-
Posts
1,095 -
Joined
Content Type
Events
Profiles
Forums
Posts posted by msherwood
-
-
7 minutes ago, ksiemb said:
What does Invision Community update have to do with logging in at Malwarebytes.com ?
It doesn't. @1PW thought it might since your post happened around the time of the update. It's not related. Please hang tight and our entire team is working on the forums update that just happened. We'll get back to you on your question soon.
-
1 minute ago, Firefox said:
Ugh... hope you get the dark theme back soon...
-
8 minutes ago, David H. Lipman said:
Lost the Dark ( Gothic ) Theme ( preferred ), the ability to attach and the ability to change personal avatar.
Also was able to change avatar.
-
5 minutes ago, David H. Lipman said:
Lost the Dark ( Gothic ) Theme ( preferred ), the ability to attach and the ability to change personal avatar.
Also...
What is with the Alphabet Soup of Avatars ?
Dark theme is a known issue and we'll rebuild it as soon as we can.
I just attached both of these using drag-and-drop as well as the "choose files..."
-
1 hour ago, ksiemb said:
What is going on with the login at malwarebytes.com ? It has Employee logon, and then Coming Soon login for users, which I cannot log into, and there is no button to request password reset or anything to help me login. The entire screen has changed format since I previously had use of it !
3 minutes ago, 1PW said:Perhaps the following link will be helpful to you:
Thank you for your patience and understanding.
This is something different as @ksiemb posted before we did the upgrade.
@ksiemb - can you further explain what you're experiencing and where exactly?
-
We've completed the upgrade to Invision Community 4.2! If you come across any issues, please check the Known Issues & Workaround thread or post a new issue here.
-
We are still on track for the Invision Community 4.2 update tomorrow morning (Monday, August 7). We are targeting downtime starting at 8a PDT and this will last ~15-30 minutes as we test and verify the update. We'll post info here once it's been completed and we're fully back online.
-
Closing this thread as it's been resolved.
-
1 hour ago, whereisthesupport said:
This is my experience. I think the complaint is obvious enough.
We have been paying £126/year for 6 licenses:
- Didn't detect the malicious code in a word document - okay, it happens but this has been happening more and more commonly
- I couldn't find where to submit the malicious file to Malwarebytes for processing. None of the suggestions I found by Googling worked.
- I couldn't find where to contact them for support. After a long rabbit hole of following support page after support page I came to a "fill in the form" page with no form and a USA telephone number. My favourite page was this one:https://www.malwarebytes.com/support/business/#question a page which simply says "I have another sales question." and then ends with no explanation.
- I know other malware protection options are cheaper and I've had enough now so just decided to cancel the subscription: Finally found the "My Account" website but I couldn't stop auto-renewal online
- Managed to get the UK contact support telephone number from this page:https://www.malwarebytes.com/business/contact-us/ - the form still doesn't show, but at least the number is good.
- UK support just answered the phone by the guy's name, didn't ask for any security questions just took my subscription number and told me my renewal date and cancelled it. Didn't even ask my name. Doesn't exactly show much in the way of security.
Hi @whereisthesupport. Sorry to hear about your issues. We'd love a chance to make this right. Our Business Support team will be in touch very shortly on this.
-
Hi @rawrabbit. Thanks for posting your concerns and feedback. Please know our Legal team is reviewing your inquiry and will get back to you early next week.
-
UPDATE 6/29/2017 1045 PST: According to information uncovered within Malwarebytes Labs, we have determined that this ransomware variant is coded to erase a unique and randomly generated key that is used to encrypt the MFT (Master File Table). The destruction of the Salsa20 key makes it very unlikely that users can receive a working decryption key – even after paying the attackers ransom demands. For this reason, we warn any infected user who may be considering paying the ransom to beware. We have created a new entry on the Malwarebytes blog with the newly discovered information: EternalPetya and the lost Salsa20 key
UPDATE 6/27/2017 1653 PST: Based on information released by security researchers, a Ukrainian accounting software company called Me Doc pushed an update at around 10:30 GMT this morning, which installed the malware on the “victim zero” system. Then, using a mix of PSExec, WMI, and EternalBlue, it was able to spread to every other computer on the network. Me Doc has claimed that this isn’t the case, however, so we won’t 100 perfect confirm that this was the source of the original infection vector.
At this point, it would be a good idea (if you are running any Me Doc software) to not update said software until they have announced that their servers are clean.
---------------------------------------------------------------------------------------------------------------------------------------------------------------------------------
UPDATE 6/27/2017 1515 PST: Researchers have discovered what might be a “Vaccine” for the current version of the Petya-Esque ransomworm. You can give it a shot and see if it works for you, but keep in mind that basically as soon as the linked article was created, the creators of this attack have likely already modified their source to negate the defense. Good luck!
---------------------------------------------------------------------------------------------------------------------------------------------------------------------------------
UPDATE 6/27/2017 1430 PST: If you’re thinking about paying the ransom for this threat–don’t bother. The e-mail service which hosted the address which victims were instructed to send payment to has closed the account. So, at this point trying to pay the ransom will result in a returned e-mail. Unfortunately, recovering files from payment is no longer possible at the moment, the attackers may provide their victims with alternative forms of payment transactions.---------------------------------------------------------------------------------------------------------------------------------------------------------------------------------
Ringing with echoes of WanaCrypt0r, a new strain of ransomware being called Petya/NotPetya is impacting users around the world, shutting down firms in Ukraine, Britain, and Spain.
Background
Petya, created in July 2016, started off as one of the next-generation ransomware strains that utilizes an MBR (Master Boot Record) locker. In the early days of ransomware, strains that modified the startup of a system were popular, but they had died off for many years. Today, not long after its one year anniversary, Petya has come back with a vengeance and a nasty new distribution method.
As to whether or not this malware is the same Petya that we have dealt with in the past, many other researchers, including our own, claim that the malware is heavily influenced and likely developed by the creators of Petya. This malware has indicators and code that matches previous versions of Petya, but with additional functionality.
We are not going to claim attribution or even confirm what family we are dealing with until more analysis has been completed and more evidence is available. What we can say for sure is that this ransomware uses tactics rarely seen in the wild.
Infection vector
Taking a page out of WannaCry’s book, this new ransomware utilizes the same EternalBlue SMB exploit that was used in the outbreak that occurred more than a month ago. There are also currently reports that this attack uses email spam to distribute infected Office documents in efforts to rapidly spread and distribute the ransomware. This malware also includes the ability to use PSExec on a system it has administrative credentials on, allowing it to execute duplicates of the malware on any system on the network.
However, not all of these reports have been confirmed by Malwarebytes staff, so its true original infection vector beyond SMB exploitation is up in the air. But the combination of the PSExec method with the EternalBlue exploit gives this malware a lot of power in its ability to spread across a network.
Execution
After execution, the ransomware infects the system at a low level, modifying the MBR and presenting the user with the following prompt:

After a reboot, instead of loading into the operating system installed on the computer, the user is faced with a faux Check Disk operation that, instead of actually checking your hard disk for issues, is actually encrypting files! This is done to buy the ransomware more time to encrypt all the relevant files on the system without being stopped by the user.

The MFT (Master File Tree) and the MBR are also encrypted. The MBR is overwritten to display the ransom note, which makes it impossible to boot the system without remediation—meaning users must either pay the culprit or be unable to access their system. The computer will then display a menacing black screen with red lettering listing the ransomware’s purpose and its demands. The attack affects users by encrypting anywhere from a single file to the entire system.

While this situation could have been easily avoided by simply keeping all antivirus database and operating system updates current, the now-infected users must pay $300 in Bitcoins to regain access to their files.
As stated on Twitter by @ydklijnsma, it would appear that the file types being targeted are aimed more toward the programs that developers would use, such as, .vbs, .ova, .vbox, and so on. This makes it appear like target of these attacks are likely businesses and especially firms that specialize in software development.
Unfortunately, unlike WannaCry, Petya does not have a “killswitch” readily available or known.
Zero-hour protection
Malwarebytes detected this ransomware in the zero hour, meaning those that have Malwarebytes Premium or our standalone anti-ransomware technology have been protected from the instant this attack began. Both Malwarebytes business users and consumers users are protected if they are using the latest version of the above products.
We detect this ransomware as either Ransom.Petya or Ransom.Petya.EB
Full protection from this threat can also be achieved by:
- Updating and deploying security software with anti-ransomware capabilities
- Updating and securing operating systems on your network, including checking for any open SMB ports on any Internet-facing systems
- Locking down user accounts from having administrative powers and possibly even removing/shutting down admin systems that might utilize the PSExec method of spreading the malware
- If you are a business owner, making sure your users are aware of this current threat
- Opening emails with a high degree of scrutiny in the near future



We are going to regularly update this post to inform you about new developments with this attack, a deeper look at its spread, and possible motivations/infection methods. In addition, we are currently working on a post that analyzes the malware binary to its core. Expect that shortly.
Thanks for reading and safe surfing!
-
Hi everyone.
If you're experiencing today's issue of Web Protection being off and/or Malwarebytes 3.1.2.1733 not being able to perform a scan, we have pushed Update Package 1.0.1976 to resolve this. In some cases, an additional step of either rebooting the machine or just Malwarebytes is needed.
If you're experiencing a different issue, please check out the Malwarebytes 3 section (here) and/or post a new thread with your issue (here).
Edit: more information on the issue (here).
-
16 minutes ago, AtariBaby said:
Hi
Firstly, I began receiving spam and malware emails to the unique address I've used with malwarebytes in the past. I know this because I use a unique email address for everything I sign up for. I wanted to give you guys a heads up that maybe your internal customer database or your forum email addresses got compromised. You may already be aware. It's possible that my email was harvested from some other means, like someone else's computer I may have been on in the past, but this pretty much never happens.
Secondly, I just wanted to comment that the hurdles in joining this forum were so great that I nearly quit in the signup process, and so I imagine you must be turning away a great many people! The password had to be crazy complex, plus the annoying task of clicking on three pages of streetsigns, plus this, plus that. If this was banking or something I would understand, but just to post on a forum? Honest feedback for you to do with as you please.
Welcome to our community, @AtariBaby. Appreciate the feedback and information.
On your first concern about our customer database and forum email addresses being compromised: at this time we are not aware of any breaches. For your reference, we did experience a breach in Nov 2014 (here) - it was a single server running the forums at that time. We took a precautionary step of issuing password resets to all users. We also moved the hosting of the forums to IPS (who did, and still does, provide the forums software).
Separately and not related to our systems, one way your email could have been obtained is someone who has your email in their address book may have been compromised, the malware then took all of their contacts and then everyone in that address book could start receiving spam emails - sharing as this is a very common way for this to happen.
On your second comment about the sign up process: yeah, it's a few extra steps. It's purposely designed this way to help keep the forums and our community protected. Just as many companies are, we're targeted and some of these extra steps help us keep unwanted elements out of the community.
-
We're super excited to announce availability of an update to both our MB-Check and MB-Clean utilities. For MB-Check, we've updated this to included both support for the latest Malwarebytes 3.1 as well as the ability to automatically collect log files. For MB-Clean, this has also been updated to support the latest Malwarebytes 3.1 as well as some other sweet enhancements.
See above to get the latest versions as well as the detailed changelogs: MB-Check | MB-Clean
-
1 hour ago, GMork said:
Maybe some members have read my last thread about my offering of my MBAM2 or MB3 license for free.
After some time being readable it was hid by the forum administration.
I was informed about that by a private message from the forum administrator @msherwood and he said it wouldn't be allowed to offer a license in such way.
But he offered a refund of my license. Therefore I sent a request to Cleverbridge and just before I got the confirmation, that the refund has been processed successfully.
Despite of all my troubles with Malwarebytes' programs while the last months I regard it as a point of fairness to publish in a new thread such fair business practices by Malwarebytes - that's absolutely not usual nowadays.
Nevertheless I end the contact with Malwarebytes ,their products and the forum finally.
Therefore I don't need anylonger an account here and I request the administration or moderation to delete my whole account on forums.malwarebytes - I do it always in that way leaving a forum finally.
A short confirmation from the administration or moderation about the deletion in a reply to this thread would be nice.
I remain with the wish for all users of Malwarebytes products, that they can use them in future without the current troubles in a safer, more stable and reliable way and with the wish for Malwarebytes, that they will be able to develop a MB3 with the same safety, stability and reliability as it has had MBAM2 while several years.
Take care and farewell!
Gert
P.S. That this is my 100th post isn't any intention by me, it's really accidentally.
Per your request, we've removed your account.
-
Hi everyone,
Here at Malwarebytes, your security is always our top priority.
With the new features added in our forum software provider’s release (here), we will be implementing an enhanced password requirement for the Malwarebytes Forums.This change will affect both new users signing up to our forums and any users who update their password after today. We encourage all to adhere to this new policy.
Passwords will be required to be “Strong” and there will be a password meter to guide you to this strength level.
Per IPS, “The strength of a password is calculated using an algorithm which rewards longer passwords with a mix of letters, numbers and symbols, and subtracts points for using consecutive or sequential characters.” A “Strong” password is “a mixture of upper and lowercase characters, numbers and special characters.”
Additionally, here are some password tips: “8 or more characters, Mixture of letters and numbers, Mixture of upper and lowercase, Special characters and Non-dictionary words”.

Here are a few examples of the new password meter and requirements in action:

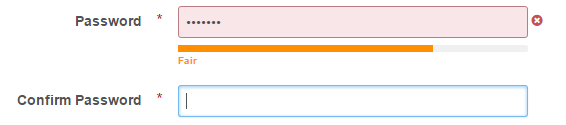
Although not required, we encourage all users to obtain the highest password strength of “Very Strong”as shown in this example:

In addition to having a strong password for your Malwarebytes Forums account, we encourage strong passwords for all of your accounts. You can learn more about good password habits at https://blog.malwarebytes.com/101/2015/01/the-password-and-you/.
-
We just pushed a new version (8.1.3): https://forums.malwarebytes.com/topic/199226-junkware-removal-tool-jrt-813-released/
Direct: https://downloads.malwarebytes.com/file/jrt/
@nukecad - let us know how it's working for you!
-
We've got the build updated and it's with QA now. We're targeting the deployment of this new build within 24 hours.
Again, if you're seeing this issue simply reboot your machine.
-
We've figured this out. We're terminating "fontdrvhost" and that's causing the issues you're seeing.
How to fix: reboot your system.

We're working on an updated build and we'll publish that ASAP. Thanks again for the bug report!
-
Hey @nukecad. We're still troubleshooting this one. We'll be in touch soon.
-
11 minutes ago, Firefox said:
You guys are probably aware, but nice to see the forum back up... it was down for several hours with messages like:
503 Service Temporarily Unavailable
504 Gateway Time-out
You're too fast!
-
As you may have noticed, the forums was down for a few hours today. Just as many other sites and services around the net, our forums provider (Invision Power Services) was also affected by the Amazon AWS outage. Read more about the AWS outage and see AWS Service Health Dashboard here.
We're back in business!
-
6 minutes ago, David H. Lipman said:
- Firefox 51+
- Black ( Dark Wide ) or what I call it, Gothic.
- 1920 x 1080
Got it, thanks.
-
@David H. Lipman from IPS...
- Which theme is the user using?
- What screen resolution are they viewing the site with?
- Which browser are they using?














Malwarebytes.com Login
in General Chat
Posted
What site / URL were you previously using? The screenshot you shared is from our new Support site and we do not have logins enabled for customers.