.disable_for_isolated_content to false [tor-browser]
- Bug 41945: Review Mozilla 1783019: Add a cookie banner service to automatically handle website cookie banners [tor-browser]
- Bug 41946: Review Mozilla 1782579: Add a locale parameter to the text recognition API [tor-browser]
- Bug 41947: Review Mozilla 1779005: Broken since Firefox 102.0: no instant fallback to direct connection when proxy became unreachable while runtime [tor-browser]
- Bug 41949: Review Mozilla 1782578: Implement a context menu modal for text recognition [tor-browser]
- Bug 41950: Review Mozilla 1788668: Add the possibility to check that the clipboard contains some pdfjs stuff [tor-browser]
- Bug 41951: Review Mozilla 1790681: Enable separatePrivateDefault by default [tor-browser]
- Bug 41959: Review Mozilla 1795944: Remove descriptionheightworkaround [tor-browser]
- Bug 41961: Review Mozilla 1798868: Hide cookie banner handling UI by default [tor-browser]
- Bug 41969: Review Mozilla 1746983: Re-enable pingsender2 [tor-browser]
- Bug 41970: Review Mozilla 17909270: WebRTC bypasses Network settings & proxy.onRequest [tor-browser]
- Bug 41973: Custom wingpanels don't line up with their toolbar icons in 13.0 alpha [tor-browser]
- Bug 41981: Review Mozilla 1800675: Add about:preferences entry for cookie banner handling [tor-browser]
- Bug 41983: Review Mozilla 1770447: Create a reusable "support-link" widget [tor-browser]
- Bug 41984: Rename languageNotification.ftl to base-browser.ftl [tor-browser]
- Bug 42013: Review Mozilla 1834374: Do not call EmptyClipboard() in nsBaseClipboard destructor [tor-browser]
- Bug 42014: Review Mozilla 1832791: Implement a Remote Settings for the Quarantined Domains pref [tor-browser]
- Bug 42015: Review Mozilla 1830890: Keep a history window of WebRTC stats for about:webrtc [tor-browser]
- Bug 42019: Empty browser's clipboard on browser shutdown [tor-browser]
- Bug 42022: Prevent extension search engines from breaking the whole search system [tor-browser]
- Bug 42026: Disable cookie banner service and UI. [tor-browser]
- Bug 42027: Create a Base Browser version of migrateUI [tor-browser]
- Bug 42029: Defense-in-depth: disable non-proxied UDP WebRTC [tor-browser]
- Bug 42037: Disable about:firefoxview [tor-browser]
- Bug 42043: Disable gUM: media.devices.enumerate.legacy.enabled [tor-browser]
- Bug 42046: Remove XUL layout hacks from base browser [tor-browser]
- Bug 42050: Bring back Save As... dialog as default [tor-browser]
- Bug 42061: Move the alpha update channel creation to a commit on its own [tor-browser]
- Bug 42083: RemoteSecuritySettings.init throws error in console [tor-browser]
- Bug 42084: Race condition with language preferences may make spoof_english ineffective [tor-browser]
-
Bug 42094: Disable
media.aboutwebrtc.hist.enabledas security in-depth [tor-browser] - Bug 42138: Disable apz.overscroll.enabled pref [tor-browser]
- Bug 42159: Responsive Design Mode not working correctly [tor-browser]
- Bug 42166: New identity dialog missing accessible name [tor-browser]
- Bug 42167: Make the preference auto-focus more reliable [tor-browser]
- Bug 40893: Update (Noto) fonts for 13.0 [tor-browser-build]
- Bug 40924: Customize MOZ_APP_REMOTINGNAME instead of passing --name and --class [tor-browser-build]
- Bug 40937: First window after update should go to the user-friendly release page on GitHub [tor-browser-build]
Windows
- Bug 40737: Revert backout of Mozilla's fix for bug 1724777 [tor-browser]
- Bug 41798: Stop building private_browsing.exe on Windows [tor-browser]
- Bug 41806: Prevent Private Browsing start menu item to be added automatically [tor-browser]
- Bug 41942: Review Mozilla 1682520: Use the WER runtime exception module to catch early crashes [tor-browser]
- Bug 41944: Review Mozilla 1774083: Add Surrogate COM Server to handle native Windows notifications when Firefox is closed. [tor-browser]
- Bug 42008: Review Mozilla 1808146: Copying images from Pixiv and pasting them in certain programs is broken [tor-browser]
- Bug 42010: Review Mozilla 1810...
-
 1
1
-
The Tor Browser 13.0 (All Platforms) has been released. (12-October-2023)
Tor Browser 13.0 is now available from the Tor Browser download page and also from our distribution directory.Blog/Announcement | Full Changelog
Full changelog
The full changelog since Tor Browser 12.5.6 is:
-
All Platforms
- Updated tor to 0.4.8.7
- Updated OpenSSL to 3.0.11
- Bug tor-browser-spec#40050: FF103 Audit
- Bug tor-browser-spec#40051: FF104 Audit
- Bug tor-browser-spec#40052: FF105 Audit
- Bug tor-browser-spec#40053: FF106 Audit
- Bug tor-browser-spec#40054: FF107 Audit
- Bug tor-browser-spec#40055: FF108 Audit
- Bug tor-browser-spec#40056: FF109 Audit
- Bug tor-browser-spec#40057: FF110 Audit
- Bug tor-browser-spec#40058: FF111 Audit
- Bug tor-browser-spec#40059: FF112 Audit
- Bug tor-browser-spec#40060: FF113 Audit
- Bug tor-browser-spec#40061: FF114 Audit
- Bug tor-browser-spec#40062: FF115 Audit
- Bug tor-browser#26277: When the “Safest” setting is enabled, searching using duckduckgo should always use the Non-Javascript site for searches
- Bug tor-browser#40577: Add “suggest url” in DDG onion's manifest
- Bug tor-browser#40938: Migrate remaining torbutton functionality to tor-browser
- Bug tor-browser#41092: Enable tracking query parameters stripping
- Bug tor-browser#41327: Disable UrlbarProviderInterventions
- Bug tor-browser#41399: Update Mozilla's patch for Bug 1675054 to enable brotli encoding for HTTP onions as well
- Bug tor-browser#41477: Review some extensions.* preferences
- Bug tor-browser#41496: Review 000-tor-browser.js and 001-base-profile.js for 115
- Bug tor-browser#41576: ESR115: ensure no remote calls for weather & add-on suggestions
- Bug tor-browser#41605: Remove unused assets from torbutton (preferences-mobile.css)
- Bug tor-browser#41675: Remove javascript.options.large_arraybuffers
- Bug tor-browser#41727: WebRTC privacy-hardening settings
- Bug tor-browser#41740: ESR115: change devicePixelRatio spoof to 2 in alpha for testing
- Bug tor-browser#41752: Review changes done by Bug 41565
- Bug tor-browser#41796: Rebase Tor Browser to Firefox 115
- Bug tor-browser#41797: Lock RFP in release builds
- Bug tor-browser#41934: Websocket raises DOMException on http onions in 13.0a1
- Bug tor-browser#41936: Review Mozilla 1770158: Use double-conversion library instead of dtoa for string-to-double conversion
- Bug tor-browser#41937: Review Mozilla 1780014: Add specific telemetry for conservative and first-try handshakes
- Bug tor-browser#41938: Review Mozilla 1769994: On systems with IPv6 preferred DNS resolution clients will fail to connect when “localhost” is used as host for the WebSocket server
- Bug tor-browser#41939: Review Mozilla 1728871: Support fetching data from Remote Setting
- Bug tor-browser#41941: Review Mozilla 1775254: Improve Math.pow accuracy for large exponents
- Bug tor-browser#41943: Lock javascript.options.spectre.disable_for_isolated_content to false
- Bug tor-browser#41945: Review Mozilla 1783019: Add a cookie banner service to automatically handle website cookie banners
- Bug tor-browser#41946: Review Mozilla 1782579: Add a locale parameter to the text recognition API
- Bug tor-browser#41947: Review Mozilla 1779005: Broken since Firefox 102.0: no instant fallback to direct connection when proxy became unreachable while runtime
- Bug tor-browser#41950: Review Mozilla 1788668: Add the possibility to check that the clipboard contains some pdfjs stuff
- Bug tor-browser#41951: Review Mozilla 1790681: Enable separatePrivateDefault by default
- Bug tor-browser#41959: Review Mozilla 1795944: Remove descriptionheightworkaround
- Bug tor-browser#41960: Review Mozilla 1797896: Proxy environment variables should be upper case / case insensitive
- Bug tor-browser#41961: Review Mozilla 1798868: Hide cookie banner handling UI by default
- Bug tor-browser#41969: Review Mozilla 1746983: Re-enable pingsender2
- Bug tor-browser#41970: Review Mozilla 17909270: WebRTC bypasses Network settings & proxy.onRequest
- Bug tor-browser#41984: Rename languageNotification.ftl to base-browser.ftl
- Bug tor-browser#42013: Review Mozilla 1834374: Do not call EmptyClipboard() in nsBaseClipboard destructor
- Bug tor-browser#42014: Review Mozilla 1832791: Implement a Remote Settings for the Quarantined Domains pref
- Bug tor-browser#42015: Review Mozilla 1830890: Keep a history window of WebRTC stats for about:WebRTC
- Bug tor-browser#42019: Empty browser's clipboard on browser shutdown
- Bug tor-browser#42026: Disable cookie banner service and UI.
- Bug tor-browser#42029: Defense-in-depth: disable non-proxied UDP WebRTC
- Bug tor-browser#42034: aboutTBUpdate.dtd is duplicated
- Bug tor-browser#42043: Disable gUM: media.devices.enumerate.legacy.enabled
- Bug tor-browser#42061: Move the alpha update channel creation to a commit on its own
- Bug tor-browser#42084: Race condition with language preferences may make spoof_english ineffective
- Bug tor-browser#42085: NEWNYM signal missing on Whonix
-
Bug tor-browser#42094: Disable
media.aboutwebrtc.hist.enabledas security in-depth - Bug tor-browser#42120: Use foursquare as domain front for snowflake
- Bug tor-browser-build#40887: Update Webtunnel version to 38eb5505
-
Windows + macOS + Linux
- Updated Firefox to 115.3.1esr
- Bug tor-browser#30556: Re-evaluate letterboxing dimension choices
- Bug tor-browser#32328: Improve error recovery from the red screen of death
- Bug tor-browser#33282: Increase the max width of new windows
- Bug tor-browser#33955: Selecting “Copy image” from menu leaks the source URL to the clipboard. This data is often dereferenced by other applications.
- Bug tor-browser#40175: Connections in reader mode are not FPI
- Bug tor-browser#40982: Cleanup maps in tor-circuit-display
- Bug tor-browser#40983: Move not UI-related torbutton.js code to modules
- Bug tor-browser#41165: Crash with debug assertions enabled
- Bug tor-browser#41333: Modernize Tor Browser's new-tab page (about:tor)
- Bug tor-browser#41423: about:tor semantic and accessibility problems
- Bug tor-browser#41528: Hard-coded English “based on Mozilla Firefox” appears in version in “About” dialog
- Bug tor-browser#41581: ESR115: figure out extension pinning / unified Extensions
- Bug tor-browser#41639: Fix the wordmark (title and background) of the “About Tor Browser” window
- Bug tor-browser#41642: Do not hide new PBM in the hamburger menu if auto PBM is not enabled
- Bug tor-browser#41651: Use moz-toggle in connection preferences
- Bug tor-browser#41691: “Firefox Suggest” text appearing in UI
- Bug tor-browser#41717: Bookmark toolbar visibility on new tabs is not honored when new tab page is not about:blank
- Bug tor-browser#41739: Remove “Website appearance”
- Bug tor-browser#41741: Refactor the domain isolator and new circuit
- Bug tor-browser#41765: TTP-02-006 WP1: Information leaks via custom homepage (Low)
- Bug tor-browser#41766: TTP-02-001 WP1: XSS in TorConnect's captive portal (Info)
- Bug tor-browser#41771: Decide what to do for firefoxview
- Bug tor-browser#41774: Hide the new “Switching to a new device” help menu item
- Bug tor-browser#41791: Copying page contents also puts the source URL on the clipboard
- Bug tor-browser#41812: Review layout for XUL elements
- Bug tor-browser#41813: Look out for links missing underlines in ESR 115-based alphas
- Bug tor-browser#41821: Fix the proxy type in the proxy modal of about:preferences in 13.0
- Bug tor-browser#41822: The default browser button came back on 115
- Bug tor-browser#41833: Reload extensions on new identity
- Bug tor-browser#41834: Hide “Can't Be Removed - learn more” menu line for uninstallable add-ons
- Bug tor-browser#41842: Remove the old removal logics from Torbutton
- Bug tor-browser#41844: Stop using the control port directly
- Bug tor-browser#41845: Stop forcing (bad) pref values for non-PBM users
- Bug tor-browser#41852: Review the Tor Check Service UX
- Bug tor-browser#41864: TOR_CONTROL_HOST and TOR_SOCKS_HOST do not work as expected when the browser launches tor
- Bug tor-browser#41865: Use --text-color-deemphasized rather than --panel-description-color
- Bug tor-browser#41874: Visual & A11 regressions in add-on badges
- Bug tor-browser#41876: Remove Firefox View from title bar
- Bug tor-browser#41877: NoScript seems to be blocking by default in the first 115-based testbuild
- Bug tor-browser#41881: Developer tools/Network/New Request remembers requests
- Bug tor-browser#41886: Downloads drop-down panel has new-line/line-break between every word in the 'Be careful opening downloads' warning
- Bug tor-browser#41904: The log textarea doesn't resize anymore
- Bug tor-browser#41906: Hide about:preferences#privacy > DNS over HTTPS section
- Bug tor-browser#41907: The bootstrap is interrupted without any errors if the process becomes ready when already bootstrapping
- Bug tor-browser#41912: “Use Current Bridges” is shown for users even when there aren't any current bridges
- Bug tor-browser#41922: Unify the bridge line parsers
- Bug tor-browser#41923: The path normalization results in warnings
- Bug tor-browser#41924: Small refactors for TorProcess
- Bug tor-browser#41925: Remove the torbutton startup observer
- Bug tor-browser#41926: Refactor the control port client implementation
- Bug tor-browser#41931: Regression: new window leaks outer window
- Bug tor-browser#41935: Improve new window & letterboxing dimensions
- Bug tor-browser#41940: Review Mozilla 1739348: When a filetype is set to “always ask” and the user makes a save/open choice in the dialog, we should not also open the downloads panel
- Bug tor-browser#41949: Review Mozilla 1782578: Implement a context menu modal for text recognition
- Bug tor-browser#41954: Inputs in the request a bridge dialog are cut-off in 13.0 alpha
- Bug tor-browser#41957: Revert to Fx's default identity block style for internal pages
- Bug tor-browser#41958: Console error when closing tor browser with about:preferences open
-
Bug tor-browser#41964:
emojiAnnotationsnot defined in time in connection preferences - Bug tor-browser#41965: TorConnect error when opening browser tools
- Bug tor-browser#41971: Update Tails URL in downloads warning
- Bug tor-browser#41973: Custom wingpanels don't line up with their toolbar icons in 13.0 alpha
- Bug tor-browser#41974: De-emphasized text in custom components is no longer gray in 13.0 alpha
- Bug tor-browser#41975: Downloads warning text too narrow in 13.0 alpha
- Bug tor-browser#41976: Bottom padding on collapsed bridge cards has increased in 13.0 alpha
- Bug tor-browser#41977: Hide the “Learn more” link in bridge cards
- Bug tor-browser#41980: Circuit display headline is misaligned in 13.0 alpha
- Bug tor-browser#41981: Review Mozilla 1800675: Add about:preferences entry for cookie banner handling
- Bug tor-browser#41983: Review Mozilla 1770447: Create a reusable “support-link” widget
- Bug tor-browser#41986: Fix the control port password handling
- Bug tor-browser#41994: CSS (and other assets) of some websites blocked in 13.0 alpha
- Bug tor-browser#42022: Prevent extension search engines from breaking the whole search system
- Bug tor-browser#42027: Create a Base Browser version of migrateUI
- Bug tor-browser#42037: Disable about:firefoxview
- Bug tor-browser#42041: TBB --allow-remote mixes up with plain Firefox
- Bug tor-browser#42045: Circuit panel overflows with long ipv6 addresses
- Bug tor-browser#42046: Remove XUL layout hacks from base browser
- Bug tor-browser#42047: Remove layout hacks from tor browser preferences
- Bug tor-browser#42050: Bring back Save As... dialog as default
- Bug tor-browser#42073: Add simplified onion pattern to the new homepage
- Bug tor-browser#42075: Fix link spacing and underline on new homepage
- Bug tor-browser#42079: TorConnect: handle switching from Bootstrapped to Configuring state
- Bug tor-browser#42083: RemoteSecuritySettings.init throws error in console
- Bug tor-browser#42091: Onion authorization prompt overflows
- Bug tor-browser#42092: Onion services key table display problems.
- Bug tor-browser#42098: Implement Windows installer icons
- Bug tor-browser#42100: Connect Assist dropdown text not centered
- Bug tor-browser#42102: TorProcess says the SOCKS port is not valid even though it is
- Bug tor-browser#42109: Onion services keys table has empty column headers.
- Bug tor-browser#42110: Add a utility module for shared UI methods needed for several tor browser components
- Bug tor-browser#42126: moat and connect assist broken for people who can't reach domain front
- Bug tor-browser#42129: Disable the Tor restart prompt if shouldStartAndOwnTor is false
- Bug tor-browser#42131: Tor Browser 13.0a5 does not track circuits created before Tor Browser started
- Bug tor-browser#42132: The new control port handling in Tor Browser 13 breaks a Tails security feature
- Bug tor-browser#42138: Disable apz.overscroll.enabled pref
- Bug tor-browser#42155: Drop the unused code for the old bridge removal warning
- Bug tor-browser#42159: Responsive Design Mode not working correctly
- Bug tor-browser#42160: Allow specifying a TOR_PROVIDER=none to configure only the proxy settings during the TorProviderBuilder initialization
- Bug tor-browser#42166: New identity dialog missing accessible name
- Bug tor-browser#42167: Make the preference auto-focus more reliable
- Bug tor-browser-build#40821: The update details URL is wrong in alphas
- Bug tor-browser-build#40893: Update (Noto) fonts for 13.0
- Bug tor-browser-build#40924: Customize MOZ_APP_REMOTINGNAME instead of passing --name and --class
- Bug tor-browser-build#40938: Copy the new tor-browser.ftl file to the appropriate directory
-
Windows + Android
- Bug tor-browser-build#40930: Upate zlib to 1.3 after 13.0a3
-
Windows
- Bug tor-browser#40737: Revert backout of Mozilla's fix for bug 1724777
- Bug tor-browser#41658: Create new installer icons for Windows
- Bug tor-browser#41798: Stop building private_browsing.exe on Windows
- Bug tor-browser#41806: Prevent Private Browsing start menu item to be added automatically
- Bug tor-browser#41942: Review Mozilla 1682520: Use the WER runtime exception module to catch early crashes
- Bug tor-browser#41944: Review Mozilla 1774083: Add Surrogate COM Server to handle native Windows notifications when Firefox is closed.
- Bug tor-browser#42008: Review Mozilla 1808146: Copying images from Pixiv and pasting them in certain programs is broken
- Bug tor-browser#42010: Review Mozilla 1810641: Enable overscroll on Windows on all channels
- Bug tor-browser#42087: Implement Windows application icons
- Bug tor-browser-build#40954: Implement Windows installer icons
-
macOS
- Bug tor-browser#41948: Review Mozilla 1782981: Hide the text recognition context menu if the macOS version doesn't support APIs
- Bug tor-browser#41955: Update macOS volume window background
- Bug tor-browser#41982: Review Mozilla 1762392: Add Cocoa platform support for paste files
- Bug tor-browser#42057: Disable Platform text-recognition functionality
- Bug tor-browser#42078: Implement MacOS application icons
- Bug tor-browser#42147: Add browser.helperApps.deleteTempFileOnExit to our profile
-
Linux
- Bug tor-browser#41509: After update, KDE Plasma identifies Tor Browser Nightly window group as “firefox-nightly”
- Bug tor-browser#41884: Linux: set browser.tabs.searchclipboardfor.middleclick to false
- Bug tor-browser#42088: Implement Linux application icons
- Bug tor-browser-build#40576: Fontconfig warning: remove 'blank' configuration
-
Android
- Updated GeckoView to 115.3.1esr
- Bug tor-browser#41878: firefox-mobile: refactor tor bootstrap off deleted onboarding path
- Bug tor-browser#41882: Update DuckDuckGo icons
- Bug tor-browser#41911: Firefox-Android tor bootstrap connect button css broken
- Bug tor-browser#41928: Backport Android-specific security fixes from Firefox 116 to ESR 102.14 / 115.1 - based Tor Browser
- Bug tor-browser#41972: Disable Firefox onboarding in 13.0
- Bug tor-browser#41990: Review Mozilla 1811531: Add 'site' query parameter to Pocket sponsored stories request
- Bug tor-browser#41991: Review Mozilla 1812518: Allow a custom View for 3rd party downloads
- Bug tor-browser#41993: Review Mozilla 1810761: Add API for saving a PDF
- Bug tor-browser#41996: App includes com.google.android.gms.permission.AD_ID permission
- Bug tor-browser#41997: com.adjust.sdk.Adjust library enables AD_ID permission even though we aren't using it
- Bug tor-browser#41999: TB13.0a2 android: center text on connect button
- Bug tor-browser#42001: Hide 'Open links in external app' settings option and force defaults
- Bug tor-browser#42002: Review Mozilla 1809305: Allow user to copy an image to the clipboard
- Bug tor-browser#42003: Review Mozilla 1819431: Reimplement default browser notification with Nimbus Messaging equivalent
- Bug tor-browser#42004: Review Mozilla 1818015: Use a custom tab or the view we use for Sync onboarding for the Privacy button
- Bug tor-browser#42005: Review Mozilla 1816932: Add Maps to app links common sub domains
- Bug tor-browser#42006: Review Mozilla 1817726: Allow sharing current tab URL from Android's Recents (App Overview) screen.
- Bug tor-browser#42007: Review Mozilla 1805450: Allow users to submit site support requests in Fenix
- Bug tor-browser#42012: Review Mozilla 1810629: add an Android shortcut to go straight to the login and passwords page
- Bug tor-browser#42016: Review Mozilla 1832069: Implement Google Play Referrer Library to fetch referrer URL
- Bug tor-browser#42018: Rebase Firefox for Android to 115.2.1
- Bug tor-browser#42023: Remove FF what's new from Android
- Bug tor-browser#42038: TBA Alpha - inscriptions Tor Browser Alpha and FireFox Browser simultaneously on the start screen
- Bug tor-browser#42074: YEC 2023 Takeover for Android Stable
- Bug tor-browser#42076: Theme is visible in options, but shouldn't be
- Bug tor-browser#42089: Disable the Cookie Banner Reduction site support requests (Mozilla 1805450)
- Bug tor-browser#42114: Disable Allow sharing current tab URL from Android's Recents screen in private browsing mode
- Bug tor-browser#42115: Enhanced Tracking Protection can still be enabled
- Bug tor-browser#42122: playstore console crashes: java.lang.NoSuchMethodError
- Bug tor-browser#42133: Remove “Total Cookie Protection” popup
- Bug tor-browser#42134: Remove Android icon shortcuts
- Bug tor-browser#42156: Screenshot allowing still blocks homescreen (android)
- Bug tor-browser#42157: Fix Help button URL
- Bug tor-browser#42165: Remove “Add to shortcuts” and “Remove from shortcuts” buttons
- Bug tor-browser#42158: Remove “Customize Homepage” button
- Bug tor-browser-build#40740: Tor Browser for Android's snowflake ClientTransportPlugin seems to be out of date
- Bug tor-browser-build#40919: Fix nimbus-fml reproducibility of 13.0a2-build1
- Bug tor-browser-build#40941: Remove PT process options on Android
-
Build System
-
All Platforms
- Updated Go to 1.21.1
-
Bug tor-browser#42130: Add support for specifying the branch in
tb-dev rebase-on-default - Bug tor-browser-build#31588: Be smarter about vendoring for Rust projects
- Bug tor-browser-build#40089: Clean up usage of get-moz-build-date script
- Bug tor-browser-build#40410: Get rid of python2
- Bug tor-browser-build#40487: Bump Python version
- Bug tor-browser-build#40741: Update browser and tor-android-service projects to pull data from pt_config.json
- Bug tor-browser-build#40802: Drop the patch for making WASI reproducible
- Bug tor-browser-build#40829: Review and standardize naming scheme for browser installer/package artifacts
- Bug tor-browser-build#40854: Update to OpenSSL 3.0
- Bug tor-browser-build#40855: Update toolchains for Mozilla 115
- Bug tor-browser-build#40868: Bump Rust to 1.69.0
- Bug tor-browser-build#40880: The README doesn't include some dependencies needed for building incrementals
- Bug tor-browser-build#40886: Update README with instructions for Arch linux
- Bug tor-browser-build#40898: Add doc from tor-browser-spec/processes/ReleaseProcess to gitlab issue templates
- Bug tor-browser-build#40908: Enable the --enable-gpl config flag in tor to bring in PoW functionality
- Bug tor-browser-build#40929: Update go to 1.21 series after 13.0a3
- Bug tor-browser-build#40932: Remove appname_bundle_android, appname_bundle_macos, appname_bundle_linux, appname_bundle_win32, appname_bundle_win64 from projects/release/update_responses_config.yml
- Bug tor-browser-build#40935: Fix fallout from build target rename in signing scripts
- Bug tor-browser-build#40948: Remove lyrebird-vendor sha256sum in nightly
- Bug tor-browser-build#40957: Expired subkey warning on Tor Browser GPG verification
- Bug tor-browser-build#40972: Handle Mullvad Browser in the changelog script and group entries by project
-
Windows + macOS + Linux
- Bug tor-browser#41967: Add a Makefile recipe to create multi-lingual dev builds
- Bug tor-browser-build#40149: Remove patching of nightly update URL
- Bug tor-browser-build#40615: Consider adding a readme to the fonts directory
- Bug tor-browser-build#40907: Sometimes debug information are not deterministic with Clang 16.0.4
- Bug tor-browser-build#40922: Use base-browser.ftl instead of languageNotification.ftl
- Bug tor-browser-build#40931: Fix incrementals after tor-browser-build#40829
- Bug tor-browser-build#40933: Fix generating incrementals between 12.5.x and 13.0
- Bug tor-browser-build#40942: Use the branch to build Base Browser
- Bug tor-browser-build#40944: After #40931, updates_responses is using incremental.mar files as if they were non-incremental mar files
- Bug tor-browser-build#40947: Remove migrate_langs from tools/signing/nightly/update-responses-base-config.yml
- Bug tor-browser-build#40956: Allow testing the updater also with release and alpha channel
-
Windows
- Bug tor-browser#41995: Generated headers on Windows aren't reproducible
- Bug tor-browser-build#40832: Unify mingw-w64-clang 32+64 bits
-
Bug tor-browser-build#40940: Change position of the
install|portablein the builds filenames
-
macOS
- Bug tor-browser#42035: Update tools/torbrowser/ scripts to support macOS dev environment
- Bug tor-browser-build#40943: Update libdmg-hfsplus to include our uplifted patch
- Bug tor-browser-build#40951: Firefox fails to build for macOS after tor-browser-build#40938
-
Linux
- Bug tor-browser#42071: tor-browser deployed format changed breaking fetch.sh
- Bug tor-browser-build#40102: Move from Debian Jessie to Debian Stretch for our Linux builds
- Bug tor-browser-build#40971: Stop shipping Linux i686 debug archive until we actually produce the symbols
-
Android
- Bug tor-browser#41899: Use LLD for Android
- Bug tor-browser-build#40867: Create a RBM project for the unified Android repository
- Bug tor-browser-build#40917: Remove the uniffi-rs project
- Bug tor-browser-build#40918: The commit hash is still not displayed about:buildconfig on Android
- Bug tor-browser-build#40920: Non-deterministic generation of baseline.profm file in Android apks
- Bug tor-browser-build#40963: Tor Browesr 13.0 torbrowser-testbuild-android* targets fail to build
- Bug tor-browser-build#40974: firefox-android fails to build in release
-
All Platforms
-
 2
2
-
All Platforms
-
The free edition of Macrium Reflect 8 has been updated to 8.0.7690 for a security fix.
QuoteSecurity Update - CVE-2023-43896
This update applies a security patch to psmounterex.sys. We advise you to install this release to ensure the security of your system.Autoupdate or download:
Version specific: Macrium Reflect Free Edition (v8.0.7783) 64-bit: https://download.macrium.com/reflect/v8/v8.0.7783/reflect_setup_free_x64.exe 32-bit: https://download.macrium.com/reflect/v8/v8.0.7783/reflect_setup_free_x86.exe or version non-specific: Macrium Reflect Free Latest Version 8 (64-bit) https://updates.macrium.com/Reflect/v8/getmsi.asp?edition=0&type=99&arch=1&redirect=Y Macrium Reflect Free Latest Version 8 (32-bit) https://updates.macrium.com/Reflect/v8/getmsi.asp?edition=0&type=99&arch=0&redirect=YThe payware edition has also been updated with a similar security fix.
-
 2
2
-
-
Hello @homeslice and welcome back:
While you are waiting for the next qualified/approved malware removal expert helper to weigh in on your topic, and even though you may have run the following Malwarebytes utility, or its subsets, please carefully follow these instructions:
- Download the Malwarebytes Support Tool.
- In your Downloads folder, open the mb-support-x.x.x.xxx.exe file.
- In the User Account Control (UAC) pop-up window, click Yes to continue the installation.
- Run the MBST Support Tool.
- In the left navigation pane of the Malwarebytes Support Tool, click Advanced.
- In the Advanced Options, click only Gather Logs. A status diagram displays the tool is Getting logs from your computer. WARNING: Do Not click the Repair System under Advanced unless requested to by a Malwarebytes support agent or authorized helper.
- A zip file named mbst-grab-results.zip will be saved to the Public desktop, please attach that file in your next reply to this topic. Please do NOT copy and paste.
For the short time between when you post the diagnostic logs, and when your helper weighs in, please take no further self-directed remedial actions that will invalidate the diagnostic logs you will have posted.
Thank you.
-
Bitwarden Editions 2023.9.2 have been released. (11-October-2023)
Release notes & downloads for all editions
- Bug fixes
-
 1
1
-
Hello @medic54 and
 :
:
While you are waiting for the next qualified/approved malware removal expert helper to weigh in on your topic, and even though you may have run the following Malwarebytes utility, or its subsets, please carefully follow these instructions:
- Download the Malwarebytes Support Tool.
- In your Downloads folder, open the mb-support-x.x.x.xxx.exe file.
- In the User Account Control (UAC) pop-up window, click Yes to continue the installation.
- Run the MBST Support Tool.
- In the left navigation pane of the Malwarebytes Support Tool, click Advanced.
- In the Advanced Options, click only Gather Logs. A status diagram displays the tool is Getting logs from your computer. WARNING: Do Not click the Repair System under Advanced unless requested to by a Malwarebytes support agent or authorized helper.
- A zip file named mbst-grab-results.zip will be saved to the Public desktop, please attach that file in your next reply to this topic. Please do NOT copy and paste.
For the short time between when you post the diagnostic logs, and when your helper weighs in, please take no further self-directed remedial actions that will invalidate the diagnostic logs you will have posted.
Thank you.
-
Version 118.0.2, first offered to Release channel users on October 10, 2023
Fixed
-
Fixed games not loading on betsoft.com (bug 1856145)
-
Fixed printing issues for some SVG images (bug 1853727)
-
Fixed CORS XHR with authentication no longer working (bug 1855650)
-
Fixed h264 WebRTC video not working in some contexts (bug 1855636)
-
Fixed Firefox Translations not working on some pages (bugs 1841656 - 1855307)
-
Stability fixes (bugs 1851991 - 1799326 - 1856637)
-
 1
1
-
-
Hello @Dinesh6252 and welcome back:
While you are waiting for the next qualified/approved malware removal expert helper to weigh in on your topic, and even though you may have run the following Malwarebytes utility, or its subsets, please carefully follow these instructions:
- Download the Malwarebytes Support Tool.
- In your Downloads folder, open the mb-support-x.x.x.xxx.exe file.
- In the User Account Control (UAC) pop-up window, click Yes to continue the installation.
- Run the MBST Support Tool.
- In the left navigation pane of the Malwarebytes Support Tool, click Advanced.
- In the Advanced Options, click only Gather Logs. A status diagram displays the tool is Getting logs from your computer. WARNING: Do Not click the Repair System under Advanced unless requested to by a Malwarebytes support agent or authorized helper.
- A zip file named mbst-grab-results.zip will be saved to the Public desktop, please attach that file in your next reply to this topic. Please do NOT copy and paste.
For the short time between when you post the diagnostic logs, and when your helper weighs in, please take no further self-directed remedial actions that will invalidate the diagnostic logs you will have posted.
Thank you.




Mullvad Browser
in General Software and Security Updates
Posted
Mullvad Browser 13.0.1 has been released. (26-October-2023)
Blog | Changelog | Update: Auto-update or download.